This article discusses a new cyber attack campaign involving newly registered domains (NRDs) that utilize an innovative domain generation algorithm (DGA) variant designed to evade detection. The attack has redirected users to potentially harmful Android application sites via manipulated IPs. Key findings reveal the use of typo DGA domains, indicating a sophisticated strategy aimed at avoid detection by security systems. Affected: Android applications, cyber security sector
Keypoints :
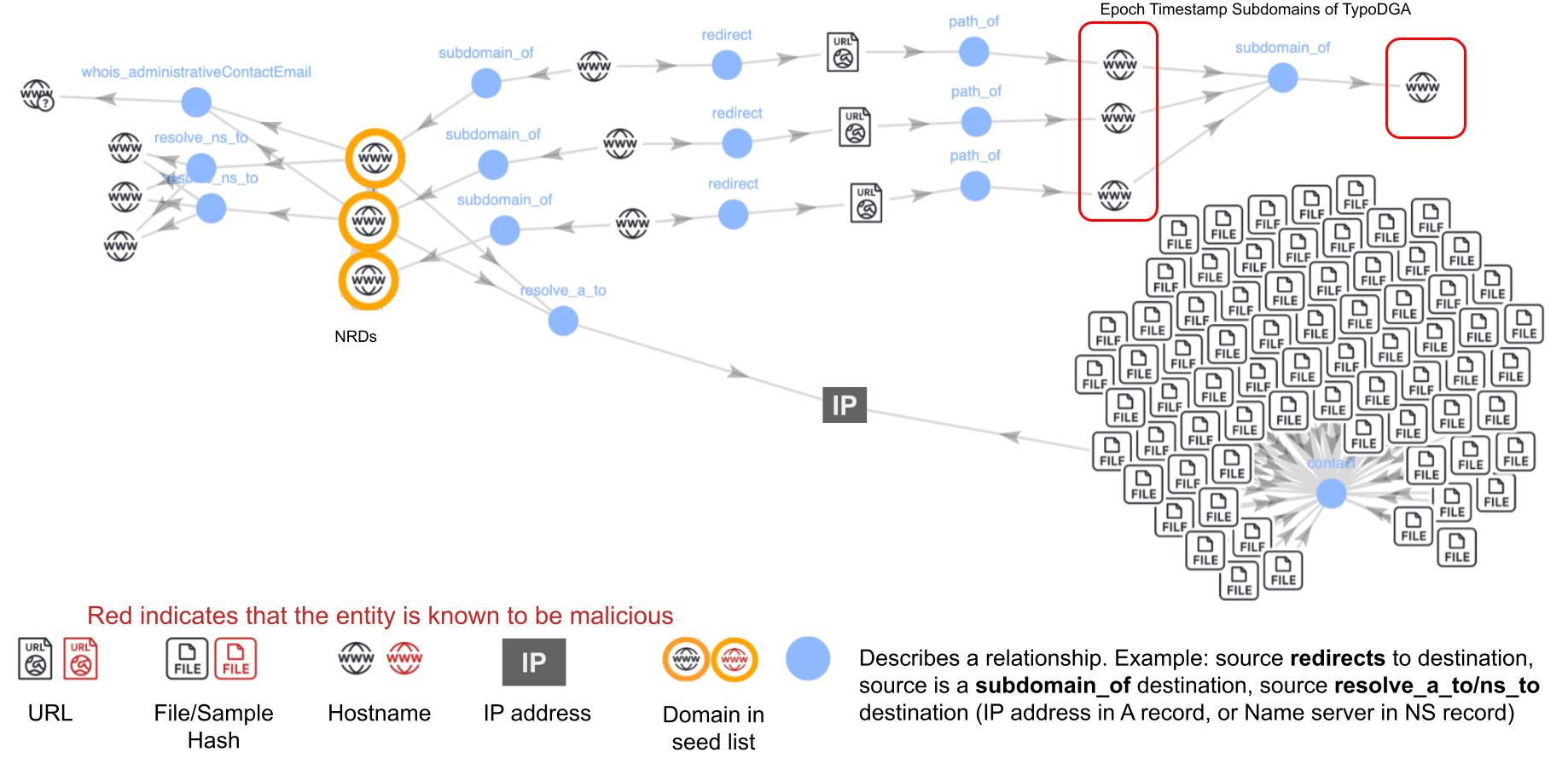
- Discover of a campaign using 6,057 newly registered domains (NRDs) for malicious purposes.
- Domains resemble those generated by dictionary-based domain generation algorithms (DGAs).
- Campaign redirects lead to advertisements of potentially unwanted Android applications.
- 96% of files contacting the malicious IP were identified as malicious.
- Identified 444,898 NRDs belonging to the same actor, redirecting to 178 typo DGA-like domains.
- Typo DGAs show a new pattern combining dictionary words with typographical errors.
- Advanced URL Filtering and Advanced DNS Security can identify the malicious domains and URLs.
- Encouragement for potentially compromised individuals to contact the Unit 42 Incident Response team.
MITRE Techniques :
- Domain Generation Algorithm (T1071) – The attacker uses newly registered domains to create a large number of domain names designed to evade detection.
- Application Layer Protocol – The campaign leveraged HTTP/S protocols for the redirection to potentially unwanted applications.
Indicator of Compromise :
- [Domain] zgi8ij[.]us
- [Domain] ord8w1[.]us
- [Domain] mg77bi[.]us
- [Domain] wnsukh[.]us
- [Domain] y1ly6n[.]us
- [IP Address] 91.195.240[.]123
- [Domain] pictidentifyive[.]pro
- [Domain] gratsuccessfic[.]pro
Full Story: https://unit42.paloaltonetworks.com/typo-domain-generation-algorithms/
Views: 29