Wiz Threat Research has identified an ongoing campaign by the threat actor JINX-0126, targeting poorly configured and publicly exposed PostgreSQL servers. By exploiting weak login credentials, the actor gains access to deploy XMRig-C3 cryptominers, impacting over 1,500 victims. The attacker employs advanced techniques to evade detection while continuously scanning for vulnerable systems.…
Read More Tag: UNIX
John the Ripper is a powerful hash-cracking tool that efficiently cracks various hash types such as Windows authentication hashes, /etc/shadow hashes, and password-protected files. Through practical tasks, users learn the syntax, features, and methods to conduct dictionary attacks and utilize custom rules. Affected: Windows systems, Linux systems, password-protected ZIP and RAR files
Read More Keypoints :
John the Ripper is a versatile tool for hash cracking.…
Summary: Researchers have uncovered a cryptocurrency mining botnet known as Outlaw, which exploits weak SSH credentials to propagate and control compromised systems. Active since 2018, it utilizes brute-force attacks and a multi-stage infection process to deploy malicious miners and maintain persistence. The botnet also exhibits features for self-propagation and remote control, using IRC channels for command and control operations.…
Read More 
This article discusses various known attack surfaces and potential risks associated with GitLab, highlighting a range of vulnerabilities, including Remote Code Execution (RCE), SSRF, XSS, and permission escalation issues. The information covers the history of vulnerabilities, their impact, and famous cases, emphasizing the importance of security measures for self-managed GitLab instances.…
Read More 
Summary: The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has disclosed the presence of a new malware, RESURGE, targeting vulnerabilities in Ivanti Connect Secure appliances. This malware exploits a recently patched security flaw (CVE-2025-0282) and has capabilities enhancing its evasion and operational effectiveness. It is linked to espionage activities potentially conducted by state-sponsored threat actors.…
Read More
CISA has reported on three malicious files acquired from an Ivanti Connect Secure device compromised through CVE-2025-0282. The files exhibit functionalities similar to known malware, including command and control capabilities and log tampering. RESURGE, the primary file, can modify files and create a web shell. Another file, a variant of SPAWNSLOTH, tampered with logs, while the third one included a shell script that extracts kernel images.…
Read More 
Summary: A critical security vulnerability (CVE-2025-30232) has been discovered in Exim, a popular message transfer agent for Unix systems. This use-after-free vulnerability may allow local privilege escalation under specific conditions. Administrators of affected Exim versions are advised to apply security patches promptly and review their security practices to mitigate risks.…
Read More 
Recent leaks from Black Basta’s internal chat logs highlight the gang’s strategy to leverage open source ecosystems, specifically npm and PyPI, to execute dependency confusion attacks. This research uncovers the threat posed by ransomware attacks and extortionware within these ecosystems, along with examples of historical attacks.…
Read More 
A new variant of XCSSET malware has been discovered, which is specifically designed to infect macOS Xcode projects. This sophisticated malware utilizes advanced obfuscation, updated persistence techniques, and novel infection strategies to exfiltrate sensitive information, including digital wallet data. It operates in a stealthy manner, often remaining fileless, which complicates detection and removal efforts.…
Read More 
This walkthrough provides a detailed guide on tackling the Sunset: 1 Capture The Flag (CTF) challenge, emphasizing skills in web exploitation, enumeration, and privilege escalation. Users navigate various tools and commands to identify and exploit vulnerabilities, ultimately achieving root access. Affected: Vulnerable web platforms
Read More Keypoints :
The Sunset: 1 CTF challenge is designed for skill development in web exploitation and privilege escalation.…
A recent global campaign has been identified that targets TP-Link Archer routers through a remote code execution (RCE) vulnerability (CVE-2023-1389). The campaign exploits these routers to create a botnet, with the potential for widespread impact given the number of vulnerable devices connected to the internet. The malware dropper utilizes a bash script to install and execute additional malware while maintaining evasion techniques.…
Read More 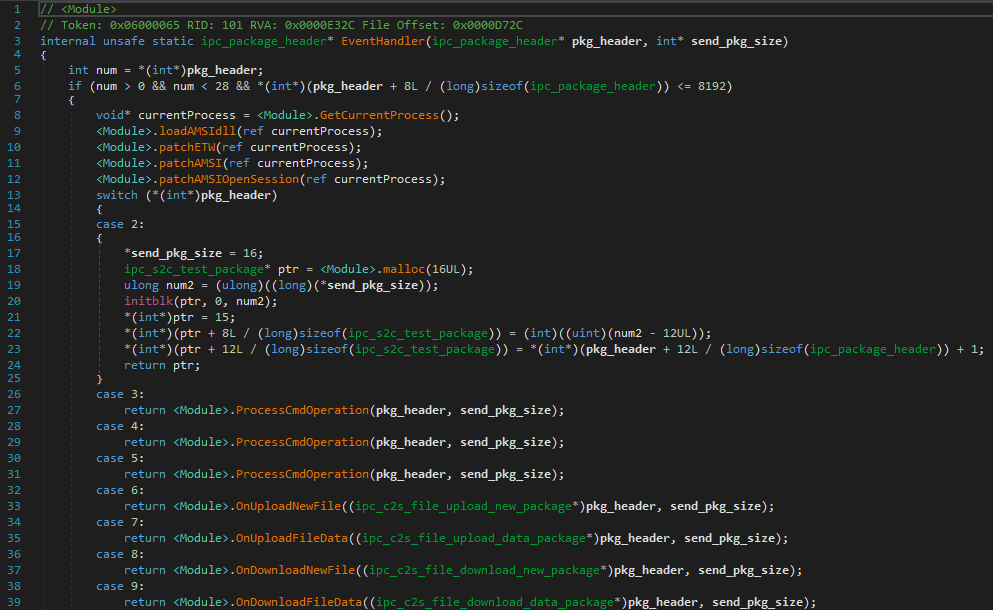
This article discusses three unique malware samples discovered recently: a C++/CLI IIS backdoor, a bootkit that installs a GRUB 2 bootloader, and a post-exploitation framework known as ProjectGeass. Each sample demonstrates unconventional techniques and complexities, highlighting the evolving threat landscape. Affected: IIS, Windows, system environments
Read More Keypoints :
Three unique malware samples discovered exhibiting novel characteristics.…
This report highlights the rise of Ramadan-related cyber scams, particularly targeting charitable contributions and crypto investments. Cybercriminals are exploiting the goodwill associated with Ramadan to spread fraudulent schemes, often using social engineering tactics to deceive victims. Understanding these scams is essential for safeguarding against potential losses.…
Read More 
The article discusses the current cyber threat landscape focusing on various incidents including the risks posed by the Murdoc_Botnet, which targets IoT devices and Unix-like systems, highlighting its infection methods and impact. The report also addresses a new DDoS botnet, Eleven11bot, and a series of cyberattacks on various sectors including Tata Technologies and the Polish Space Agency, along with vulnerabilities discovered in Google’s Android and HPE’s remote management tools.…
Read More 
A recent analysis reveals a sustained malicious campaign targeting the Go ecosystem, utilizing typosquatted packages to distribute loader malware to Linux and macOS systems. At least seven packages were identified as impersonating popular Go libraries, with a significant focus on deception aimed at financial-sector developers. The malware employs obfuscation techniques and has been linked to multiple malicious domains while remaining accessible on Go Module Mirror.…
Read More 
This article explains function hooking using the LD_PRELOAD environment variable, showcasing a hands-on example of modifying a random number guessing game to make it possible to win. It covers the theory behind function hooking, practical implementation, and details on dynamic linking. Affected: Unix-like operating systems, software applications
Read More Keypoints :
Function hooking intercepts and modifies function calls at runtime.…
Summary: A security vulnerability in Webmin versions 2.202 and below allows attackers to bypass SSL certificate authentication, potentially granting unauthorized access to sensitive systems. This flaw arises from Webmin’s mishandling of SSL certificates when remote IP addresses from proxies are trusted. Users are urged to upgrade to version 2.301 or later and to adjust their IP Access Control settings as a precautionary measure.…
Read More 
In November 2024, Solar 4RAYS reported on a malicious campaign targeting Russian IT organizations providing services for the public sector. The group, dubbed Erudite Mogwai by Solar 4RAYS and Space Pirates by Positive Technologies, is utilizing a modified version of the public proxy tool Stowaway. This custom tool, used alongside other malware like ShadowPad Light, demonstrated enhancements and adaptions for unauthorized access against sensitive networks.…
Read More
Summary: The video discusses security audits for web applications, particularly focusing on the challenges faced when testing applications blindly without source code access. It highlights how backend implementation details, such as error messages and unique HTTP headers, can offer valuable insights. The discussion then shifts to a practical example, analyzing a CTF challenge involving a Go web application and uncovering a race condition vulnerability related to error handling in the code.Key…
Read More 
This article concludes the “Linux Persistence Detection Engineering” series by exploring advanced persistence mechanisms in Linux. Key topics include manipulation of GRUB and initramfs for persistence, exploitation of PolicyKit (Polkit) permissions, D-Bus configuration for unauthorized access, and NetworkManager dispatcher scripts. Readers are equipped with practical examples and detection strategies to bolster their defenses against Linux persistence threats.…
Read More