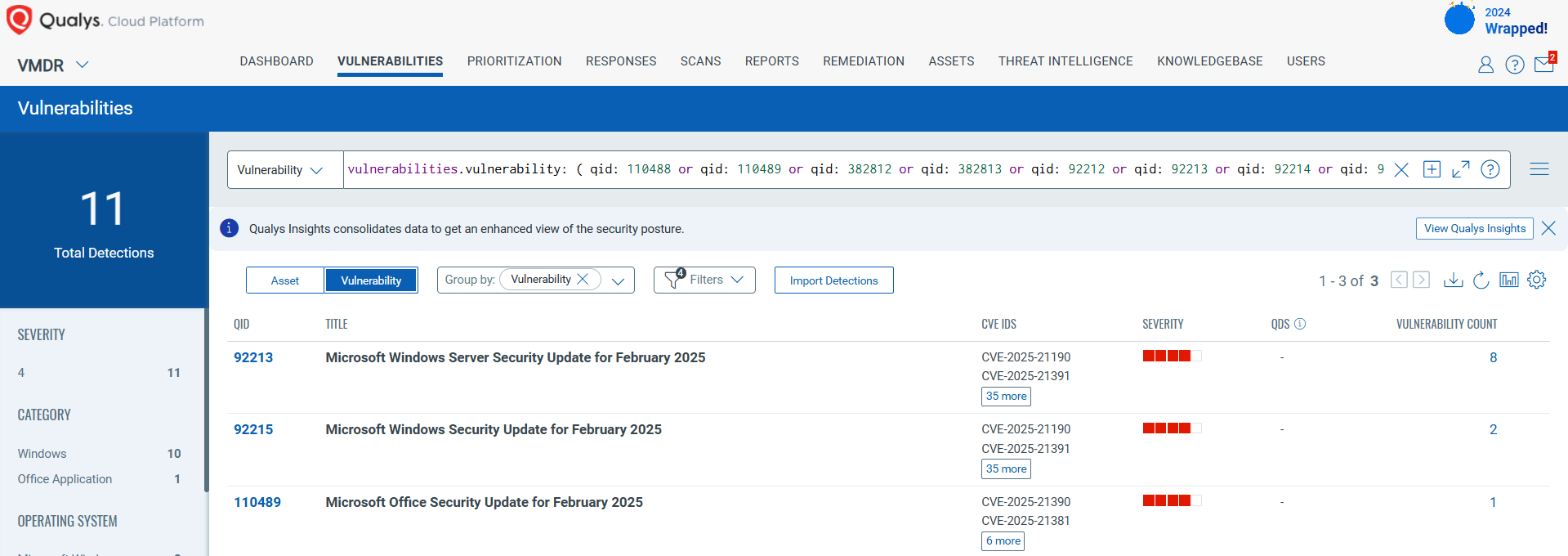
Summary: In 2024, credential stuffing attacks surged due to a blend of infostealer infections and extensive data breaches, marking a troubling trend in cybercrime. The emergence of AI agents, specifically Computer-Using Agents, presents a new challenge, enabling attackers to automate credential exploitation on a large scale without needing extensive coding.…
Read More