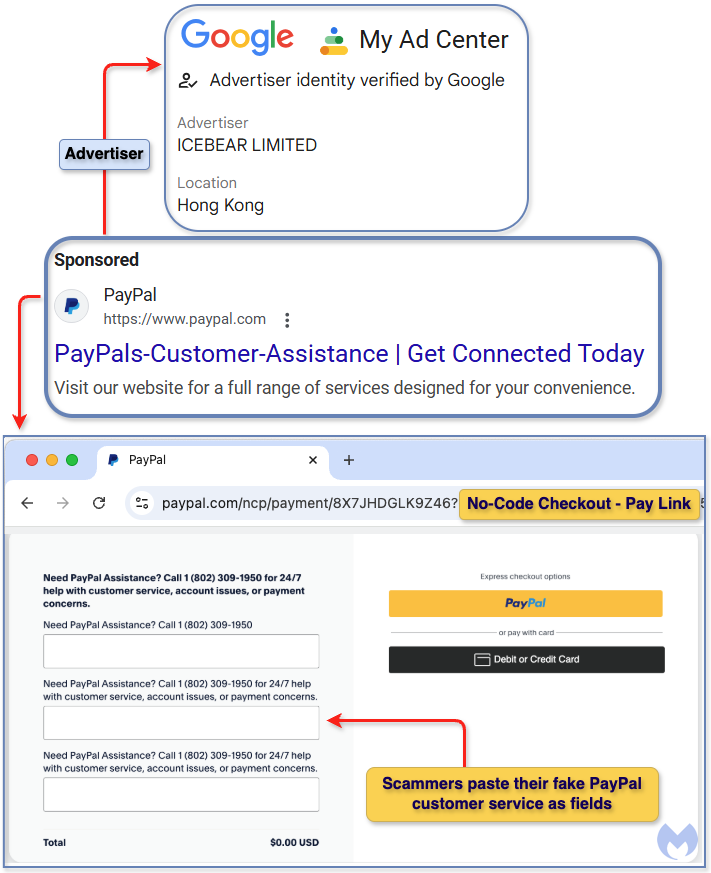
A phishing campaign identified by Microsoft Threat Intelligence targets the hospitality industry, impersonating Booking.com and utilizing the ClickFix social engineering technique to deliver credential-stealing malware. The campaign, ongoing since December 2024, aims at financial fraud by tricking users into executing malicious commands. Affected: hospitality organizations, Booking.com…
Read More