Introduction
Pikabot is a malware loader that originally emerged in early 2023. Over the past year, ThreatLabz has been tracking the development of Pikabot and its modus operandi. There was a significant increase in usage of Pikabot in the second half of 2023, following the FBI-led takedown of Qakbot. This was likely the result of a BlackBasta ransomware affiliate replacing Qakbot with Pikabot for initial access. However, Pikabot ceased activity shortly after Christmas 2023, with its version number being 1.1.19 at that time.
In recent campaigns, which started in February 2024, Pikabot reemerged with significant changes in its code base and structure. Although it appears to be in a new development cycle and testing phase, the developers have reduced the complexity of the code by removing advanced obfuscation techniques and changing the network communications.
Key Takeaways
- Pikabot is a malware loader that was first observed in early 2023 and became very active following the takedown of Qakbot in August 2023.
- In December 2023, Pikabot activity ceased, possibly as a result of a new version of Qakbot that emerged. In February 2024, a new version of Pikabot was released with significant changes.
- Previous versions of Pikabot used advanced string encryption techniques, which have been replaced with simpler algorithms.
- Pikabot now stores all configuration elements in a single memory block, similar to Qakbot. In prior versions, Pikabot decrypted necessary configuration elements only when required.
- Pikabot continues to use HTTP for command-and-control, but its network protocol has changed, including the network command IDs and the encryption algorithms.
Technical Analysis
As covered in our previous technical analysis of Pikabot, the malware consists of two components: a loader and a core module. The core module is responsible for executing commands and injecting payloads from a command-and-control server. The malware uses a code injector to decrypt and inject the core module. It employs various anti-analysis techniques and string obfuscation. Pikabot uses similar distribution methods, campaigns, and behaviors as Qakbot. The malware acts as a backdoor, allowing the attacker to control the infected system and distribute other malicious payloads such as Cobalt Strike.
In the following sections, we will describe the latest Pikabot variant, including its capabilities and notable changes compared to previous versions. The analysis was performed on Pikabot binaries with version 1.8.32.
Anti-analysis techniques
As with previous versions of Pikabot, this variant employs a series of different anti-analysis techniques to make the analysis more time-consuming. It should be noted that none of the methods below presents any significant advanced capabilities. Furthermore, Pikabot used a series of more advanced detection features in its loader component in previous versions of the malware.
Strings encryption
The most notable change is the string obfuscation. In previous versions of Pikabot, each string was obfuscated by combining the RC4 algorithm with AES-CBC. This method was highly effective in preventing analysis, particularly when it came to automated configuration extraction. To successfully analyze Pikabot, an analyst would need to detect not only the encrypted string but also its unique RC4 key. Additionally, they would need to extract the AES key and initialization vector, which are unique to each Pikabot payload.It should be noted that the approach the Pikabot malware developers followed is similar to the ADVobfuscator.
In the latest version of Pikabot, the majority of the strings are either constructed by retrieving each character and pushing it onto the stack (Figure 1) or, in some rare cases, a few strings are still encrypted using the RC4 algorithm only.
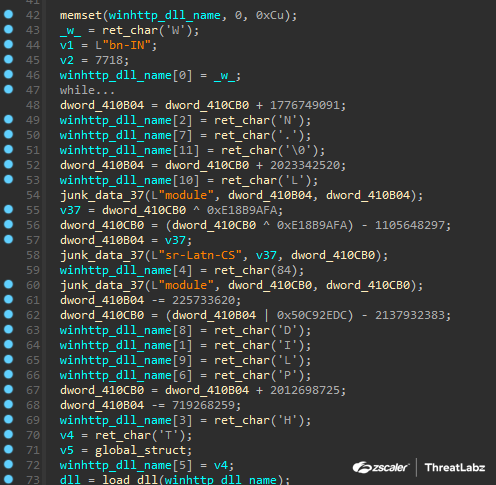
Figure 1. String stack construction
Junk instructions
This anti-analysis technique was also implemented in previous versions of Pikabot. Pikabot inserts junk code between valid instructions. The junk code is either inlined in the function or a call is made to a function, which contains the junk code (Figure 2).
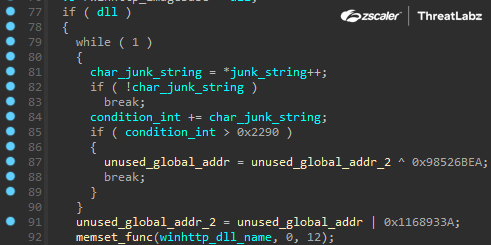
Figure 2. Junk code
Anti-debug methods
Pikabot uses two methods to detect a debugging session. They are:
- Reading the BeingDebugged flag from the PEB (Process Environment Block).
- Calling the Microsoft Windows API function CheckRemoteDebuggerPresent.
Pikabot constantly performs the debugging checks above in certain parts of its code. For example, when it (en/de)codes network data or when it makes a request to receive a network command.
Anti-sandbox evasion
In addition to the anti-debugging checks above, Pikabot uses the following methods to evade security products and sandboxes:
- Pikabot utilizes native Windows API calls.
- Pikabot delays code execution at different stages of its code. The timer is randomly generated each time.
- Pikabot dynamically resolves all required Windows API functions via API hashing.
A Python representation of the algorithm is available below.
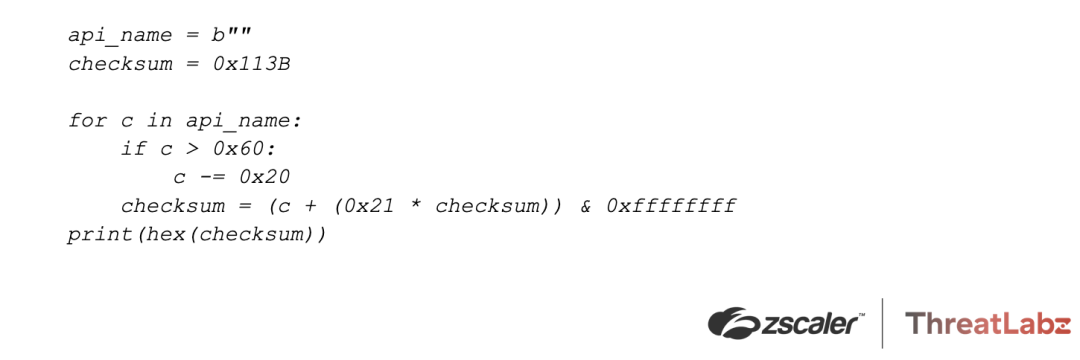
Language detection
Identical to previous versions, Pikabot stops execution if the operating system’s language is any of the following:
- Russian (Russia)
- Ukrainian (Ukraine)
This is likely an indication that the threat actors behind Pikabot are Russian-speaking and may reside in Ukraine and/or Russia. The language check reduces the chance of law enforcement action and potential criminal prosecution in those regions.
Bot initialization phase
Unlike previous versions, this version of Pikabot stores all settings and information in a single structure at a global address (similar to Qakbot). The analyzed structure is shown below. For brevity, we redacted non-important items of the structure (such as Windows API names).
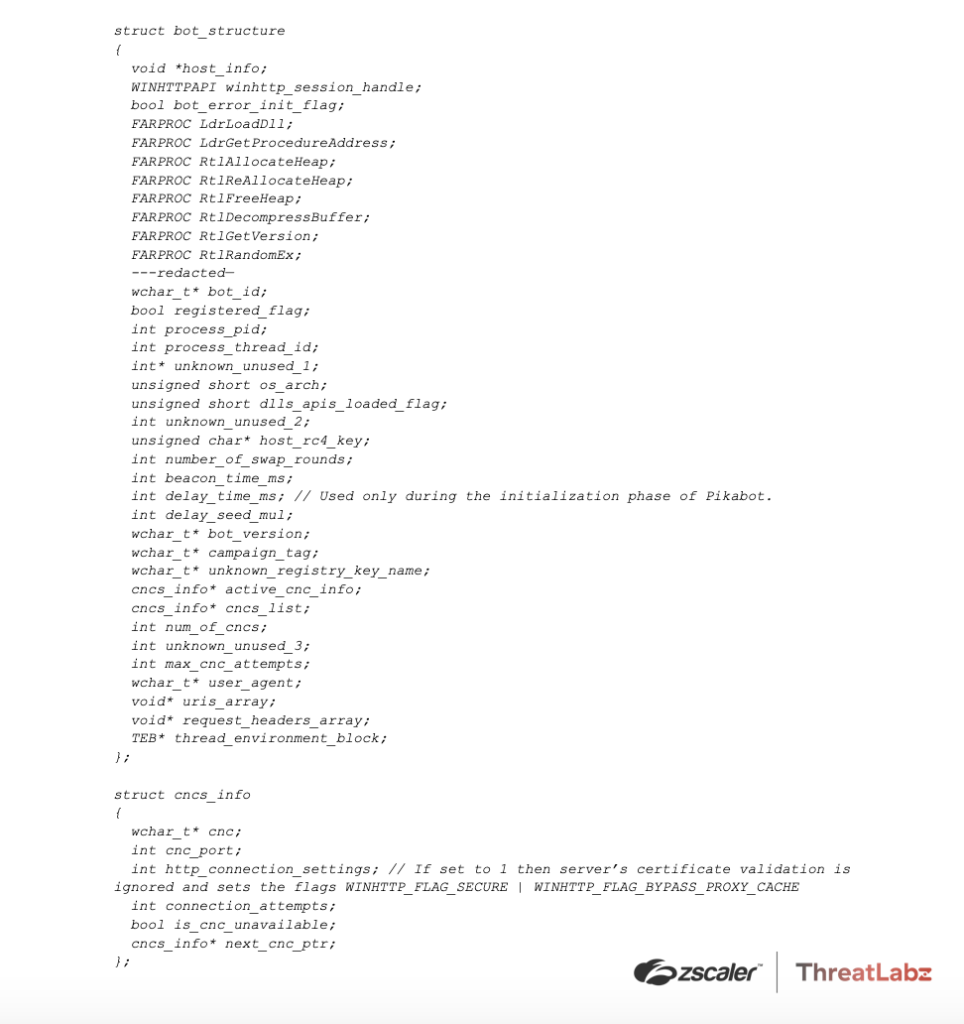
Bot configuration
The latest version of Pikabot stores its entire configuration in plaintext in one address. This is a significant drawback since in previous versions, Pikabot decrypted each required element at runtime and only when required. In addition, many of the configuration elements (e.g. command-and-control URIs) were randomized.
ANALYST NOTE: Despite their randomization, all configuration elements were valid on the server-side. If a bot sent incorrect information, then it would get rejected/banned by the command-and-control server.
The configuration structure is the following:
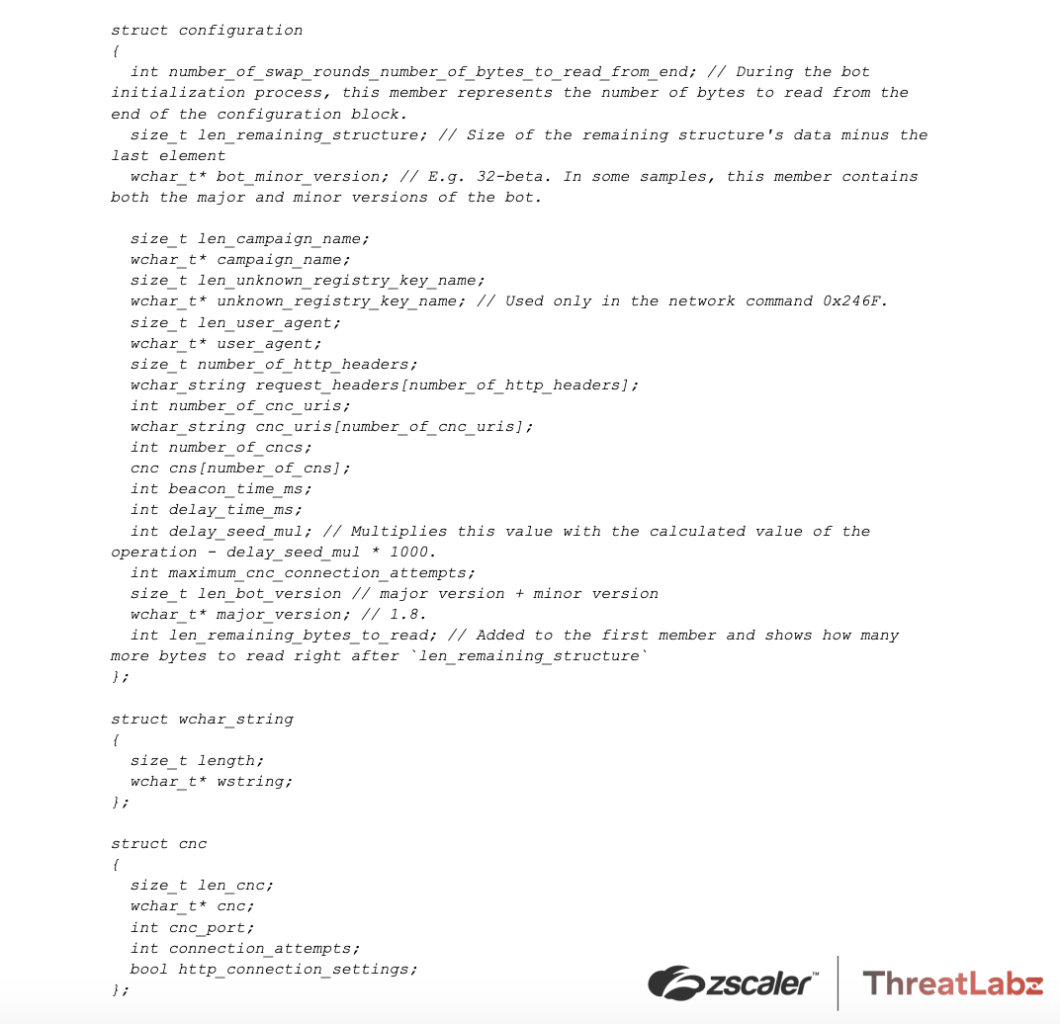
Once Pikabot parses the plaintext configuration, it erases it by setting all bytes to zero. We assess that this is an anti-dumping method to avoid automating the extraction of the configuration.
Lastly, Pikabot loads any remaining required Windows API functions and generates a bot identifier for the compromised host. The algorithm is similar to previous versions and can be reproduced with the following Python code.
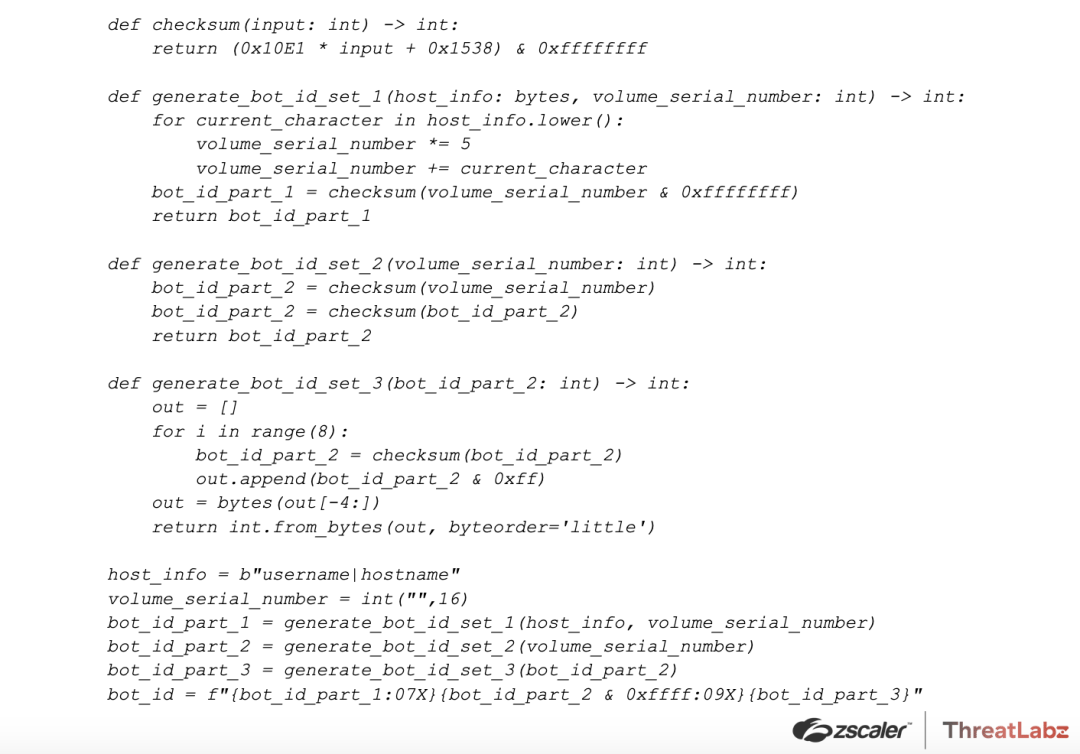
ANALYST NOTE: In some samples, Pikabot does not read the volume serial number due to a bug in their code that causes a failure when calling GetVolumeInformationW.
Network communications
Pikabot contacts the command-and-control server to request and receive network commands. In this version, the network protocol has considerably changed. Pikabot starts by registering the compromised host to its server.
First, Pikabot collects information from the compromised host, such as:
- Monitor’s display settings
- Windows version
- Hostname/username and operating system’s memory size
- Beacon and delay settings
- Process information such as the process ID, parent process ID and number of threads (see the description of network command 0x985 for a comprehensive list).
- Bot’s version and campaign name
- Name of the domain controller
Then Pikabot appends the following information to the registration packet:
- 32-bytes network RC4 key (unique per host), which remains the same for the session. In previous versions, Pikabot was using AES-CBC with a random key/IV per request.
- Unknown registry key name. We observed it used only in the network command with ID 0x246F.
- Number of swap rounds used for encoding the data. This remains the same for the rest of the session.
Next, Pikabot encrypts the data using the RC4 algorithm, encodes the encrypted output, picks a random URI from its list, and sends the data with a POST request to the command-and-control server.
The encoding involves bytes swapping for N times, where N is a randomly generated number in the range 0-25.
ANALYST NOTE: Despite the fact that a round number is set in the configuration (see the configuration structure), this value is ignored and Pikabot replaces it with a random value. Moreover, Pikabot has completely removed the JSON format in its network packets and inserts everything in a raw format.
If the bot registration is successful, Pikabot starts an infinite loop to request and execute commands.
Each incoming network command (with the exception of network command with ID 0x164) has a task ID that is placed at the start of the (decrypted) packet as a QWORD value. In Table 1 below, we list the identified network commands along with a description of their functionality.
| Command ID | Description |
|---|---|
| 0x164 | Requests command from command-and-control server. The packet includes the command ID, size of bot ID, and the bot ID. The server replies with the same command ID if there is no network command for the bot to execute. |
| 0x555 | Reports the output of the executed network command to the command-and-control server. |
| 0x1291 | Registers the bot. An unknown integer value (0x1687) is appended in the packet at offset 8. |
| 0x1FED | Updates beacon time. |
| 0x1A5A | Terminates/kills the bot. |
| 0x2672 | Not implemented |
| 0x246F | Writes a file to disk and adds registry data using the value name specified in the configuration (unknown_registry_key_name). |
| 0xACB | Executes the system command and sends back the output. Includes the error code 0x1B3 if there is no output. |
| 0x36C | Injects the code of a downloaded PE file. The target process information is specified in the network packet. |
| 0x792 | Injects the code of a downloaded shellcode. The target process information is specified in the network packet. |
| 0x359 | Executes system command and sends back the output. Note: Same as 0xACB but does not send the error code. |
| 0x3A6 | Executes system command and sends back the output. Note: Same as 0xACB but does not send the error code. |
| 0x240 | Executes system command and sends back the output. Note: Same as 0xACB but does not send the error code. |
| 0x985 | Collects processes’ information. These are:
|
| 0x982 | Not implemented |
Table 1. Pikabot Network Commands
Conclusion
Despite its recent inactivity, Pikabot continues to pose a significant cyber threat and is in constant development. However, the developers have decided to take a different approach and decrease the complexity level of Pikabot’s code by removing advanced obfuscation features. Moreover, based on our code analysis, it appears that certain features and network commands have not been implemented yet and are still a work in progress.
Zscaler ThreatLabz continues to track this threat and add detections to protect our customers.
Indicators Of Compromise (IOCs)
SHA256 | Description |
|---|---|
555687ca3149e23ee980a3acf578e0572da556cf34c87aecf48596834d6b496f | Pikabot sample (version 1.8.32-beta) |
ca5fb5814ec62c8f04936740aabe2664b3c7d036203afbd8425cd67cf1f4b79d | Pikabot sample (version 1.8.32-beta) |
IOC | Description |
|---|---|
104.129.55[.]103:2224 | Command-and-Control server |
178.18.246[.]136:2078 | Command-and-Control server |
158.220.80[.]167:2967 | Command-and-Control server |
104.129.55[.]104:2223 | Command-and-Control server |
23.226.138[.]161:5242 | Command-and-Control server |
37.60.242[.]85:9785 | Command-and-Control server |
23.226.138[.]143:2083 | Command-and-Control server |
37.60.242[.]86:2967 | Command-and-Control server |
85.239.243[.]155:5000 | Command-and-Control server |
158.220.80[.]157:9785 | Command-and-Control server |
65.20.66[.]218:5938 | Command-and-Control server |
95.179.191[.]137:5938 | Command-and-Control server |
139.84.237[.]229:2967 | Command-and-Control server |
Zscaler Coverage
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators related to Pikabot at various levels with the following threat names:
- Win32.Trojan.PikaBot
- Win32.Downloader.PikaBot
Source: Original Post
“An interesting youtube video that may be related to the article above”
Views: 0