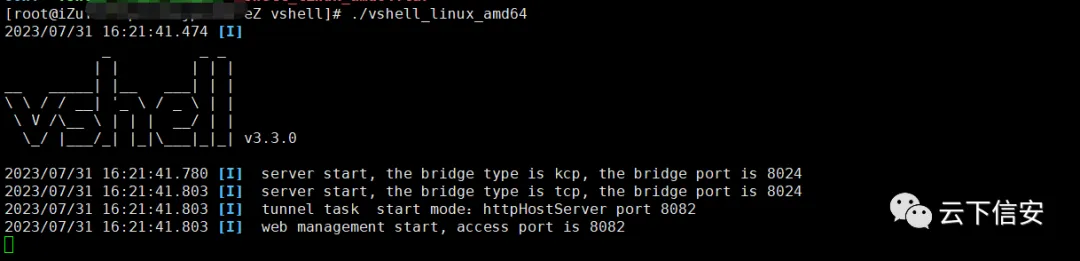
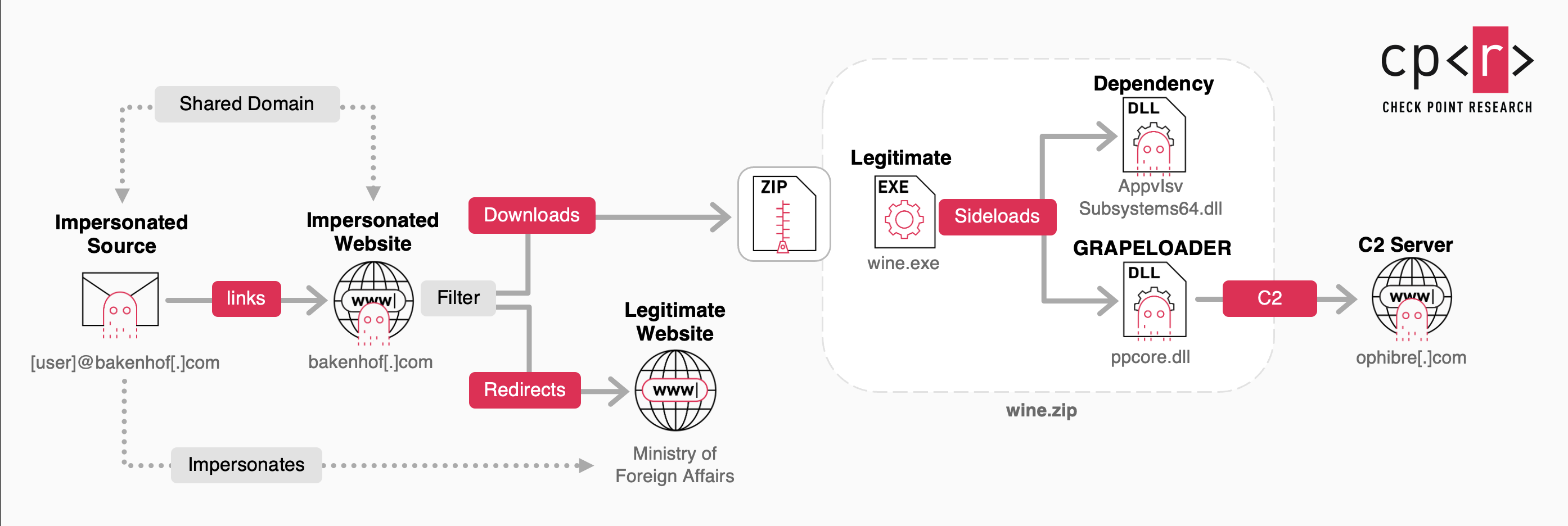
Keypoints :
Dark Caracal has launched a new campaign using the Poco RAT malware.…
Dark Caracal’s latest cyber operation uses Poco RAT, a sophisticated malware targeting Spanish-speaking regions in Latin America, primarily through phishing campaigns. The group employs clever methods to deliver malicious payloads, including trojanized attachments and cloud storage services. Affected: corporate networks, Spanish-speaking users, Latin America
Read More 



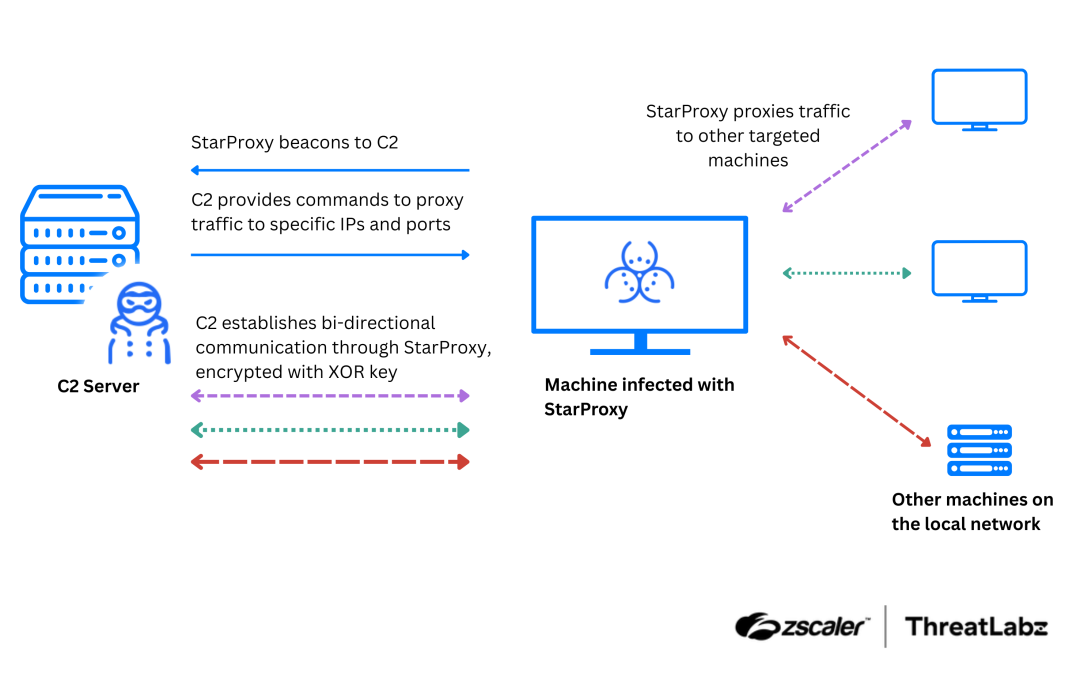




.png)