Summary: OpenAI’s “Deep Research,” an advanced AI agent, is set to become available for free users shortly, after currently being exclusive to Plus and Enterprise customers. The feature allows users to prompt the AI for in-depth information and analysis on various topics. Detailed rollout timelines and accessibility for free users are still pending confirmation from OpenAI.…
Read More 


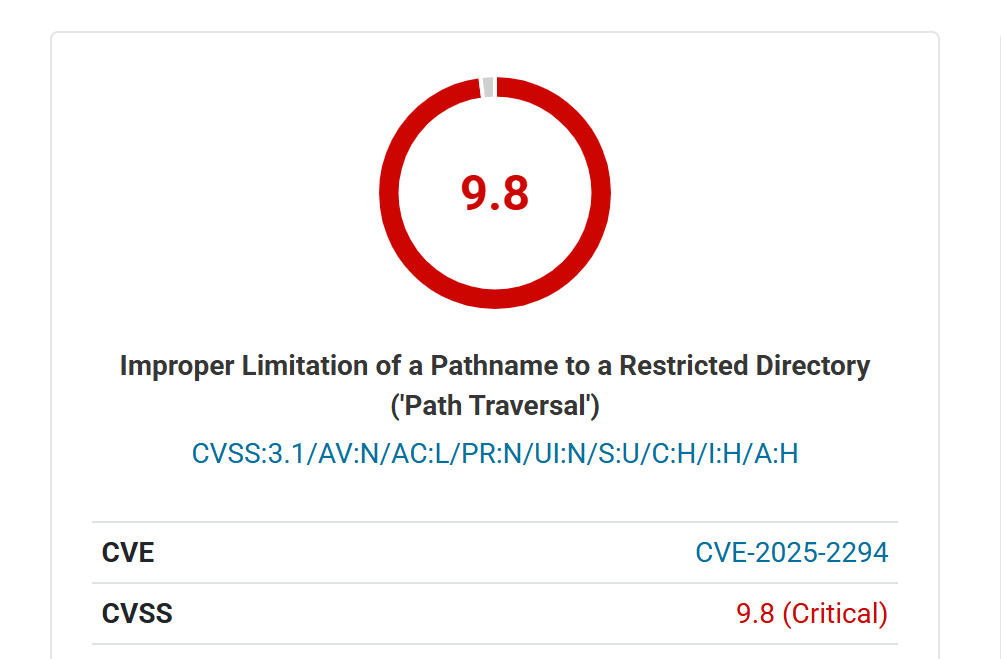


 Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More
Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More