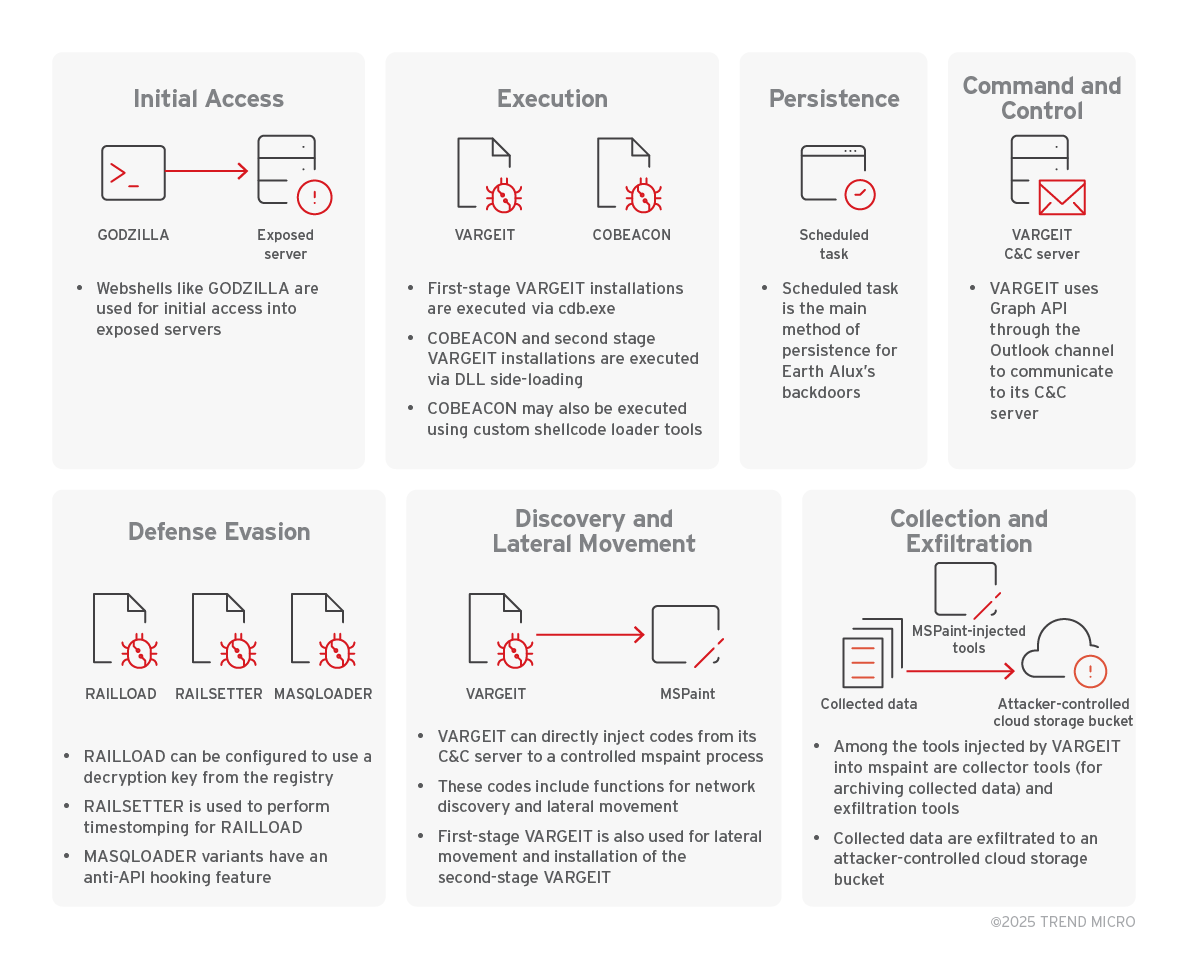
The cyberespionage group Earth Alux, linked to China, employs sophisticated techniques to target critical sectors in the Asia-Pacific (APAC) and Latin America. Their primary backdoor, VARGEIT, facilitates stealthy data exfiltration, affecting vital industries including government, technology, and logistics. To mitigate the risks of such cyber threats, organizations should adopt proactive security measures. Affected: government, technology, logistics, manufacturing, telecommunications, IT services, retail
Keypoints :
- Earth Alux is linked to China and executes cyberespionage attacks mainly in the APAC and Latin American regions.
- The group’s primary tool for infiltration is the VARGEIT backdoor, which allows data exfiltration while remaining undetected.
- Key sectors targeted include government, technology, logistics, manufacturing, telecommunications, IT services, and retail.
- Regular system updates and monitoring are crucial to prevent infiltration by such advanced persistent threat groups.
- Testing of tools like RAILLOAD and RAILSETTER indicates Earth Alux’s commitment to improving its evasion capabilities.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: Earth Alux uses HTTP and HTTPS communication channels to exfiltrate data.
- T1059.001 – Command and Scripting Interpreter: COBEACON and VARGEIT run scripts to execute commands stealthily.
- T1064 – Scripting: The group employs PowerShell and other scripting tools for automation and execution of malicious payloads.
- T1547.001 – Boot or Logon Autostart Execution: RAILSETTER is utilized for persistence by configuring scheduled tasks.
- T1203 – Exploitation for Client Execution: Earth Alux exploits vulnerable services on exposed servers for initial access.
Indicator of Compromise :
- [Domain] baidu.com
- [Domain] example[. ]com
- [IP Address] 192.168.1.1
- [Email Address] attacker@example[. ]com
- [Hash] 56e81fceae51e65e40e5b3d8f3dcd1 e66
Full Story: https://www.trendmicro.com/en_us/research/25/c/the-espionage-toolkit-of-earth-alux.html