
Summary: RiseLoader is a newly identified malware loader that utilizes a custom TCP-based protocol similar to its predecessor, RisePro, but focuses on downloading and executing secondary payloads. Its emergence follows the discontinuation of RisePro, suggesting a potential link between the two malware families and their threat actors.
Threat Actor: Unknown | RiseLoader
Victim: Various Cryptocurrency Users | cryptocurrency users
Key Point :
- RiseLoader was first observed in October 2024 and is designed to download and execute additional malware payloads.
- The malware employs VMProtect for code obfuscation and includes anti-analysis techniques aimed at evading detection.
- It communicates with command and control (C2) servers using a custom TCP-based binary protocol, sharing similarities with RisePro.
- RiseLoader targets cryptocurrency-related applications and browser extensions, gathering sensitive information for potential exploitation.
- Indicators of compromise (IOCs) include various SHA256 hashes of packed samples and dropped payloads associated with known malware families.
Introduction
In October 2024, Zscaler ThreatLabz came across malware samples that use a network communication protocol that is similar to RisePro. However, unlike RisePro which has primarily been used for information stealing, this new malware specializes in downloading and executing second-stage payloads. Due its distinctive focus and similarities with RisePro’s communication protocol, we named this new malware family RiseLoader. RiseLoader’s emergence is interesting, as the threat actor selling RisePro announced in June 2024 on Telegram that its development was discontinued. Based on these factors, ThreatLabz assesses with moderate confidence that the threat group behind RisePro and PrivateLoader is also behind RiseLoader.
In this blog, we explore RiseLoader’s TCP-based binary protocol, and highlight the similarities between RiseLoader and RisePro.
Key Takeaways
- RiseLoader is a new malware loader family that was first observed in October 2024.
- The malware implements a custom TCP-based binary network protocol that is similar to RisePro.
- Many RiseLoader samples have used VMProtect to obfuscate the malware’s code.
- RiseLoader has been observed dropping malware families including Vidar, Lumma Stealer, XMRig, and Socks5Systemz – similar to those distributed by PrivateLoader.
- RiseLoader collects information about installed applications and browser extensions related to cryptocurrency.
Technical Analysis
The following sections describe some of the features in RiseLoader.
Anti-analysis techniques
Most of the RiseLoader samples analyzed by ThreaLabz are packed with VMProtect. In addition, the malware obfuscates important strings. For example, all RiseLoader samples included the following strings related to malware analysis and debugging:
ollydbg.exeprocesshacker.exetcpview.exefilemon.exeprocmon.exeregmon.exeprocexp.exeida.exeida64.exebinaryninja.exeimmunitydebugger.exewireshark.exedumpcap.exehookexplorer.exeimportrec.exepetools.exelordpe.exesysinspector.exeproc_analyzer.exesysanalyzer.exesniff_hit.exewindbg.exejoeboxcontrol.exejoeboxserver.exeapimonitor.exeapimonitor-x86.exeapimonitor-x64.exex32dbg.exex64dbg.exex96dbg.execheatengine.exescylla.execharles.execheatengine-x86_64.exereclass.net.exe
These strings are defined in a global array, but are not used during execution. This may indicate that anti-analysis features are currently in development and will potentially be implemented in future versions.
Note that RiseLoader does not currently use stack-based string obfuscation, which is present in RisePro and PrivateLoader.
Behavioral analysis
The malware starts by creating a mutex using hardcoded strings for the name. The mutex name will be a combination of three strings such as: winrar8PROMEMEKGAmaV3_2_8. The mutex is formed from a prefix (winrar8), a campaign_id value (PROMEMEKG), and a hardcoded suffix (AmaV3_2_8). If the mutex exists, RiseLoader will terminate. Samples analyzed by ThreatLabz have lacked a persistence mechanism, although this may be a configurable parameter (similar to other malware loaders).
Next, RiseLoader randomly selects a C2 server from a hardcoded list and opens a TCP connection. This process is repeated up to 10 times until a connection is established. If unsuccessful, RiseLoader terminates. Upon successful communication with the C2 server, a new thread is launched to continuously check for commands, process them, and send system information as requested. Additionally, another thread handles the PAYLOADS data from the C2 server, creating a randomly generated folder in the user’s temporary directory to process each payload. This thread also creates an infection marker by creating a registry key under certain conditions and prepares the arguments and delays for each payload.
Finally, a new thread is created to download and execute each payload from URLs provided by the C2 server using libcurl. DLL files are launched with rundll32, while executables are started by creating a new process. After all payloads are downloaded and executed, RiseLoader terminates.
Network communication
After establishing the TCP three-way handshake with the C2 server, RiseLoader expects the server to respond with a message containing XOR keys used for subsequent communications. If the server does not send this message within a 10-second timeout, the malware will attempt to “wake up” the server by sending a KEEPALIVE message. If the server is online, it will respond with a KEEPALIVE_RES message, and the malware will reset its timeout. If the server does not respond, the malware will either attempt to reconnect or close the connection, and call ExitProcess after 10 failed attempts.
After receiving the XOR keys, the malware sends a campaign_id and other information to the server, then waits for the PAYLOADS command. The server can close the connection at any time without notifying the client. Additionally, a SEND_SHUTDOWN command will immediately terminate the malware. The server periodically sends KEEPALIVE messages to ensure continuous communication. If the PAYLOADS command is received, RiseLoader processes the packet and sends either an SL_TASKS_EXECUTED or PL_TASKS_EXECUTED message with the task information. Once the task commands are received, the server closes the connection. The message types exchanged in both directions share a common structure, as defined below:
struct message {
uint32_t magic_bytes; // Hardcoded to 0x00020001
uint32_t data_size;
uint32_t message_type;
byte data[data_size];
}The magic_bytes field may represent a protocol version (i.e., version 1.0.2.0 in little endian byte format), although it is too early to determine the value’s exact meaning since this malware family is new.
Not all messages contain data; for these, the data_size will be zero. For messages that contain data, the structure varies. Some messages use a UTF-8 encoded JSON string, while others, like the SET_XORKEYS and SEND_ID message types, use a byte structure.
Throughout the communication process, the data field will be encoded using one of the XOR keys defined by the C2 server in the SET_XORKEYS message.
The RiseLoader message types are shown in the following table:
|
Message Type |
Message Value |
Description and Payload |
Source |
|---|---|---|---|
|
|
|
Sends information related to cryptocurrency websites, wallets, and web browser extensions. |
Sent by the client. |
|
|
|
Sends information related to the victim’s machine in a JSON format:
|
Sent by the client. |
|
|
|
Sends the |
Sent by the client. |
|
|
|
Sends the |
Sent by the client. |
|
|
|
Sends a list of task IDs, which were downloaded and executed successfully. This message type is used only for the payload URLs that were included in the JSON keys |
Sent by the client. |
|
|
|
Sends a list of task IDs, which were downloaded and executed successfully. This message type is used for the payload URLs that were included in the JSON key |
Sent by the client. |
|
|
|
The C2 server provides encryption keys that are used for subsequent messages. The first byte encodes message payloads from the infected system and the second byte decodes message payloads coming from the C2 server. |
Sent by the server. |
|
|
|
The C2 server sends a new |
Sent by the server. |
|
|
|
Terminates execution. |
Sent by the server. |
|
|
|
Forces sending a |
Sent by the server. |
|
|
|
The C2 server sends a structure with several payloads to download and execute on the victim’s system in a JSON format. There are three different arrays for payloads:
In addition, the |
Sent by the server. |
|
|
|
Requests a response from |
Sent by both the client and the server. |
|
|
|
The response to the |
Sent by both the client and the server. |
Table 1: RiseLoader message types exchanged between the client and the server.
The figure below shows a high-level view of RiseLoader’s network communication protocol.
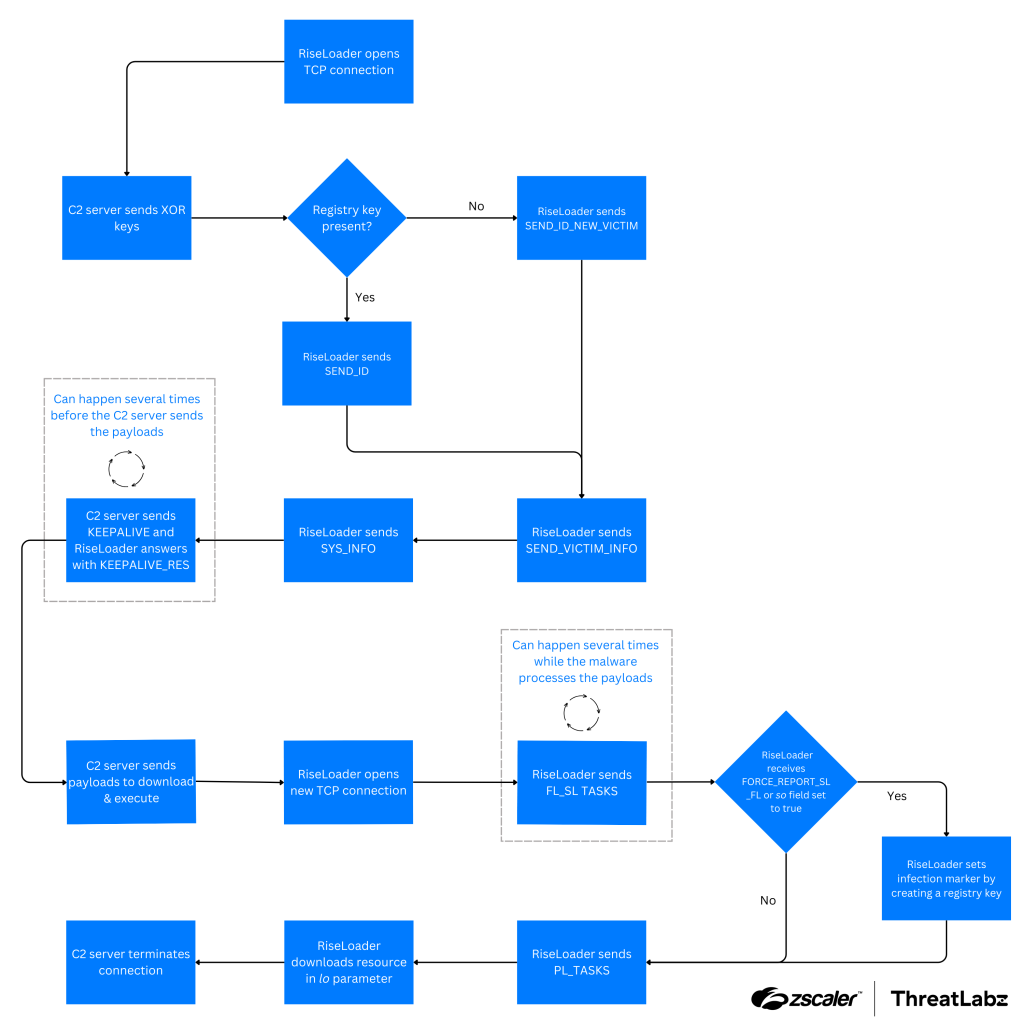
Figure 1: RiseLoader network communication protocol.
Network communication starts with the server sending a SET_XORKEYS message that contains two 1-byte XOR keys: the first for encrypting messages from the client, and the second for decrypting messages received from the server. After establishing the encryption keys for the session, the client sends either a SEND_ID_NEW_VICTIM or SEND_ID message. RiseLoader will determine which of these messages to use based on the existence of a specific registry key (HKEY_CURRENT_USERSOFTWAREdmdsaodgmarksmdkgsa).
Immediately after sending the campaign_id to the C2 server, RiseLoader will scan the victim’s file system to gather information about cryptocurrency wallets, extensions, and specific programs (shown in the Appendix). This information will be sent to the server using the SEND_VICTIM_INFO message type, followed by a SYS_INFO packet. Once the system information is sent, the server will maintain the connection by exchanging KEEPALIVE and KEEPALIVE_RES messages with RiseLoader.
RiseLoader waits for a PAYLOADS command containing a JSON encoded structure with payload URLs to download and execute on the victim’s system. The malware will then send SL_FL_TASKS_EXECUTED and PL_TASKS_EXECUTED messages to report the tasks that were executed.
During the processing phase for payloads, RiseLoader may create a registry key depending on the value specified by the so field in the PAYLOADS data structure or when receiving the FORCE_REPORT_SL_FL command from the C2 server. This registry key appears to serve as an infection marker and is located at HKEY_CURRENT_USERSOFTWAREdmdsaodgmarksmdkgsa. Under this key the registry name var1 is created with a hardcoded value set to 0x00b2. The actual value is not relevant for execution, as RiseLoader only checks for the presence of the registry key when choosing to send either SEND_ID or SEND_ID_NEW_VICTIM messages.
After processing all payloads, RiseLoader downloads a resource from a URL specified in the lo parameter of the PAYLOADS structure. Currently, this URL resolves to a 1×1 pixel PNG file, likely serving as a tracking method since the PNG file has no clear purpose in the malware code. After downloading and executing the payloads and downloading the URL from the lo parameter, RiseLoader will terminate its execution.
Comparison of the RiseLoader and RisePro communication protocols
The similarities between RiseLoader and RisePro are described below:
- Both use a custom binary TCP-based protocol with encoded JSON messages encrypted by a single byte key.
- The message structure is very similar: magic bytes, followed by a 4-byte payload size, and a 4-byte command type as shown in the figure below.
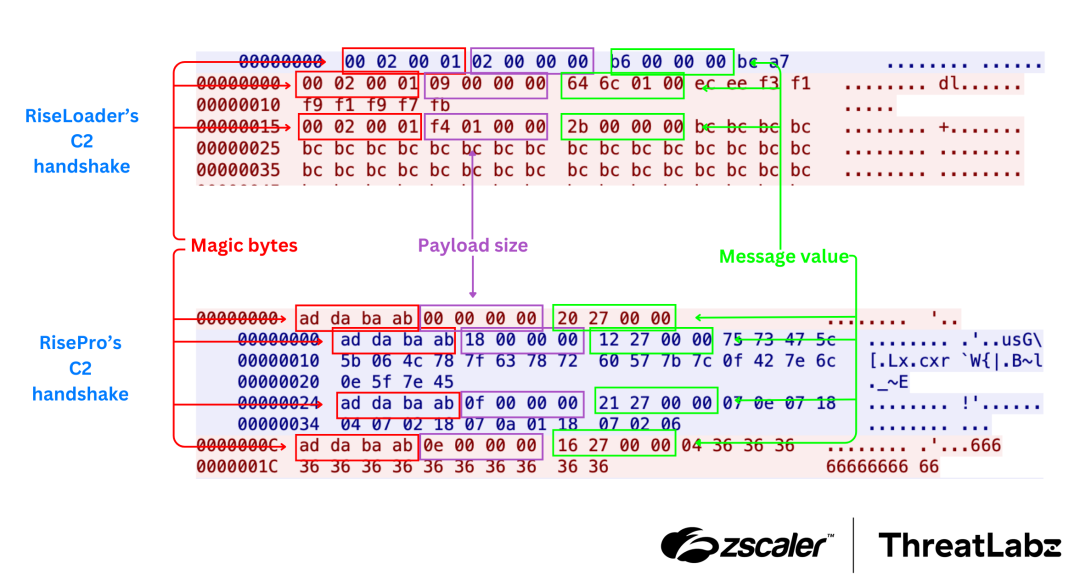
Figure 2: A comparison of RiseLoader’s C2 handshake and RisePro’s handshake, showing a similar structure.
- The initialization process is similar; however, RiseLoader has been simplified.
Conclusion
The security research community has tentatively linked RiseLoader to PrivateLoader, which is also developed by the same threat actor behind RisePro. This may be due to behavioral similarities, since both have been dropping similar malware families. However, RiseLoader has a distinct communication protocol that is far more similar to RisePro than PrivateLoader.
RiseLoader and RisePro share several similarities in their network communication protocols, including message structure, the initialization process, and payload structure. These overlaps may indicate that the same threat actor is behind both malware families. RiseLoader appears to still be in development with potential upcoming features for information stealing and anti-analysis.
Zscaler Coverage
Zscaler’s multilayered cloud security platform detects indicators related to the new variant of RisePro at various levels. The figure below depicts the Zscaler Cloud Sandbox, showing detection details for RiseLoader.
Figure 3: Zscaler sandbox report for RiseLoader.
Indicators Of Compromise (IOCs)
|
e4cbf31ac0aacb712219b080af8ccbc11899cc1e7a695077b61df5317ffc3a1d |
Packed sample SHA256 (RiseLoader) |
|
3834d3be235ebc488832a35dbd98d301c33281f9062a2cb16a681b77b3480044 |
Packed sample SHA256 (RiseLoader) |
|
5731851703e6ca1dd31c4ba3455a4e961621aab904d53ff5d747f811d3dee1b0 |
Packed sample SHA256 (RiseLoader) |
|
b5eaf10fcee125295402478e086f6e3c441024daec47dde0170ba528525f1eb2 |
Packed sample SHA256 (RiseLoader) |
|
eccf6b8a45f044951712b08013fcb020bff95e7c784164464afcf5e6adba1fdb |
Packed sample SHA256 (RiseLoader) |
|
0c26d498ccd4d7aea16e4b6e7e647fe4e16b89f67e18a8eacb4b0965fce2f381 |
Packed sample SHA256 (RiseLoader) |
|
65a060f8606f2213f1480ea132d519590f2736d8e1f53edb33fdfb27b3c9d869 |
Packed sample SHA256 (RiseLoader) |
|
c0cdd15f9913c6e88d7e124cbcba7ea981f12a856f473d0e96a94d8835d9ecf3 |
Dropped payload SHA256 (StealC) |
|
86c4e141ec49a5bb2646d39efec6207f01f9f9cfdff552715fcef860ec7d0b2d |
Dropped payload SHA256 (Lumma Stealer) |
|
4635a9149c53a2fbc072ceb338351d3b149e093cd43163e01d629bb016f8cd7c |
Dropped payload SHA256 (XMRig) |
|
54bc5a6ed4cca0770ced899f55b18a9e4d7ba7c6b0136f3291c43a5112ef0800 |
Dropped payload SHA256 (Vidar) |
|
7b2f904ede2ef17c8b9cda1433ffab97b5f7098ee33664a8362beaa1479e1baa |
Dropped payload SHA256 |
|
0df41caa968a517a454a6f36528c572af685f1ab62f792760e3a4d8e9de40461 |
Dropped payload SHA256 (StealC) |
|
bfe368b6b3729f8dfee1531e43cd41a787c554e3090645dd66f9785be96ccff4 |
Dropped payload SHA256 |
|
f06e0e417bca037bfa2150451bb6a4e38aa9db104c29167c1f642dc2ca60abfc |
Dropped payload SHA256 (Vidar) |
|
1bda055af670cb8e8f37d4860197b58cea1464c16dfaa31fadf42a9eedee8b25 |
Dropped payload SHA256 (Socks5Systemz) |
|
c04f64f0b5cbd336ad8b5dcf40727f50dba7534d66df1998110f38af533b45b3 |
Dropped payload SHA256 (Vidar) |
|
c0cdd15f9913c6e88d7e124cbcba7ea981f12a856f473d0e96a94d8835d9ecf3 |
Dropped payload SHA256 (StealC) |
|
ced59ab566ffe8b3274d7bba452a3b93341411c2c1cc23f2577a767ac846591a |
Dropped payload SHA256 (XMRig) |
|
41.216.183[.]36:3306 |
RiseLoader C2 |
|
185.209.21[.]88:3306 |
RiseLoader C2 |
|
147.45.44[.]166:3306 |
RiseLoader C2 |
Appendix
Cryptocurrency websites targeted by RiseLoader
|
sorare.com |
yobit.net |
zb.com |
binance.com |
huobi.com |
|
okex.com |
hitbtc.com |
bitfinex.com |
kraken.com |
bitstamp.net |
|
payoneer.com |
bittrex.com |
bittrex.zendesk.com |
gate.io |
exmo.com |
|
yobit.io |
bitflyer.com |
poloniex.com |
kucoin.com |
coinone.co.kr |
|
localbitcoins.com |
korbit.co.kr |
cex.io |
luno.com |
bitkonan.com |
|
jubi.com |
koinex.in |
koineks.com |
kuna.io |
koinim.com |
|
kiwi-coin.com |
leoxchange.com |
lykke.com |
localtrade.cc |
magnr.com |
|
lbank.info |
itbit.com |
gemini.com |
gdax.com |
gatehub.net |
|
satoshitango.com |
foxbit.com.br |
flowbtc.com.br |
exx.com |
exrates.me |
|
excambriorex.com |
ezbtc.ca |
infinitycoin.exchange |
tdax.com |
stex.com |
|
vbtc.exchange |
coinmarketcap.com |
vwlpro.com |
nocks.com |
nlexch.com |
|
novaexchange.com |
mynxt.info |
nzbcx.com |
nevbit.com |
mixcoins.com |
|
mr.exchange |
neraex.pro |
dsx.uk |
okcoin.com |
liquid.com |
|
quoine.com |
quadrigacx.com |
rightbtc.com |
rippex.net |
ripplefox.com |
|
qryptos.com |
ore.bz |
openledger.info |
omnidex.io |
paribu.com |
|
paymium.com |
dcexchange.ru |
dcexe.com |
bitmex.com |
funpay.ru |
|
bitmaszyna.pl |
bitonic.nl |
bitpanda.com |
bitsblockchain.net |
bitmarket.net |
|
bitlish.com |
bitfex.trade |
blockchain.com |
blockchain.info |
cryptofresh.com |
|
btcmarkets.net |
braziliex.com |
btc-trade.com.ua |
btc-alpha.com |
bitspark.io |
|
bitso.com |
bittylicious.com |
altcointrader.co.za |
arenabitcoin.com |
allcoin.com |
|
796.com |
abucoins.com |
aidosmarket.com |
bitcointrade.com |
bitcointoyou.com |
|
bitbanktrade.jp |
big.one |
bcex.ca |
bitconnect.co |
coinsbank.com |
|
coinsecure.in |
coinsquare.com |
coinspot.io |
coinsmarkets.com |
crypto-bridge.org |
|
dcex.com |
dabtc.com |
decentrex.com |
deribit.com |
dgtmarket.com |
|
btcturk.com |
btcxindia.com |
bt.cx |
bitstarcoin.com |
bitstarcoin.com |
|
coincheck.com |
coinmate.io |
coingi.com |
coinnest.co.kr |
coinrail.co.kr |
|
coinpit.io |
coingather.com |
coinfloor.co.uk |
coinegg.com |
coincorner.com |
|
coinexchange.io |
pancakeswap.finance |
coinbase.com |
livecoin.net |
mercatox.com |
|
cryptobridge.freshdesk.com |
volabit.com |
tradeogre.com |
bitkub.com |
uphold.com |
|
wallet.uphold.com |
login.blockchain.com |
tidex.com |
coinome.com |
coinpayments.net |
|
bitmax.io |
bitbank.cc |
independentreserve.com |
bitmart.com |
cryptopia.co.nz |
|
cryptonator.com |
volet.com |
my.dogechain.info |
spectrocoin.com |
exir.io |
|
exir.tech |
coinbene.com |
bitforex.com |
gopax.co.kr |
catex.io |
|
vindax.com |
coineal.com |
maicoin.com |
finexbox.com |
etherflyer.com |
|
bx.in.th |
bitopro.com |
citex.co.kr |
coinzo.com |
atomars.com |
|
coinfinit.com |
bitker.com |
dobitrade.com |
btcexa.com |
satowallet.com |
|
cpdax.com |
trade.io |
btcnext.io |
exmarkets.com |
btc-exchange.com |
|
chaoex.com |
jex.com |
therocktrading.com |
gdac.com |
southxchange.com |
|
tokens.net |
fexpro.net |
btcbox.co.jp |
coinmex.com |
cryptology.com |
|
cointiger.com |
cashierest.com |
coinbit.co.kr |
mxc.com |
bilaxy.com |
|
coinall.com |
coindeal.com |
omgfin.com |
oceanex.pro |
bithumb.com |
|
ftx.com |
shortex.net |
coin.z.com |
fcoin.com |
fatbtc.com |
|
tokenize.exchange |
simex.global |
instantbitex.com |
Cryptocurrency wallet software targeted by RiseLoader
|
atomic |
atomic wallet |
com.liberty.jaxx |
electrum |
exodus |
|
multidoge |
monero |
binance.chain |
binance |
Metamask |
Cryptocurrency wallet browser extensions targeted by RiseLoader
|
nkbihfbeogaeaoehlefnkodbefgpgknn |
ejbalbakoplchlghecdalmeeeajnimhm |
ibnejdfjmmkpcnlpebklmnkoeoihofec |
fhbohimaelbohpjbbldcngcnapndodjp |
fnjhmkhhmkbjkkabndcnnogagogbneec |
|
bfnaelmomeimhlpmgjnjophhpkkoljpa |
fhilaheimglignddkjgofkcbgekhenbh |
mgffkfbidihjpoaomajlbgchddlicgpn |
aodkkagnadcbobfpggfnjeongemjbjca |
kpfopkelmapcoipemfendmdcghnegimn |
|
fmblappgoiilbgafhjklehhfifbdocee |
hmeobnfnfcmdkdcmlblgagmfpfboieaf |
lpfcbjknijpeeillifnkikgncikgfhdo |
dngmlblcodfobpdpecaadgfbcggfjfnm |
aholpfdialjgjfhomihkjbmgjidlcdno |
|
agoakfejjabomempkjlepdflaleeobhb |
lgmpcpglpngdoalbgeoldeajfclnhafa |
ghpilmjholiicaobfjdkefcogmgaabif |
ebfidpplhabeedpnhjnobghokpiioolj |
mfgccjchihfkkindfppnaooecgfneiii |
Source: https://www.zscaler.com/blogs/security-research/technical-analysis-riseloader