Summary: On April 22, 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released five urgent advisories addressing critical vulnerabilities in Industrial Control Systems (ICS) from Siemens, ABB, and Schneider Electric. These advisories highlight severe risks that could lead to data theft, operational disruption, and safety incidents, necessitating immediate attention from security personnel.…
Read More Tag: SQL INJECTION

GrapeQL is a dedicated security testing tool for GraphQL applications, enabling detection of vulnerabilities like Remote Code Execution, SQL injection, and denial-of-service attacks. It automates testing and generates detailed reports to assist developers and security researchers in fortifying APIs. Affected: GraphQL applications, APIs
Read More Keypoints :
GrapeQL is designed specifically for testing modern GraphQL applications.…
Summary: A recent report by Cyble highlights the shift in hacktivist tactics towards advanced attacks targeting critical infrastructure and the integration of ransomware into politically motivated operations. This evolution demonstrates hacktivist groups adopting methods similar to those of nation-state actors, posing significant threats to national resilience.…
Read More 
The rise in advanced cyber threats is attributed to sophisticated vulnerabilities that attackers exploit, including zero-day exploits and supply chain compromises. This trend highlights the need for organizations to enhance their defenses and embrace continuous threat exposure management (CTEM) to stay ahead of attackers. Affected: organizations, critical infrastructure, software supply chains, cloud services, end-users
Read More Keypoints :
2023 saw a rise in zero-day exploits, with 97 reported in the wild compared to 62 in 2022.…
In February 2025, 13 hacking groups were identified, engaging in various cybercrimes including ransomware distribution, phishing attacks, and identity theft through sophisticated techniques. Each group employed unique methods to compromise targets and steal valuable information or funds, affecting numerous sectors globally. Affected: government, e-commerce, social media, enterprise security, individual users
Read More Keypoints :
SectorJ09 used formjacking to steal financial information from e-commerce sites.…Summary: The video discusses the integration of AI into Burp Suite, a web application security testing tool, and highlights its advantages in finding web application vulnerabilities more efficiently. The presenter, John Hammond, demonstrates how to set up Burp Suite Professional, leverage AI-powered features, and perform vulnerability scanning using the provided “Jin and Juice Shop,” an intentionally vulnerable web application for testing.…
Read More 
Summary: Swiss cybersecurity firm Prodaft has initiated a program called ‘Sell your Source,’ aimed at acquiring verified accounts from hacking forums to enhance intelligence on cybercriminal activities. The initiative seeks to penetrate cybercrime networks while ensuring rigorous verification of account history and legality. Prodaft’s efforts are touted as a method to improve visibility and combat adversarial cyber threats effectively.…
Read More 
This guide outlines a strategic security approach for Software-as-a-Service (SaaS) applications, focusing on five key pillars: Identity and Access Management (IAM), Data Protection, Secure Development, Network Security Controls, and Incident Response & Monitoring. It emphasizes the need for adopting Zero Trust principles and aligns each security pillar with established industry standards.…
Read More
In the Persistence stage of the MITRE ATT&CK framework, attackers establish footholds within systems to maintain access. They may create scheduled tasks that run malicious scripts and add new accounts to preserve their entry even if passwords change. The article discusses the procedures for identifying these actions through log file analysis and the technical implementations involved.…
Read More 
ReliaQuest’s report analyzed incidents from December 2024 to February 2025, revealing a surge in attacks by financially motivated actors targeting vulnerabilities in external remote services and internal phishing tactics. Key findings include increased VPN brute-forcing, MSHTA command abuses, and advancements in malware. Recommendations for improved cyber defenses include enabling specific detection rules and enhancing employee training against phishing.…
Read More 
This article discusses how AI can be leveraged for ethical hacking to escalate vulnerabilities in web applications. The author shares a personal experience of using ChatGPT to conduct mass reconnaissance, identify SQL injection vulnerabilities, and successfully escalate to remote file inclusion attacks. The narrative emphasizes the transformative power of AI in bug bounty hunting.…
Read More 
Summary: UK-based Halo recently addressed a significant SQL injection vulnerability in its IT service management software, HaloITSM, which could have allowed unauthorized access to sensitive data. Approximately 1,000 cloud deployments were potentially at risk, exposing critical systems to remote attacks. The vendor has released patches to mitigate the threat and advises on-premises users to update promptly.…
Read More 
Summary: A recent Patchstack report reveals critical vulnerabilities in several WordPress plugins that hackers exploited in early 2025. The report highlights four significant flaws that, despite being fixed in 2024, remain unpatched in numerous installations, leaving many sites at risk. It emphasizes the importance of applying security updates and using effective website security measures to mitigate risks.…
Read More 
Summary: Apache VCL is facing critical security vulnerabilities, including an SQL injection flaw and a cross-site scripting (XSS) vulnerability. These flaws could lead to unauthorized data manipulation and system compromises. Immediate upgrading to version 2.5.2 is recommended to address these issues.
Read More Affected: Apache VCL versions 2.1 through 2.5.1
Keypoints :
Critical SQL injection vulnerability identified in the New Block Allocation form (CVE-2024-53678).…
Biotech firms, holding sensitive data such as patient genomes and drug formulas, are prime targets for cyberattacks due to their high value. Cybercriminals can exploit such data for financial gain, leading to risks that include compromised patient safety and legal penalties. Biotech penetration testing is crucial to safeguard against these threats, simulating attacks to identify and mitigate vulnerabilities in systems critical to research and patient data.…
Read More
SQL Injection remains a significant vulnerability in web applications, allowing attackers to compromise databases. This guide introduces SQLMAP, a robust tool that automates the detection and exploitation of SQL Injection vulnerabilities through practical examples. Key topics include types of SQL Injection, commands for using SQLMAP effectively, and methods for bypassing security measures like Web Application Firewalls.…
Read More
Hunt researchers exposed a web server hosting tools linked to an intrusion campaign against South Korean organizations. This server, available for less than 24 hours, encompassed a Rust-compiled Windows executable that deployed Cobalt Strike Cat along with several other open-source tools. The attacker appears to have focused on exploiting vulnerabilities in government and commercial entities.…
Read More 
Summary: Hunt researchers have detected a sophisticated cyber intrusion campaign focusing on South Korean organizations, utilizing modified Cobalt Strike tools and various open-source exploitation tools. The attackers leveraged a publicly exposed web server to distribute their malware and gather intelligence on over 1,000 Korean domains, targeting government and commercial entities.…
Read More 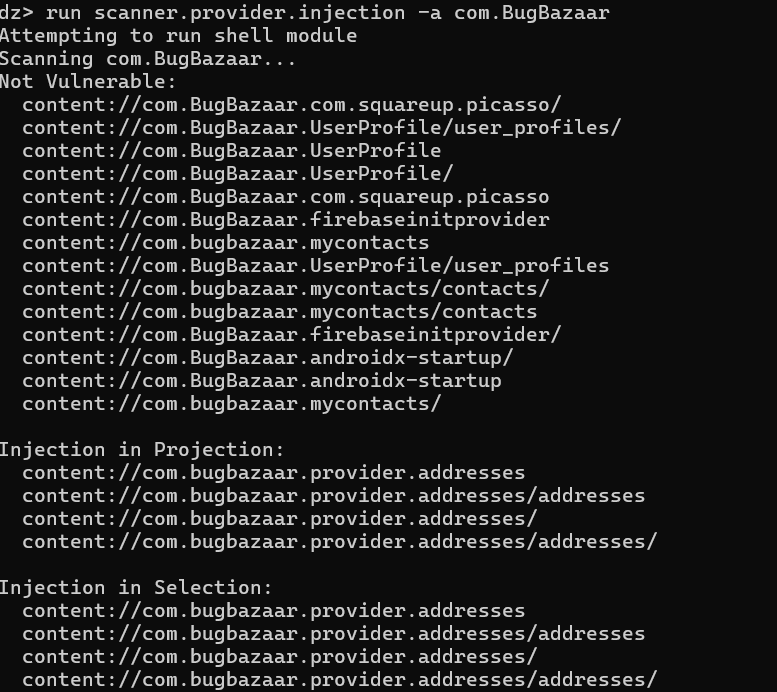
This blog explains how to detect SQL injection vulnerabilities in an Android app’s content provider using Drozer. Content providers manage app data and control access to it, allowing secure interactions with data. The article provides a step-by-step guide for exploiting these vulnerabilities to gain unauthorized access to data.…
Read More
Summary: The popular WordPress security plugin WP Ghost is found to have a critical vulnerability that could enable unauthenticated attackers to execute remote code and take control of compromised servers. This vulnerability, identified as CVE-2025-26909, impacts all versions up to 5.4.01 and arises from insufficient input validation.…
Read More