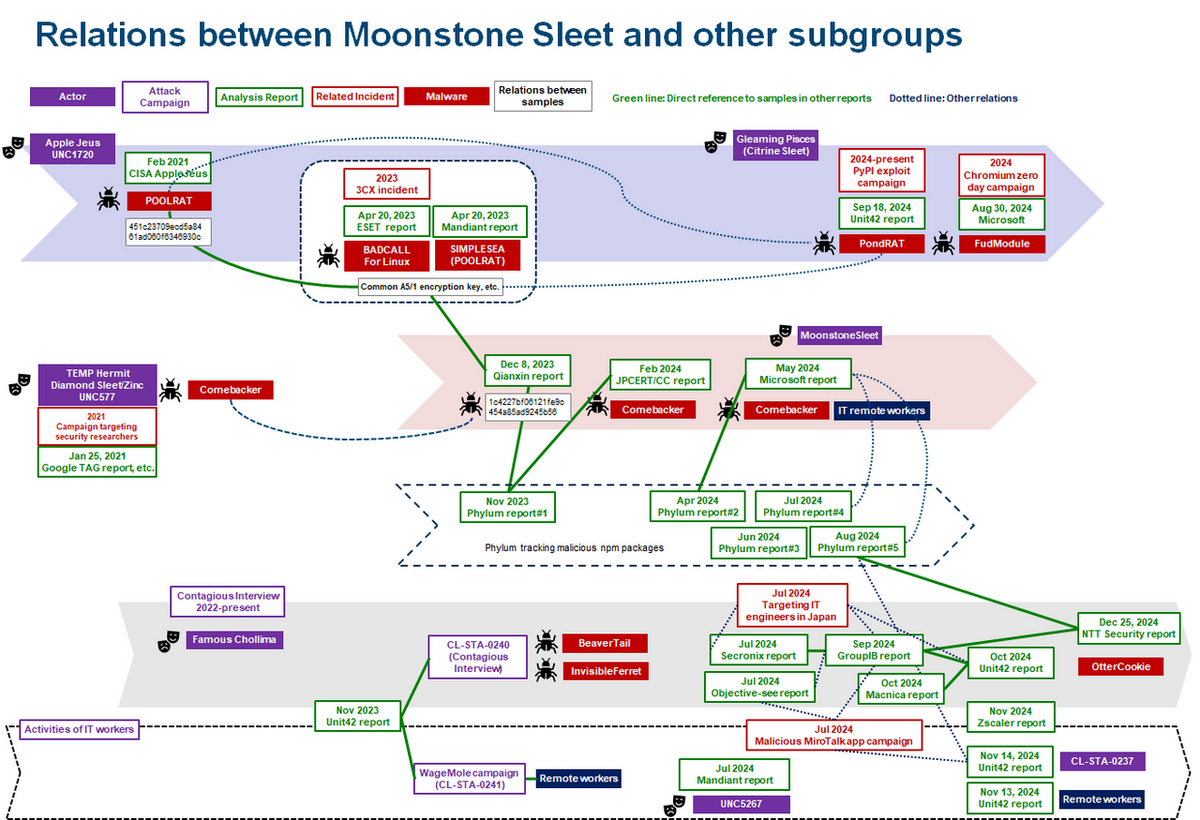
The article discusses the evolution of the Lazarus group, indicating that it has now transformed into a collection of subgroups rather than a single entity. It emphasizes the importance of understanding these subgroups, their tactics, and their individual characteristics for effective cyber defense strategies. Affected: Japan, cryptocurrency sector, defense industry, aviation industry
Keypoints :
- The term “Lazarus” has evolved from a singular APT group to multiple subgroups.
- Various labels exist for campaigns, attack groups, and subgroups, causing confusion in threat landscape analysis.
- Overlaps in tactics, techniques, and procedures (TTPs) among Lazarus subgroups complicate attribution and analysis.
- Identifying subgroups can improve specific security alerts and countermeasures for targeted sectors.
- Active cyber defense measures are necessary for Japan to combat activities from Lazarus subgroups effectively.
- Emerging actors like Bureau325 exhibit similar TTPs to Lazarus subgroups but operate independently of traditional group structures.
MITRE Techniques :
- T1071 – Application Layer Protocol: Lazarus groups utilize common application protocols for command and control.
- T1046 – Network Service Discovery: Several subgroups show overlap in identifying network services in their reconnaissance phases.
- T1203 – Exploitation for Client Execution: Attack campaigns utilize malicious npm and Python packages for initial access.
- T1193 – Spear Phishing Link: Groups like Moonstone Sleet use social networking to lure targets.
- T1485 – Data Destruction: Certain subgroups target sensitive industries, sometimes involving ransomware attacks.
Indicator of Compromise :
- [Domain] example.com (malicious domain used for phishing)
- [URL] http://malicious-package.com/malware (used to lure victims to download malicious content)
- [Email Address] attacker@example.com (used for spear phishing)
- [IP Address] 192.168.1.10 (known IP linked with C2 infrastructure)
- [Hash] 7c6a180b36896a351a108d3f7e1e2dde (MD5 hash associated with malicious executable)
Full Story: https://blogs.jpcert.or.jp/en/2025/03/classifying-lazaruss-subgroup.html