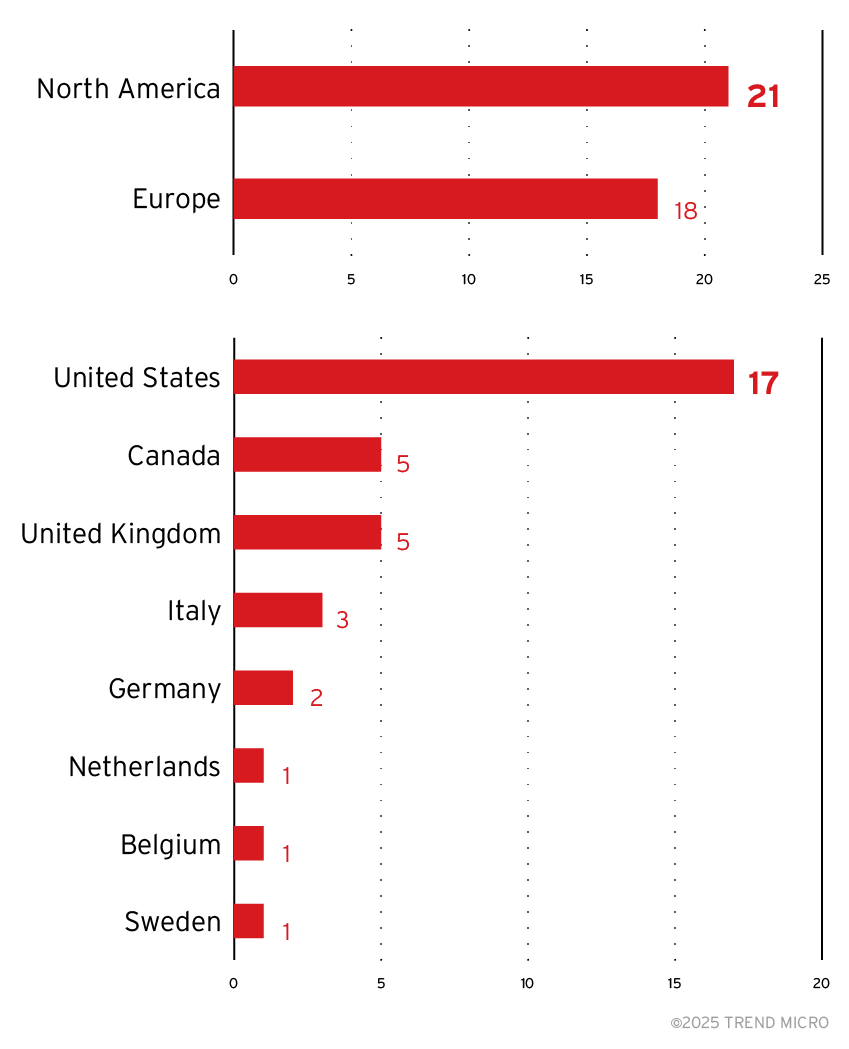
Summary: The Cybersecurity and Infrastructure Security Agency (CISA) has alerted users about a critical vulnerability (CVE-2025-1316) in Edimax IC-7100 IP cameras, with a CVSS score of 9.8. This flaw enables remote code execution due to the camera’s inability to properly handle incoming requests. CISA emphasizes the urgent need for users to secure their devices as public exploits are already available and Edimax has not coordinated a fix.…
Read More