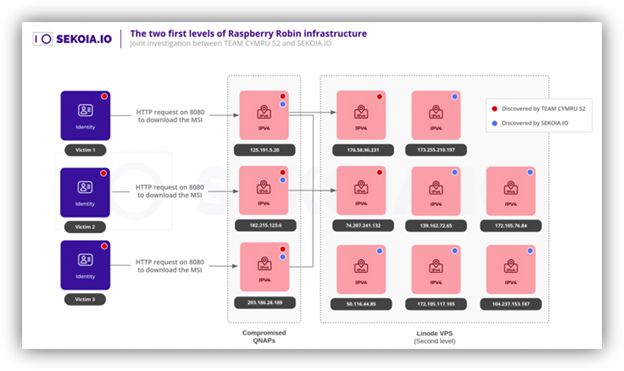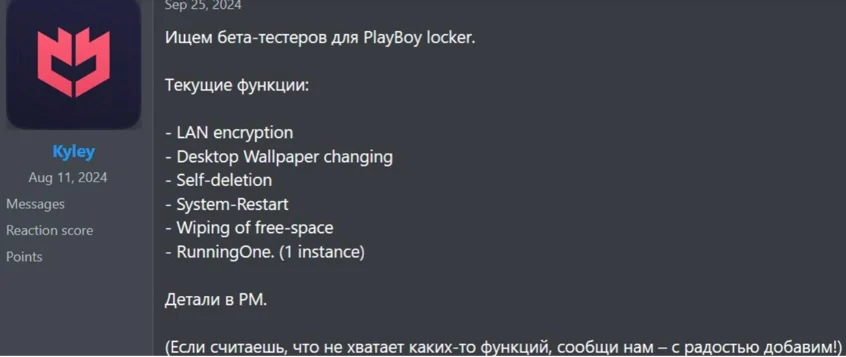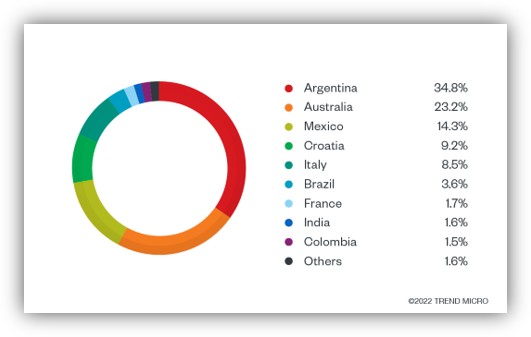
GOFFEE is a threat actor recognized for targeting entities in Russia through spear phishing and using various malicious techniques, including the deployment of modified malware. They have introduced a new implant called “PowerModul” and are shifting from PowerTaskel to a binary Mythic agent for lateral movement.…
Read More