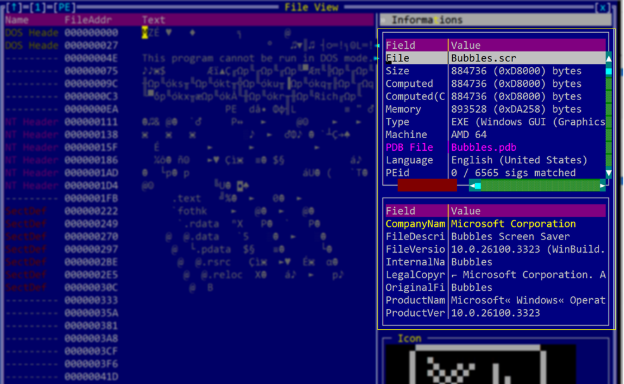
Summary: Ivanti has issued security updates to address a critical remote code execution vulnerability (CVE-2025-22457) exploited by Chinese espionage actors to deploy malware. The vulnerability affects multiple Ivanti products, including older Pulse Connect Secure versions, and was initially misclassified as a bug. Users are urged to update to the latest versions to mitigate risks from active exploitation observed in the wild.…
Read More