
Tag: SQL INJECTION




Attacker: SUKASEPONG01Target: aksi.smpmuhasa.sch.idSource: https://zone-xsec.com/mirror/id/703684
Attacker: SUKASEPONG01Target: explorer.smpmuhasa.sch.idSource: https://zone-xsec.com/mirror/id/703683
Attacker: SUKASEPONG01Target: main.smpmuhasa.sch.idSource: https://zone-xsec.com/mirror/id/703682
Attacker: SUKASEPONG01Target: literasi.smpmuhasa.sch.idSource: https://zone-xsec.com/mirror/id/703681
Attacker: SUKASEPONG01Target: www.ujian.smpmuhasa.sch.idSource: https://zone-xsec.com/mirror/id/703680
Attacker: RidXploitTarget: sibolgakota.go.id/home/wp-cont…Source: https://zone-xsec.com/mirror/id/703679
Attacker: ./FreedomXploitTarget: sid.banyumaskab.go.id/desa/upl…Source: https://zone-xsec.com/mirror/id/703588
Attacker: D0R4H4X0RTarget: gimnasionuevaamerica.edu.co/5….Source: https://zone-xsec.com/mirror/id/703586
Attacker: KenzoXploitTarget: mooc.ba.rmuti.ac.th/log/index….Source: https://zone-xsec.com/mirror/id/703573
Attacker: KaiyoTarget: cdvdna.edu.vn/vi/khoadien/tran…Source: https://zone-xsec.com/mirror/id/703572
Attacker: RidXploitTarget: sibolgakota.go.id/home/wp-content/uploads/2025/…Source: https://defacer.id/mirror/id/140185
Attacker: SUKASEPONG01Target: aksi.smpmuhasa.sch.id/Source:…


_Elena_Uve_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)
Keypoints :
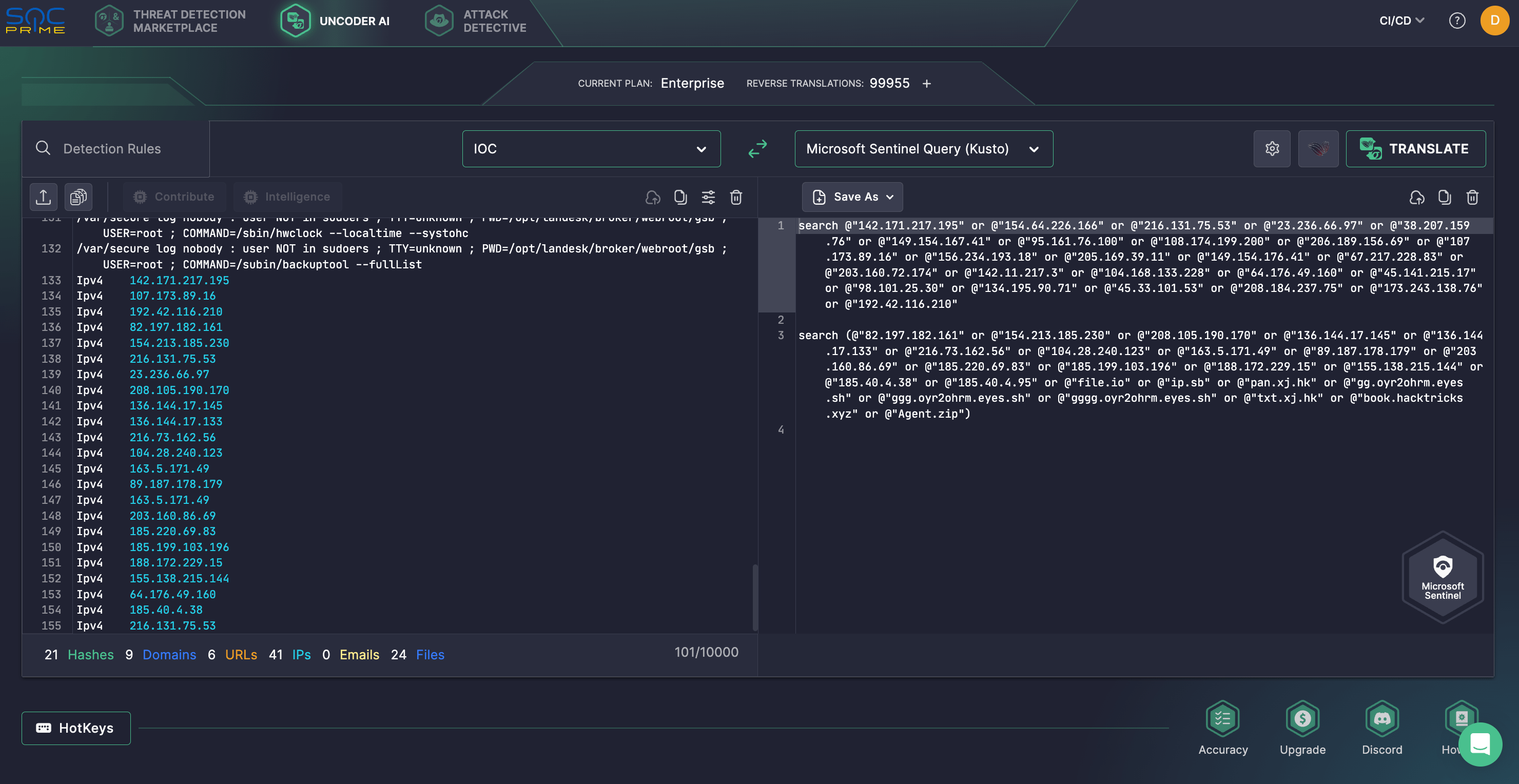
Ivanti Cloud Service Appliances (CSAs) face critical vulnerabilities tracked as CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380.…
Keypoints :
A zero-day vulnerability identified as CVE-2025-23006 was disclosed by SonicWall.…


Keypoints :
Cyble Research and Intelligence Labs (CRIL) analyzed vulnerabilities disclosed between January 8 and 14, 2025.…
