Xloader is a sophisticated malware family that targets various applications to steal sensitive information and deploy additional payloads. With its evolving obfuscation techniques and encryption layers, Xloader complicates detection and analysis efforts. This article provides a detailed examination of the latest versions (6 and 7) of Xloader, focusing on its behavior, persistence mechanisms, and advanced obfuscation methods. Affected: Xloader, Formbook
Keypoints :
- Xloader is a successor to Formbook, rebranded in early 2020.
- It operates on a Malware-as-a-Service (MaaS) model, offering command-and-control (C2) infrastructure to cybercriminals.
- Xloader targets web browsers, email clients, and FTP applications for data theft.
- Versions 6 and 7 feature enhanced obfuscation and encryption to evade detection.
- New techniques include runtime code encryption and NTDLL hook evasion.
- Xloader establishes persistence through registry modifications and executable copies in user directories.
- It employs process injection methods to evade security software.
- Obfuscation techniques have evolved significantly from previous versions, complicating reverse engineering.
MITRE Techniques :
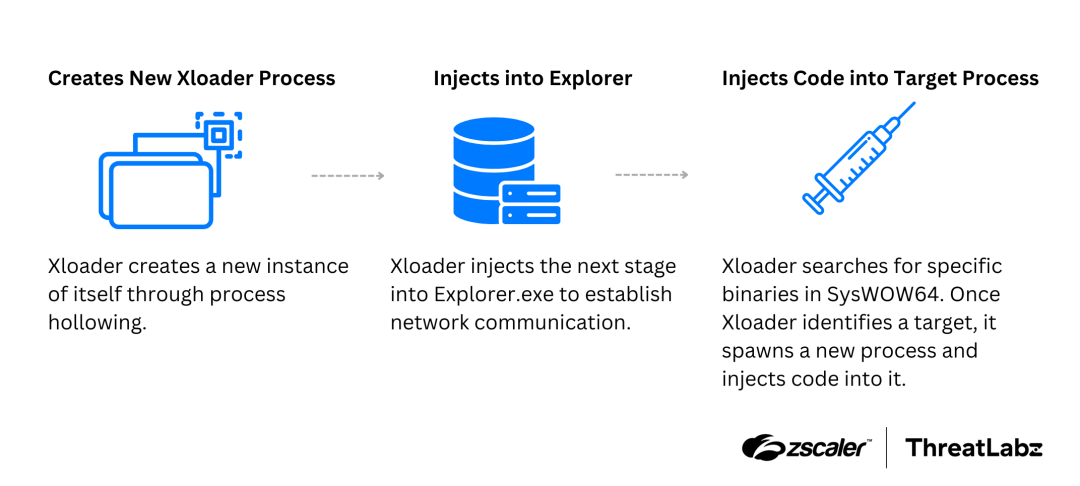
- TA0002: Execution – Xloader executes its payload through process hollowing and code injection into legitimate processes.
- TA0003: Persistence – It maintains persistence by copying itself to the %APPDATA% directory and modifying registry keys.
- TA0040: Impact – Xloader steals sensitive information from targeted applications.
- TA0042: Resource Development – The malware uses a MaaS model to provide infrastructure for other cybercriminals.
- TA0005: Defense Evasion – Xloader employs obfuscation techniques and process injection to evade detection.
Indicator of Compromise :
- [file name] 66ebf028ab0f226b6e4c6b17cec00102b1255a4e59b6ae7b32b062a903135cc9
- [file name] 88909cd27a422da91a651e87f493d16beff1f0e03adcc035f2835a2a25e871e7
- [file name] 4ad101eef336dc2467ffaf584b272aa82f26711bfba4e2e29e8ad7c6d62bc6ae
- [file name] 362207c53645346df6f36cf3f7792e5fc4655895b35a6e3477e218e0e0007be9
- [file name] b1fb20d5857d1ca65dbacd6cb100dc2d7da8eb7ce54d4faeebafb2bbb212beca
- Check the article for all found IoCs.
Full Research: https://www.zscaler.com/blogs/security-research/technical-analysis-xloader-versions-6-and-7-part-1