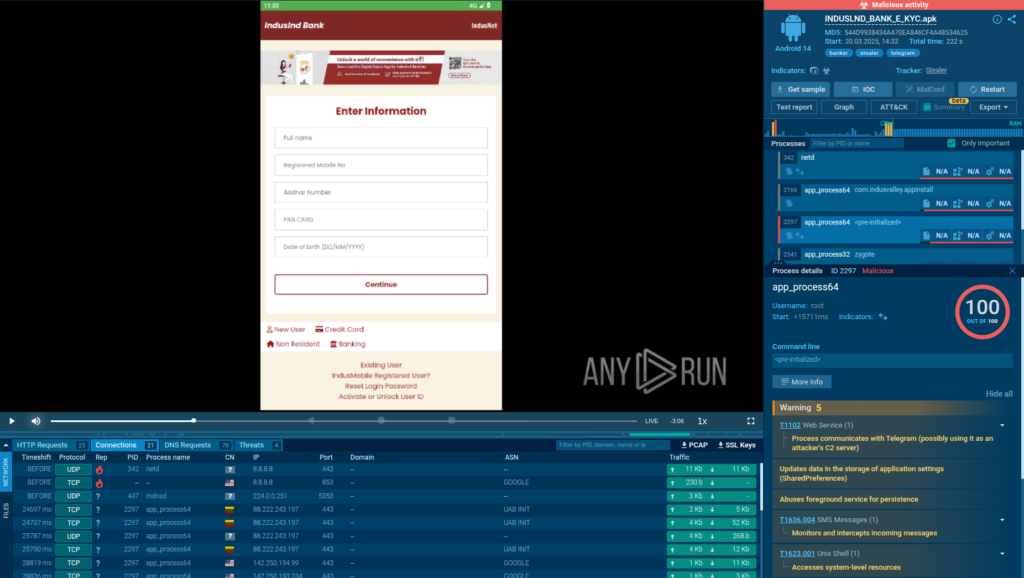
Summary: This article explores the transformative power of Agentic AI in Security Operations Centers (SOCs), emphasizing its autonomy compared to traditional Assistant AI tools. It highlights how Agentic AI automates critical triage and investigation tasks, reducing analyst fatigue while improving operational efficiency and cost-effectiveness. The article also offers key considerations for evaluating Agentic AI solutions to enhance security operations.…
Read More