Summary: The video discusses security audits for web applications, particularly focusing on the challenges faced when testing applications blindly without source code access. It highlights how backend implementation details, such as error messages and unique HTTP headers, can offer valuable insights. The discussion then shifts to a practical example, analyzing a CTF challenge involving a Go web application and uncovering a race condition vulnerability related to error handling in the code.Key…
Read More Tag: UNIX

This article concludes the “Linux Persistence Detection Engineering” series by exploring advanced persistence mechanisms in Linux. Key topics include manipulation of GRUB and initramfs for persistence, exploitation of PolicyKit (Polkit) permissions, D-Bus configuration for unauthorized access, and NetworkManager dispatcher scripts. Readers are equipped with practical examples and detection strategies to bolster their defenses against Linux persistence threats.…
Read More
Summary: Libxml2, a widely used XML parsing library, has multiple vulnerabilities (CVE-2024-56171, CVE-2025-24928, CVE-2025-27113) that could lead to denial of service and arbitrary code execution. These vulnerabilities have been addressed in recent releases (2.12.10 and 2.13.6), and users are advised to update immediately. Failure to update may leave systems exposed to significant security risks.…
Read More 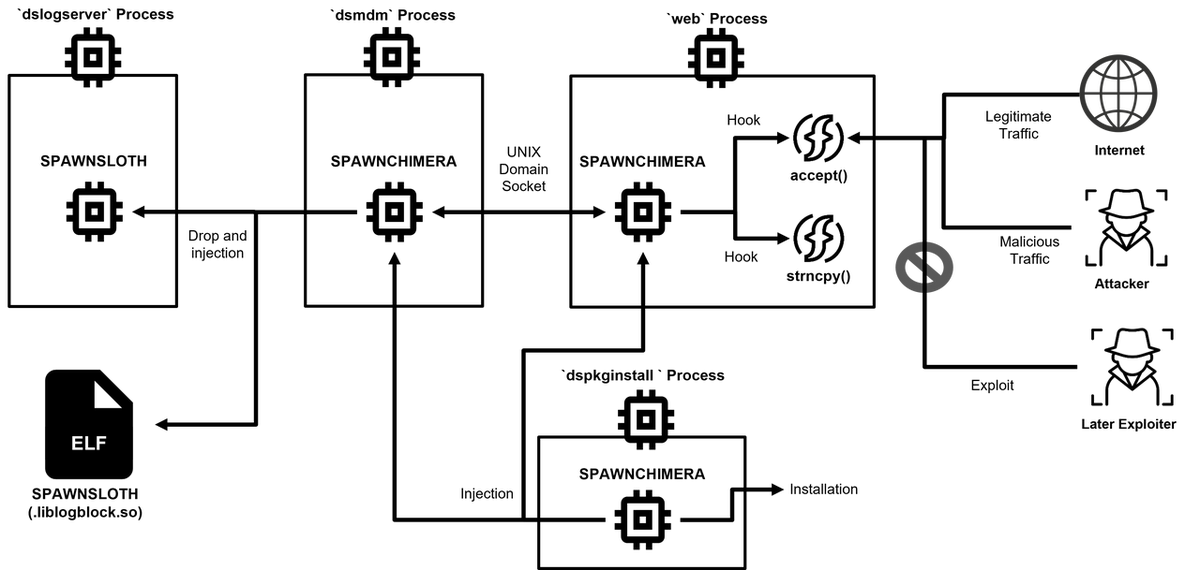
The article discusses the vulnerability CVE-2025-0282 related to Ivanti Connect Secure and the subsequent rise of SPAWNCHIMERA malware which exploits this vulnerability. JPCERT/CC noted several instances of exploitation in Japan. The updated SPAWNCHIMERA incorporates various functionalities to obscure its operations, manage inter-process communications, and dynamically address the vulnerability.…
Read More 
Summary: OpenSSH has issued security updates in response to two significant vulnerabilities: a machine-in-the-middle (MitM) flaw introduced in 2014 and a pre-authentication denial of service (DoS) vulnerability introduced in 2023. Both vulnerabilities, discovered by Qualys, pose serious risks to users, particularly those who have enabled specific configurations.…
Read More 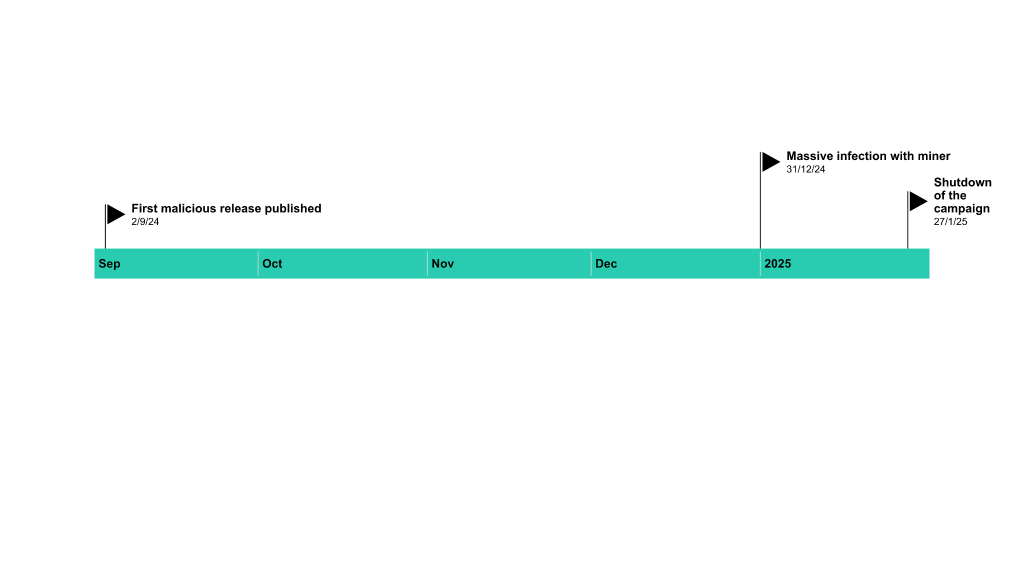
The article discusses a sophisticated cyber attack that began on December 31, where cybercriminals targeted users worldwide by distributing trojanized games via torrent sites to deploy the XMRig cryptominer. The attackers utilized various defense evasion techniques to deliver malicious content while exploiting reduced vigilance during the holiday season.…
Read More 
This report analyzes various cyber threats targeting diverse sectors, with a focus on malicious campaigns and tools utilized by actors from different regions. Notably, the Sandworm APT’s espionage against Ukrainian users highlights threats to national security, while other reported incidents reveal exploitation of vulnerabilities and the increasing sophistication of ransomware tactics.…
Read More 
Summary: Cybersecurity researchers identified a critical bypass vulnerability (CVE-2025-23359) in the NVIDIA Container Toolkit that allows attackers to break container isolation and gain full access to the host system. This flaw affects multiple versions of the NVIDIA Container Toolkit and GPU Operator, with a CVSS score of 8.3.…
Read More 
In Q4 2024, APT groups from China, North Korea, Iran, and Russia significantly escalated their cyber operations, demonstrating advanced techniques such as cyber espionage, credential theft, and disruptive assaults. These developments highlight a persistent threat to critical sectors, including government infrastructure and financial institutions worldwide. Affected: governments, critical infrastructure, defense, financial institutions, research entities
Read More Keypoints :
APT groups showcased increasingly sophisticated techniques across a range of cyber threats in Q4 2024.…
Summary: Researchers have disclosed a high-severity vulnerability (CVE-2024-36972, CVSS 7.5) in the Linux kernel’s af_unix component, which can lead to kernel crashes and privilege escalation. This double free vulnerability could potentially be exploited by attackers, allowing for risks like container escape. A proof-of-concept exploit has been made available, highlighting the urgent need for system administrators to upgrade their systems.…
Read More 
Summary: A coalition of nine application security providers is launching a fork of the Semgrep code-scanning project, creating Opengrep, after Semgrep transitioned some features to a paid version. The new initiative aims to restore key functionalities and maintain neutrality by being owned collectively rather than by a single vendor.…
Read More 
Researchers have identified a malicious npm package named postcss-optimizer, linked to North Korean state-sponsored threat actors, specifically the Lazarus group. This package, which masquerades as a legitimate library, has been downloaded 477 times and contains the BeaverTail malware, functioning as both an infostealer and a loader.…
Read More 
In 2024, an alarming increase in reported vulnerabilities rose by 40%, exceeding 40,000 CVEs, prompting the JFrog Security Research team’s critical assessments of threats to application security. The team has highlighted significant vulnerabilities in MLOps platforms, Docker Hub repositories, and open-source libraries, exposing users to possible malware and exploitation.…
Read More
This week’s discovery revealed over 10,000 compromised WordPress sites displaying deceptive Google browser update pages. The malware, targeting both Apple and Microsoft users, includes AMOS and SocGholish variants. The exploitation occurred through client-side attacks utilizing outdated WordPress plugins, notably the RocketLazyLoadScript. This incident highlights vulnerabilities in the web supply chain and reiterates the importance of timely software updates.…
Read More 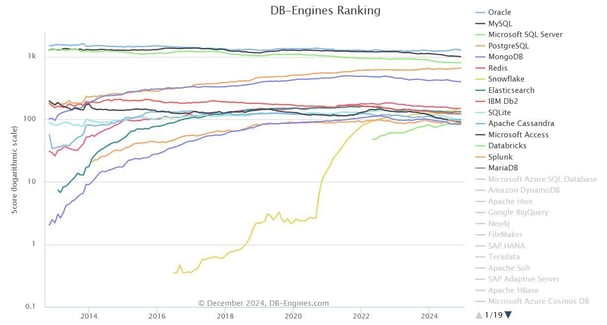
In the competitive landscape of database technologies, Oracle Database maintains its dominance and is widely adopted by Fortune 500 companies due to its scalability, performance, and security features. However, vulnerabilities exist, particularly with the emergence of the Oracle Database Attacking Tool (ODAT), a Python-based tool used by both penetration testers and threat actors to exploit weaknesses within Oracle Database systems.…
Read More 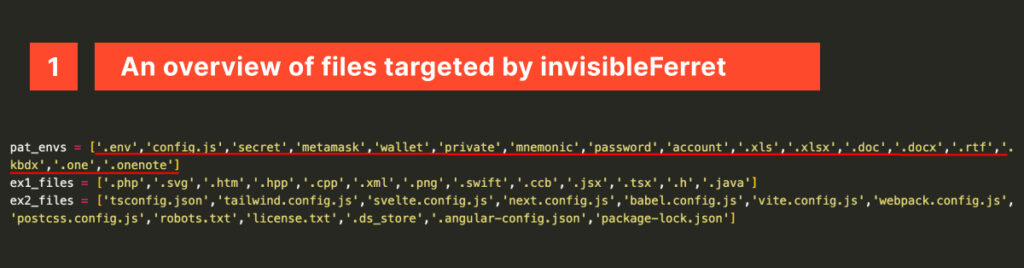
The article discusses the InvisibleFerret malware, associated with North Korean threat actors, exploiting fake job interviews to distribute itself. This malware targets sensitive files, source code, and user data in technological, financial, and cryptocurrency sectors, demonstrating high levels of sophistication and stealth. Affected: technological sector, financial sector, cryptocurrency sector
Read More Keypoints :
North Korean activity observed using fake job interviews to spread malware.…
This article examines two scenarios wherein attackers exploit misconfigured Redis servers and utilize cloud storage resources to execute malicious scripts and gain unauthorized access. The sophisticated techniques employed emphasize the necessity for proactive defensive measures. Affected: Redis servers, macOS systems
Read More Keypoints :
Attackers exploit misconfigurations in Redis services to execute remote commands.…
The article discusses the emergence of InvisibleFerret malware, which is being spread through fake job interviews targeting developers in the tech and cryptocurrency sectors. This malware is part of a broader campaign that includes other malware like BeaverTail. InvisibleFerret is designed to steal sensitive information and operates silently, making it difficult to detect.…
Read More 
This article discusses the evolution of cyber warfare through historical cyberattacks, emphasizing the importance of cybersecurity in the digital age. It highlights ten significant cyber incidents that have shaped our understanding of digital security, the lessons learned, and the ongoing threats organizations face today. Affected: organizations, government, healthcare, energy, transportation, technology sector
Read More Keypoints :
Cyberattacks are malicious attempts to steal, damage, or disrupt computer systems and data.…
This report presents the findings of a study on the Mercedes-Benz User Experience (MBUX) infotainment system, focusing on vulnerabilities and diagnostic subsystems that were not previously addressed. The research highlights various attack vectors, including USB and inter-process communication protocols, and identifies several critical vulnerabilities. Affected: Mercedes-Benz MBUX, automotive sector
Read More Keypoints :
The study analyzes the first-generation MBUX system, emphasizing its architecture and diagnostic capabilities.…