Every month the Nextron Threat Research Team (NTRT) shares insights into evasive threats that we’ve seen in the wild via our Valhalla service. The aim is to highlight interesting samples our rules detected and have or had very low detection rates as reported by VirusTotal scanning.
Please note that we are aware that VirusTotal results do not represent the full capabilities of antivirus or EDR Products. The aim is to highlight how Threat Actors are taking into account evasiveness with some of these samples.
Threat Overview
The following table gives an overview of the threats mentioned in this blog. You can use the respective Valhalla page for every threat to get a list of the hashes.
Threat Digest
MrAgent
The MrAgent sample was first reported by MalwareHunterTeam where he pointed it out from a related sample used by RansomHouse.
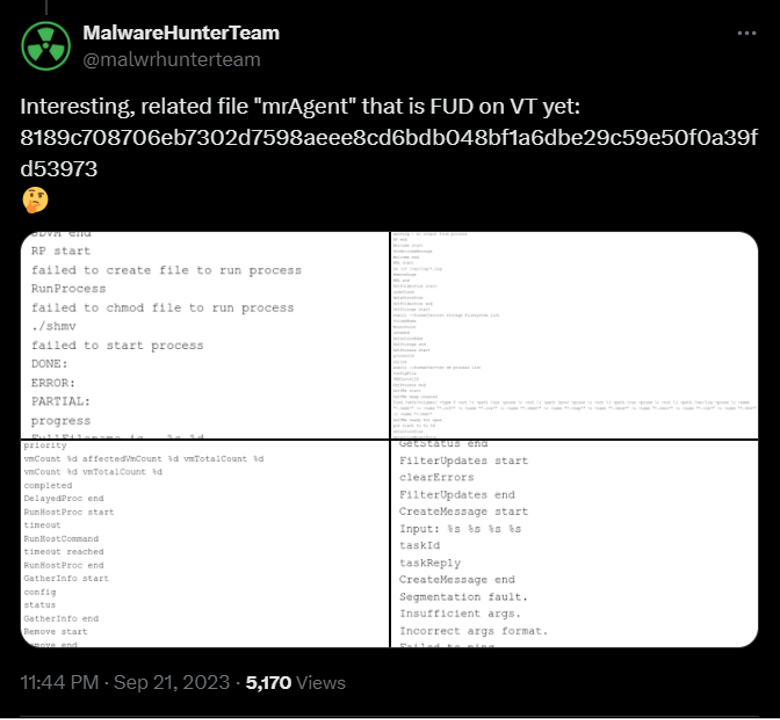
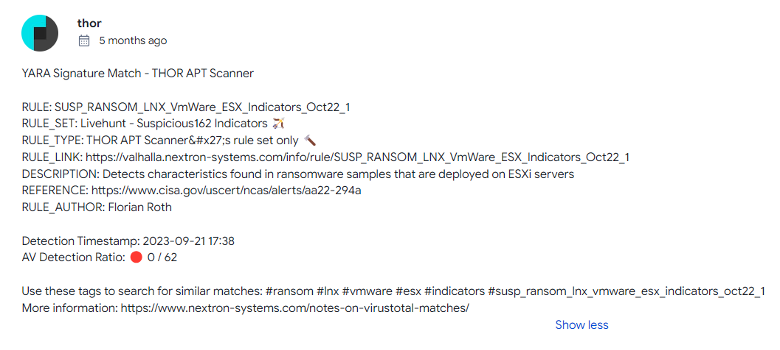
The sample triggered one of our generic Vmware ESX malware rules on the date of the upload last September.
A couple of months later the Trellix team put out a blog where they dissected the sample in question. Here is an excerpt from the Trellix blog.
MrAgent is a binary designed to run on hypervisors, with the sole purpose of automating and tracking the deployment of ransomware across large environments with a high number of hypervisor systems. The binary connects back to a set of command & control servers, which need to be supplied as a command-line argument.
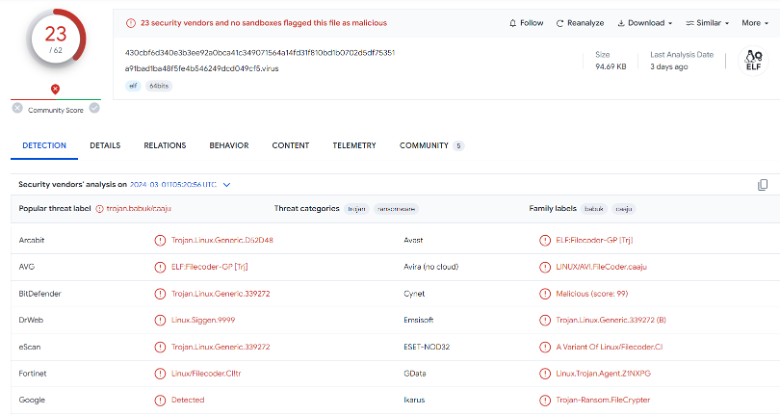
We’ve only noticed one additional new sample uploaded on the 2024-03-01 that was quickly picked up by multiple vendors (430cbf6d340e3b3ee92a0bca41c349071564a14fd31f810bd1b0702d5df75351)
Guloader Shellcode
Guloader is a first stage shellcode based malware that is usually used to download other types of malware such as Agent Tesla, Lokibot and others. It was discovered in 2019 and is still going strong to this day.
We’re seeing multiple uploads a day to VirusTotal, with almost all of the uploaded samples having 0 detections.
It turns out that most of these samples are memory dumps uploaded via the VT API. Investigating them would reveal the GuLoader shellcode.
It is worth noting that we’ve also seen GuLoader ShellCode uploaded directly and some vendors did indeed pick it up directly.

HemiGate
HemiGate is a backdoor used by the threat actor known as Earth Estries. It was first reported by TrendMicro last year. Since the initial reporting we’ve tracked 4 samples uploaded to VT over the next months. The most recent one was uploaded early this (January 2024)
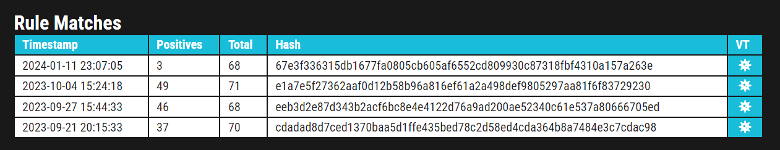
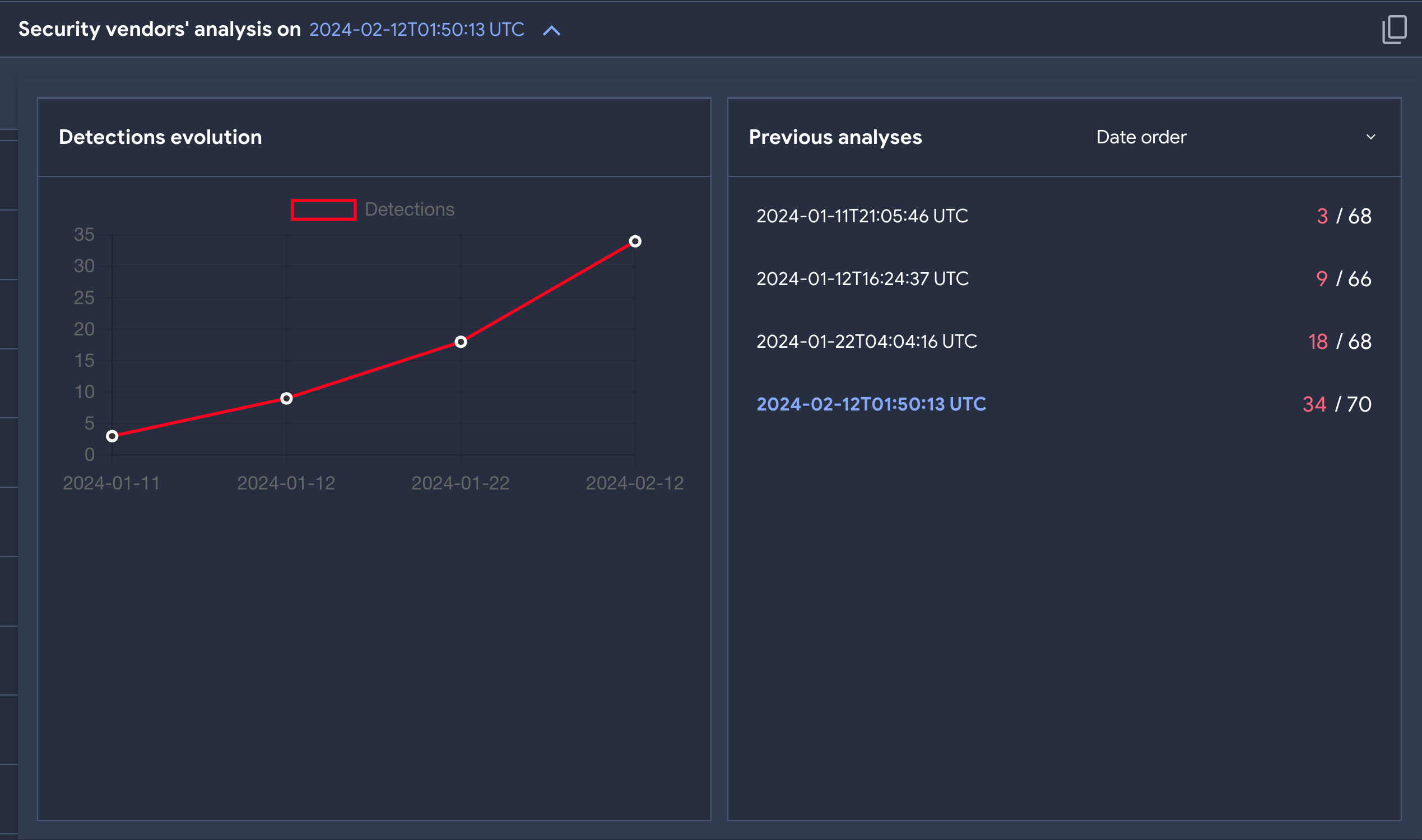
While the first 3 samples uploaded had very high AV matches. The most recent one only started with 3 vendors having coverage for it.
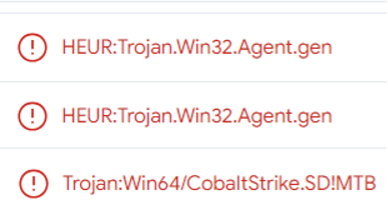
We can see the coverage increased over the next months to reach 34/70.
This latest sample of the HemiGate backdoor loader, is very similar in nature to the previous ones. It mimics the “libvlc.dll” DLL to achieve DLL sideloading as can be seen by the exported functions.
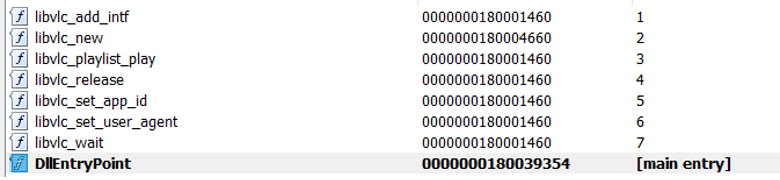
All of the exports are empty except for “libvlc_new” which calls the functions that decrypts the encrypted payload (HemiGate backdoor) with RC4.
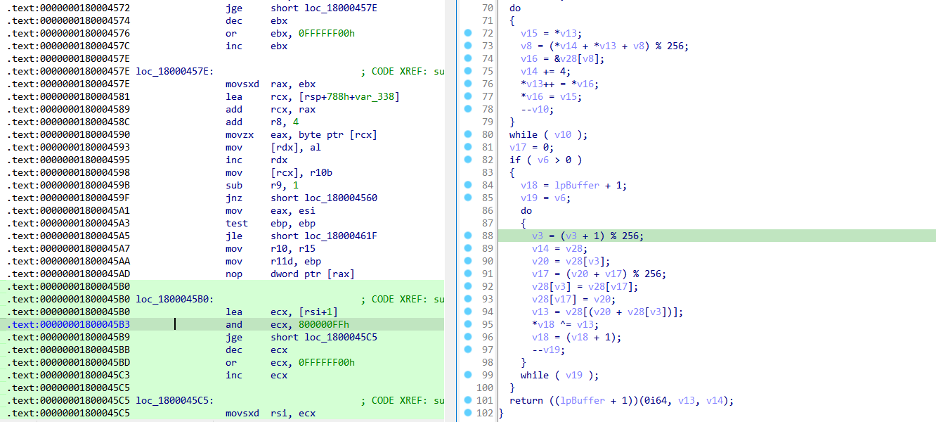
From strings found in the sample, it seems highly likely that this was generated via the AheadLib tool.
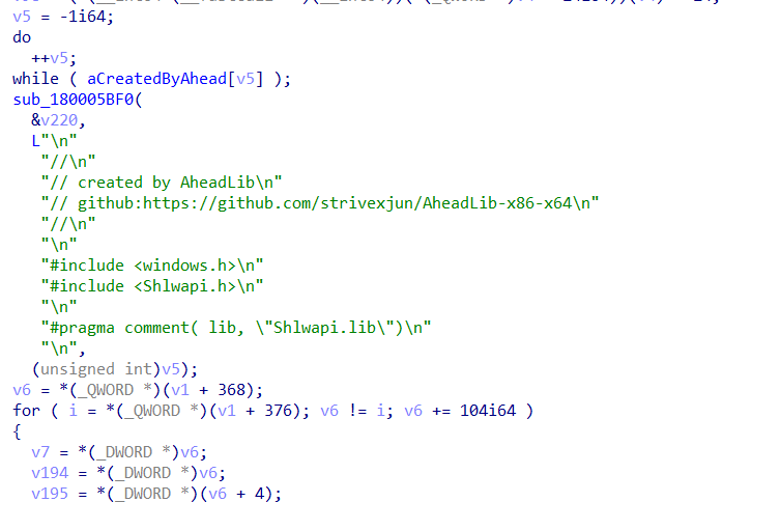
IronWind
IronWind is an initial access downloader first reported by Proofpoint last November. You can read their analysis for full technical details. Since that report we’ve been tracking the IronWind samples being uploaded to VT.
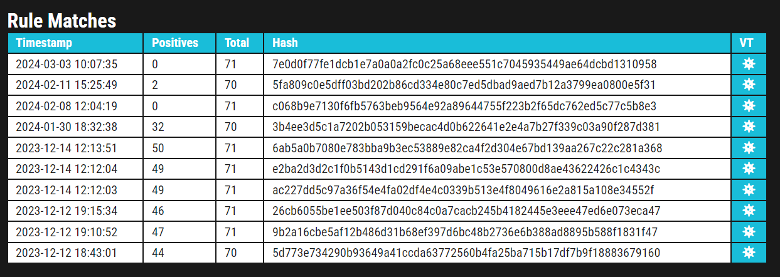
And we can see, earlier uploads by the end of last year were highly flagged by almost every major vendor. But in recent months the samples we’re monitoring are getting more stealthier and evading AV signatures. A look at the decrypted strings shows potential new capabilities.
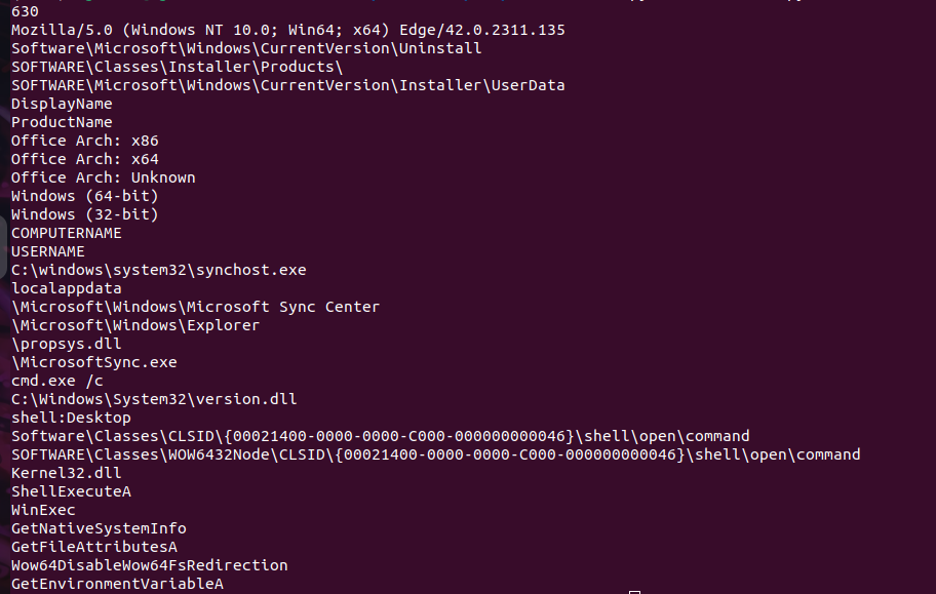
We’ll be releasing a blog in the upcoming weeks detailing the capabilities of this new variant.
Detection opportunity
HemiGate Sideloading Activity
The following Sigma rule can be used to detect potential sideloading of libvlc.dll
title: Potential Libvlc.DLL Sideloading
id: bf9808c4-d24f-44a2-8398-b65227d406b6
status: test
description: Detects potential DLL sideloading of "libvlc.dll", a DLL that is legitimately used by "VLC.exe"
references:
- https://www.trendmicro.com/en_us/research/23/c/earth-preta-updated-stealthy-strategies.html
- https://hijacklibs.net/entries/3rd_party/vlc/libvlc.html
author: X__Junior
date: 2023/04/17
tags:
- attack.defense_evasion
- attack.persistence
- attack.privilege_escalation
- attack.t1574.001
- attack.t1574.002
logsource:
category: image_load
product: windows
detection:
selection:
ImageLoaded|endswith: 'libvlc.dll'
filter_main_vlc:
ImageLoaded|startswith:
- 'C:Program Files (x86)VideoLANVLC'
- 'C:Program FilesVideoLANVLC'
condition: selection and not 1 of filter_main_*
falsepositives:
- False positives are expected if VLC is installed in non-default locations
level: medium
Nextron steps in where traditional security measures might miss threats. Our digital forensics tools conduct thorough analyses of systems that show signs of unusual behavior. They effectively identify risky software and expose a range of threats that could go unnoticed by standard methods.
Our signature collection is tailored to detect a variety of security concerns. This includes hacker tools, their remnants, unusual user activities, hidden configuration settings, and legitimate software that might be misused for attacks. Our approach is especially useful in detecting the tactics used in supply chain attacks and identifying tools that evade Antivirus and EDR systems.
Source: Original Post
“An interesting youtube video that may be related to the article above”