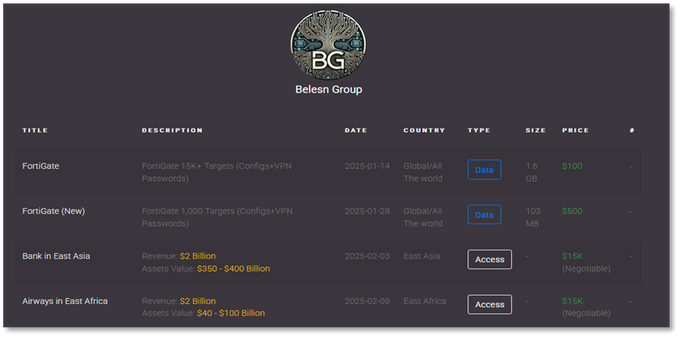
This article provides an in-depth analysis of an intrusion investigation conducted by security professionals, focusing on the methods and techniques used to unravel a complex attack. It details how the threat actor gained initial access, performed credential theft, and executed lateral movement within a network. The findings highlight the challenges of gathering complete telemetry during such investigations.…
Read More