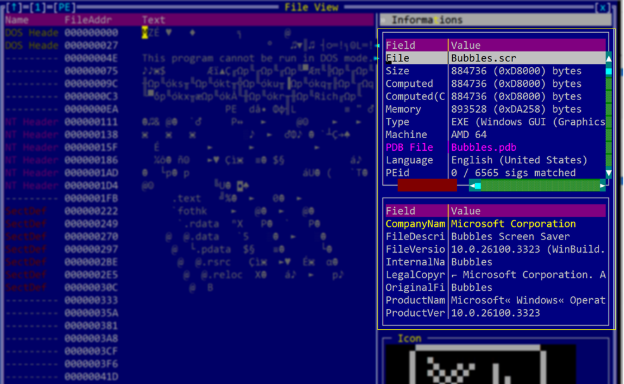
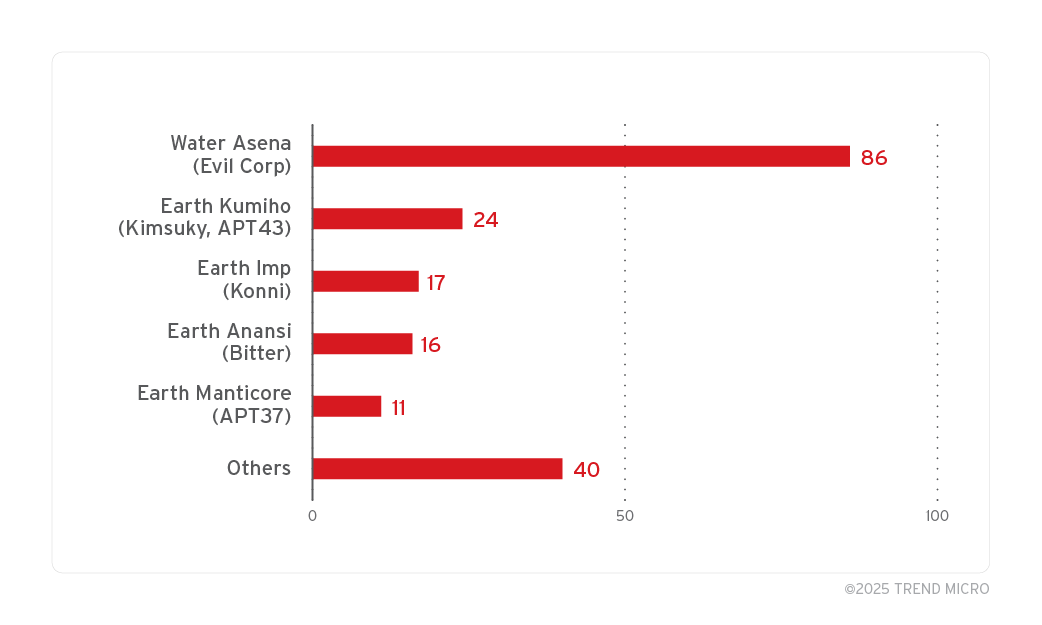
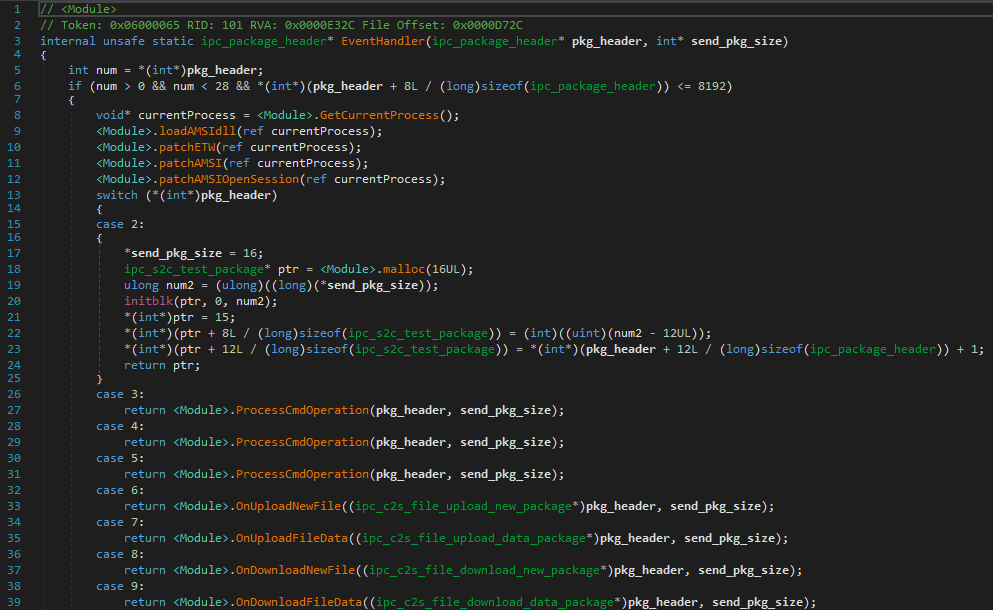
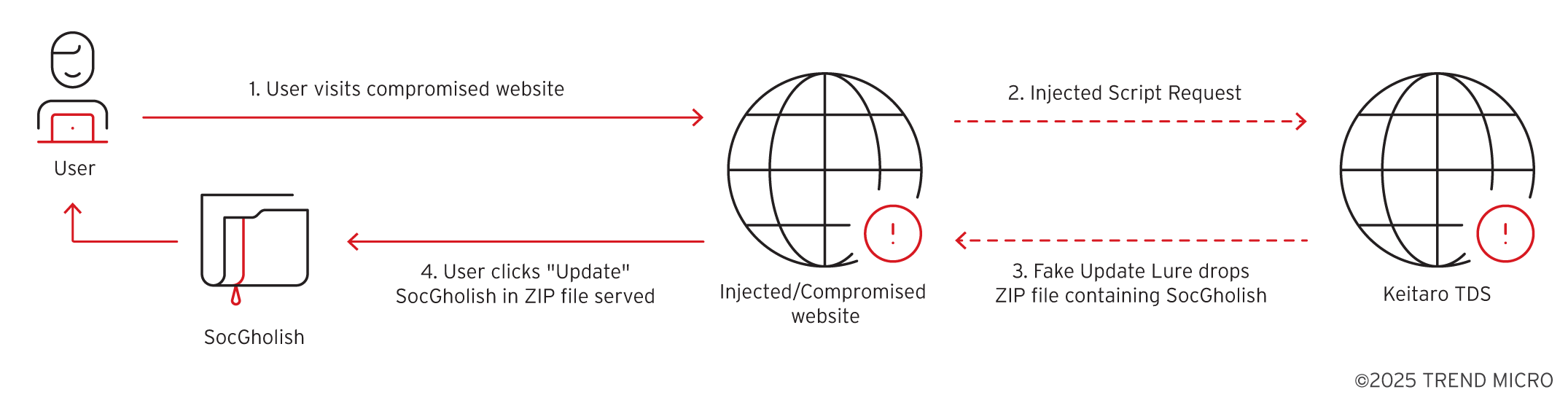
Microsoft has identified a zero-day elevation of privilege vulnerability in the Windows Common Log File System (CLFS), tracked as CVE-2025-29824, that has been exploited by the PipeMagic malware, targeting sectors in the U.S., Venezuela, Spain, and Saudi Arabia. The company released security updates to mitigate this issue.…
Read More