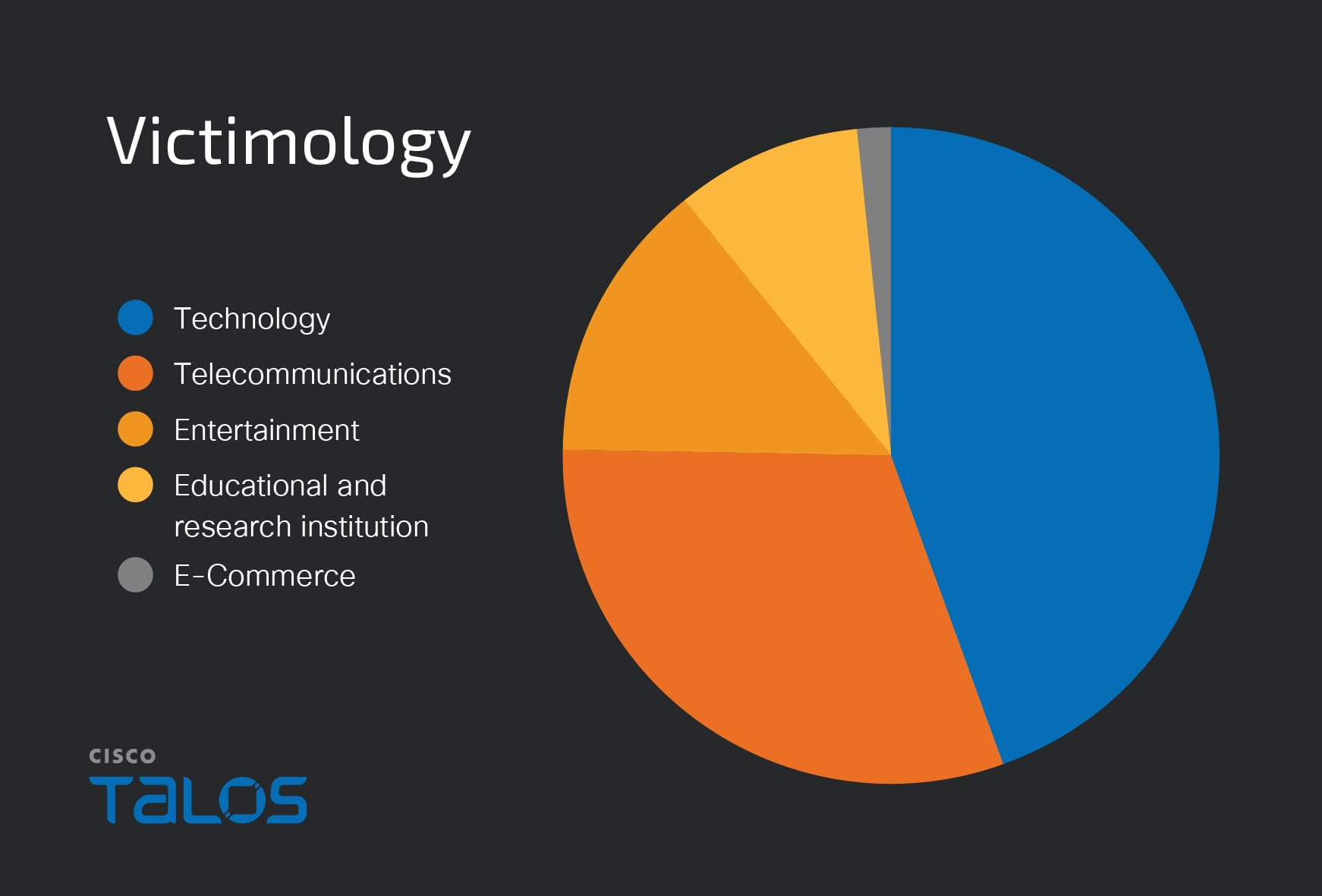
Summary: A critical SQL Injection vulnerability (CVE-2025-22954) has been discovered in Koha, a popular open-source library management system, affecting multiple versions. This flaw allows both unauthenticated and authenticated users to inject arbitrary SQL instructions, posing a severe risk to sensitive data. Koha version 24.11.02 has been released to address this issue, along with additional security enhancements.…
Read More