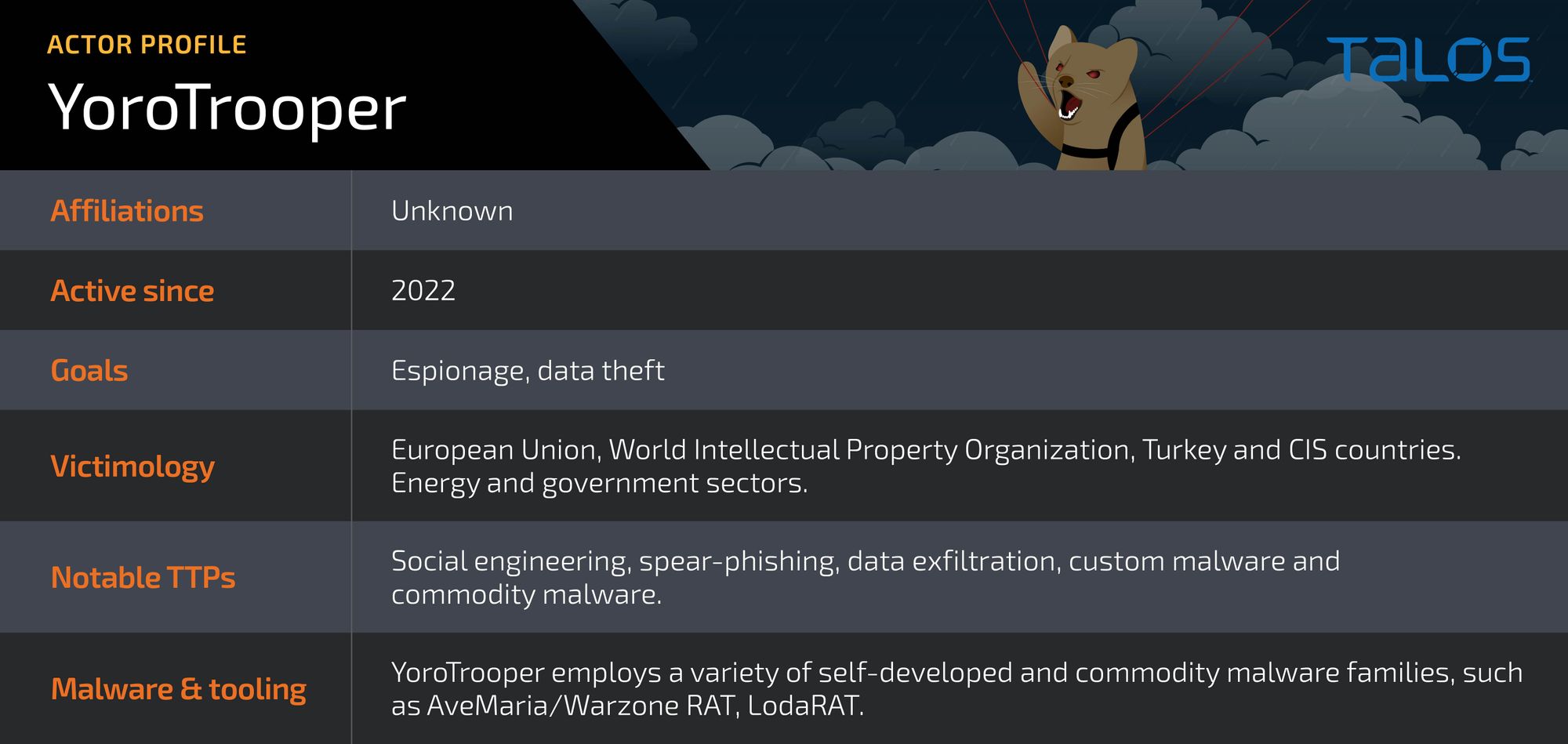
- Cisco Talos has identified a new threat actor, which we are naming “YoroTrooper,” that has been running several successful espionage campaigns since at least June 2022.
- YoroTrooper’s main targets are government or energy organizations in Azerbaijan, Tajikistan, Kyrgyzstan and other Commonwealth of Independent States (CIS), based on our analysis. We also observed YoroTrooper compromise accounts from at least two international organizations: a critical European Union (EU) health care agency and the World Intellectual Property Organization (WIPO). Successful compromises also included Embassies of European countries including Azerbaijan and Turkmenistan. We assess the actor also likely targets other organizations across Europe and Turkish (Türkiye) government agencies.
- Information stolen from successful compromises include credentials from multiple applications, browser histories & cookies, system information and screenshots.
- YoroTrooper’s main tools include Python-based, custom-built and open-source information stealers, such as the Stink stealer wrapped into executables via the Nuitka framework and PyInstaller. For remote access, YoroTrooper has also deployed commodity malware, such as AveMaria/Warzone RAT, LodaRAT and Meterpreter.
- The infection chain consists of malicious shortcut files (LNKs) and optional decoy documents wrapped in malicious archives delivered to targets. The actor appears intent on exfiltrating documents and other information, likely for use in future operations.
This new threat actor we are naming “YoroTrooper” has been targeting governments across Eastern Europe since at least June 2022, and Cisco Talos has found three different activity clusters with overlapping infrastructure that are all linked to the same threat actor. Cisco Talos does not have a full overview of this threat actor, as we were able to collect varying amounts of detail in each campaign. In some cases, for instance, we were able to fully profile a campaign, while in other cases, we only identified the infrastructure or compromised data.
Our assessment is that the operators of this threat actor are Russian language speakers, but not necessarily living in Russia or Russian nationals since their victimology consists mostly of countries in the Commonwealth of Independent States (CIS). There are also snippets of Cyrillic in some of their implants, indicating that the actor is familiar with the language. Also, in some cases, the attackers are targeting Russian language endpoints (with Code Page 866), indicating a targeting of individuals speaking that specific language.
Espionage is the main motivation for this threat actor, according to the tactics, techniques and procedures (TTPs) we have analyzed. To trick their victims, the threat actor either registers malicious domains and then generates subdomains or registers typo-squatted domains similar to legitimate domains from CIS entities to host malicious artifacts. The table below contains some of the domains created by this actor.
| Malicious subdomain | Legitimate domain | Entity |
|---|---|---|
| mail[.]mfa[.]gov[.]kg[.]openingfile[.]net | mfa[.]gov[.]kg | Kyrgyzstan’s Ministry of Foreign Affairs |
| akipress[.]news | akipress[.]com | AKI Press News Agency (Kyrgyzstan-based) |
| maileecommission[.]inro[.]link | commission[.]europa[.]eu | European Commission’s email |
| sts[.]mfa[.]gov[.]tr[.]mypolicy[.]top | mfa[.]gov[.]tr | Turkey’s Ministry of Foreign Affairs |
| industry[.]tj[.]mypolicy[.]top | industry[.]tj | Tajikistan’s Ministry of Industry and New Technologies |
| mail[.]mfa[.]az-link[.]email | mail[.]mfa[.]az | Azerbaijan’s Ministry of Foreign Affairs |
| belaes[.]by[.]authentication[.]becloud[.]cc | belaes[.]by | Belarusian Nuclear Power Plant (Astravets) |
| belstat[.]gov[.]by[.]attachment-posts[.]cc | belstat[.]gov[.]by | National Statistical Committee of Belarus |
| minsk[.]gov[.]by[.]attachment-posts[.]cc | minsk[.]gov[.]by | Official Website of the Government of Minsk (Belarus) |
The initial attack vectors are phishing emails with a file attached, which usually consists of an archive consisting of two files: a shortcut file and a decoy PDF file. The shortcut file is the initial trigger for the infection, while the PDF is the lure to make the infection look legitimate. The full details of the campaigns are detailed in the section below.
Phishing email example.
Regarding YoroTrooper’s toolset, the actor uses several commodity remote access trojans (RAT) and credential stealers. For RATs, we have seen the usage of AveMaria/Warzone RAT, LodaRAT, and a custom-built implant based on Python. Credential stealers used by YoroTrooper are either custom scripts, which in some cases are based on the open-sourced Lazagne project or commodity stealers such as the Stink Stealer. All the Python-based malware used in the campaign is wrapped up into an executable using frameworks such as Nuitka or PyInstaller. The custom implants (stealers and RATs) use Telegram bots to exfiltrate information or receive commands from the operator.
Our analysis has shown that YoroTrooper successfully obtained access to credentials of at least one account from a critical EU health care agency’s internet-exposed system and another from the World Intellectual Property Organization (WIPO). However, it is unclear if the threat actors targeted these institutions specifically via such phishing domains or if the credentials were compromised because they belong to users from a specific list of targeted countries in Europe. We found malicious domains masquerading as those of legitimate European Union government agencies, such as “maileecommission[.]inro[.]link”, which indicates that other European institutions were targeted.
YoroTrooper also successfully compromised embassies belonging to Turkmenistan and Azerbaijan, where the operators attempted to exfiltrate documents of interest and deploy additional malware.
Typically, YoroTrooper employs information stealers and RATs. An analysis of their stolen data reveals a treasure trove of information stolen from infected endpoints, such as credentials, histories and cookies for multiple browsers. Information such as credentials is highly valuable as they may be used either during lateral movement efforts or during subsequent YoroTrooper campaigns. Browsing histories can be used by a threat actor to specifically target victims with phishing lures based on their browsing habits.
While attribution can be difficult, we assess that there are no relevant overlaps between YoroTrooper and Kasablanka, the group behind the development of LodaRat4Android. Our analysis on Kasablanka in 2021 was that the operators might be different from the developers, which we can now confirm.
The overlaps with the PoetRAT team are stronger, especially on non-technical aspects of the campaigns but there are not enough for us to link them even with a low confidence level. Cisco Talos discovered the PoetRAT team in 2020 during a series of campaigns that successfully compromised Azerbaijan embassies and other government agencies.
PoetRAT team and YoroTropper share victimology and TTPs
While there are no concrete links between operators of PoetRAT and YoroTrooper, such as infrastructure overlaps, there are some similarities in their TTPs and victimology. Both actors use open-source tools to perform credential exfiltration and initial reconnaissance. In terms of bespoke tools, both threat actors have an affinity towards using Python-based implants, usually distributed, implemented or packed in a rather unusual way that is characteristic of the respective threat actors. The PoetRAT team would append the Python interpreter to a malicious document that would be extracted and used to execute the Python-based PoetRAT. YoroTropper used the Nuitka framework to pack their custom credential stealer in such a weird way that it ended up leaking the Python code rather than obfuscating it.
Regarding victimology, there are some noteworthy overlaps between YoroTrooper and the PoetRAT team, who mainly target Azerbaijan, specifically their embassies, energy sector and government institutions. YoroTropper is also targeting Azerbaijan and other CIS countries, and their embassies, with a similar focus on the energy sector.
Kasablanka is not the sole operator of LodaRAT
While attributing this campaign to a specific threat actor, what stuck out the most was the use of LodaRAT and its repeated attribution to a singular threat actor called “Kasablanka” in open-source reporting. While Talos assesses that LodaRAT is built and sometimes operated by Kasablanka, there is evidence that indicates that LodaRAT is being used in multiple distinct campaigns. Therefore, despite the fact that LodaRAT isn’t publicly available, either open-sourced or for sale publicly — although one can be decompiled easily for use by any actor — our assessment is that there are multiple operators in the threat landscape employing LodaRAT. Therefore, YoroTrooper’s use of LodaRAT should not be used as the sole indicator for attribution.
Our research shows that the LodaRAT samples used by YoroTrooper deviate from previous versions of the malware employed by Kasablanka. In fact, the LodaRAT variants used by Yoro Trooper are based on versions we’ve seen being deployed in other crimeware campaigns alongside RedLine and VenomRAT, indicating LodaRAT’s availability to multiple threat actors.
This strengthens our assertion that although Kasablanka is the developer of LodaRAT and Loda4Android, it is not the sole operator of LodaRAT, an assessment we made as early as 2021.
This threat actor extensively targets CIS countries using a variety of malware deployed by a relatively simple infection chain. The operators have utilized a diverse suite of malware such as:
- Commodity RATs and stealers: Warzone, LodaRAT and Stink stealer.
- Custom Python-based information stealers: Custom scripts for stealing Google Chrome browser credentials.
- Custom Python-based RATs (with exfiltrators): First seen in June 2022, but gained popularity with the threat actor around February 2023.
- Reverse shells: Python and Meterpreter-based reverse shells.
The following is a timeline of the various geographies targeted by attacks in the campaign operated by YoroTrooper.
Time frame | Targeted Geography | Salient TTPs |
February 2023 | Uzbekistan | • Reuses Uzbekistani themed lures/decoys: • Memo from energy company “UZBEKHYDROENERGO” • Deploys a custom-built Python based reverse shell and file exfiltrator with variants built via PyInstaller and Nuitka. • Uses HTA files. • Also deploys Meterpreter reverse shells in certain cases. |
Late January 2023 | Uzbekistan | • Uses Uzbekistani themed lures/decoys: • Memo from energy company “UZBEKHYDROENERGO” • Deploys Python implant – custom Python based stealer. • HTA downloads Decoy and dropper implant. |
Early January 2023 | Tajikistan | • Uses Tajikistani themed lures: Report from Government of Tajikistan. • Deploys Python implant – custom Python based stealer. • HTA downloads decoy documents and dropper implants. |
December 2022 | Russia | • Uses Russian themed lures. • Uses VHDX files containing archives and LNKs that download and activate LodaRAT. |
November 2022 | Azerbaijan | • Uses Azerbaijani lures and malicious domains: • mail[.]mfa[.]az-link[.]email, true[.]az-link[.]email • Deploys Python implant – Stink stealer. |
October 2022 | Belarus | • IPs and domains masquerade as Belarusian domains: • mail[.]belaes[.]by[.]authentication[.]becloud[.]cc • One variant of HTA downloads only AveMaria/Warzone RAT. • Another variant of HTA downloads only Python based implants – Stink stealer. • No lures. |
September 2022 | Russia | • VHDX based distribution introduced. • No HTAs employed – LNKs download .NET based implants directly using curl. • Malicious subdomains masquerading (typo-squatted) as Russian government entities: • rnail[.]mintrans[.]gov[.]ru[.]inro[.]link ; rnail[.]iterrf[.]ru[.]inro[.]link ; account[.]nail[.]ru[.]inro[.]link ; rnail[.]rnid[.]ru[.]inro[.]link |
August 2022 | Belarus, Russia | • IPs and domains masquerade as Belarusian and Russian domains: • mail[.]hse[.]ru[.]attachment-posts[.]cc ; belstat[.]gov[.]by[.]attachment-posts[.]cc ; minsk[.]gov[.]by[.]attachment-posts[.]cc • No HTAs employed – LNKs download Python based reverse shells directly using curl. • Corrupt PDFs used as lures. |
The latest infection chain from January 2023 is relatively straightforward but consists of multiple components such as archives, LNKs, HTAs and ultimately the final payloads:
The infection chains begin with a malicious archive (RARs or ZIPs) delivered to targets with lure document titles referring to topics of interest to CIS nations, such as:
- National_Development_Strategy.rar
- Presidents_Strategy_2023.rar
The campaign has also employed some generic file names as well such as “Nota.rar”, “вложение.rar”.
We have also observed the occasional inclusion of decoy documents in the archive files, as well.
The malicious LNK files are simple downloaders that employ mshta.exe to download and execute a remote HTA file on the infected endpoint.
LNK files downloading and executing remote HTA files.
The malicious HTA files employed in this campaign have seen a steady evolution with the latest variant downloading the next-stage payload: a malicious EXE-based dropper and a decoy document. All these tasks are accomplished by running PowerShell-based commands.
Malicious HTA.
Custom-built final payloads
YoroTrooper has been consistently introducing new malware into their infection chains in this campaign, including both custom-built and commodity malware. It is worth noting that while this campaign began with the distribution of commodity malware such as AveMaria and LodaRAT, it has evolved significantly to include Python-based malware. This highlights an increase in the efforts the threat actor is putting in, likely derived from successful breaches during the course of the campaign.
Custom Python RAT
The custom-built Python-based RAT is relatively simple. It uses Telegram as a medium of C2 communication and exfiltration and contains functionality to:
- Run arbitrary commands on the infected endpoint.
- Upload files of interest to the attacker to a telegram channel via a bot.
This bot was wrapped up into a .exe either using PyInstaller or Nuitka and then deployed in the field. There are some interesting observations here suggesting that the adversary may be speak Russian:
- The presence of telegram messages in Russian such as: “Сохраняю в {save_dir}” or “Файл загружен!nИмя”.
- Code that decodes the output of a command run on the system into CP866 – Code page for Cyrillic.
Snippet: Python based RAT used by YoroTrooper.
Customized stealer script
Another Python-based payload distributed in January 2023 consists of a simple stealer script that will extract login data for the Chrome browser and exfiltrate it via a Telegram bot. This custom script has likely been stitched together from publicly available sources, such as Lazagne:
Commodity and miscellaneous malware
YoroTrooper has relied heavily on the use of primarily two commodity malware families, AveMaria/Warzone RAT and LodaRAT, especially in October and November 2022. AveMaria is a highly prolific malware family available for sale online, while LodaRAT is a RAT-based family whose authorship has been attributed to the Kasablanka threat actor.
Stink stealer analysis
Yet another one of the final payloads found being deployed by YoroTrooper is an open-source credential stealer called “Stink,” which is wrapped into an executable file using the Nuitka Python compiler framework.
Stink has several modules from Chromium-based browsers that collect credentials, cookies and bookmarks, among other information. It harvests Filezilla credentials and authentication cookies from Discord and Telegram. From the system, the stealer will collect a screenshot, external IP address, operating system, processor, graphic card and running processes:
All modules are executed in their own process and even each process will use its own threads to speed up the information collection process. The information is stored in a temporary directory before being compressed and exfiltrated.
The sender module is responsible for data exfiltration via a Telegram bot. As of early March, the latest version of Stink Stealer 2.1.1 has an autostart configuration option that will create a link in the startup folder of the victim profile with the name “Windows Runner.”
Autostart configuration options.
Miscellaneous malware
Apart from commodity malware, we’ve also observed YoroTrooper deploy implants serving as reverse shells against their targets. For example, in September 2022, we saw a simple Python-based reverse shell. This one, however, was missing the Cyrillic language check (CP866).
Another set of reverse shell implants that YoroTrooper occasionally uses are Meterpreter binaries that are then used to execute arbitrary commands on the infected endpoint. This tactic was seen being used by YoroTrooper as late as February 2023.
A C-based custom keylogger also discovered by Talos probably deployed by one of the final stage payloads consists of the ability to record keystrokes and save them to a file on disk.
Snippet: Keylogger functionality.
Ways our customers can detect and block this threat are listed below.
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCs for this research can also be found at our Github repository here.
Source: https://blog.talosintelligence.com/yorotrooper-espionage-campaign-cis-turkey-europe/
Views: 0