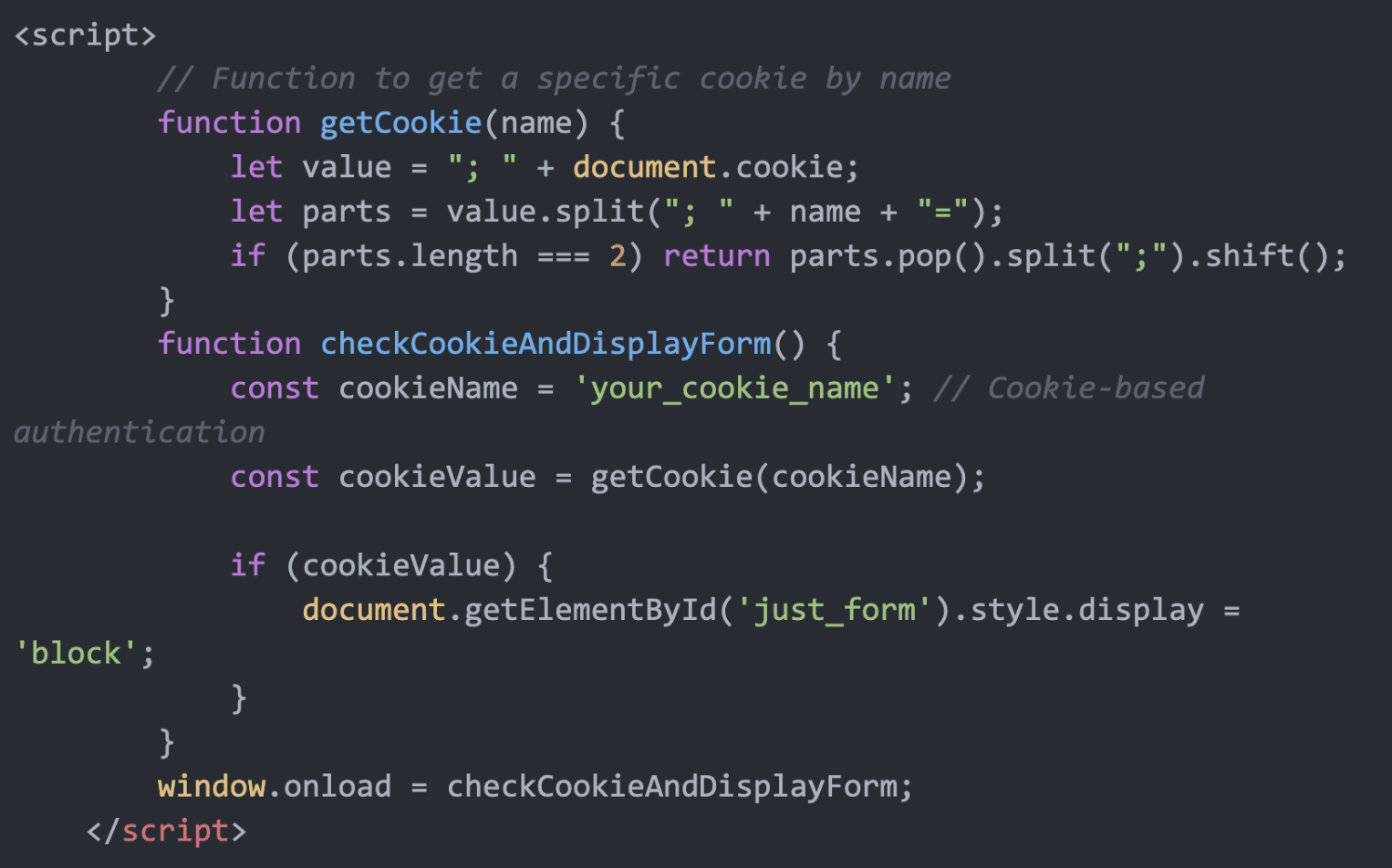
Summary: The report by Prodaft reveals the emergence of Phishing-as-a-Service (PhAAS) platforms, particularly focusing on the Lucid platform operated by Chinese-speaking threat actors. This platform facilitates large-scale phishing attacks targeting individuals and organizations worldwide through sophisticated mechanisms that exploit messaging technologies. The rise of such platforms underscores a growing threat landscape, intensifying the risks associated with financial cybercrime and the need for enhanced security measures.…
Read More