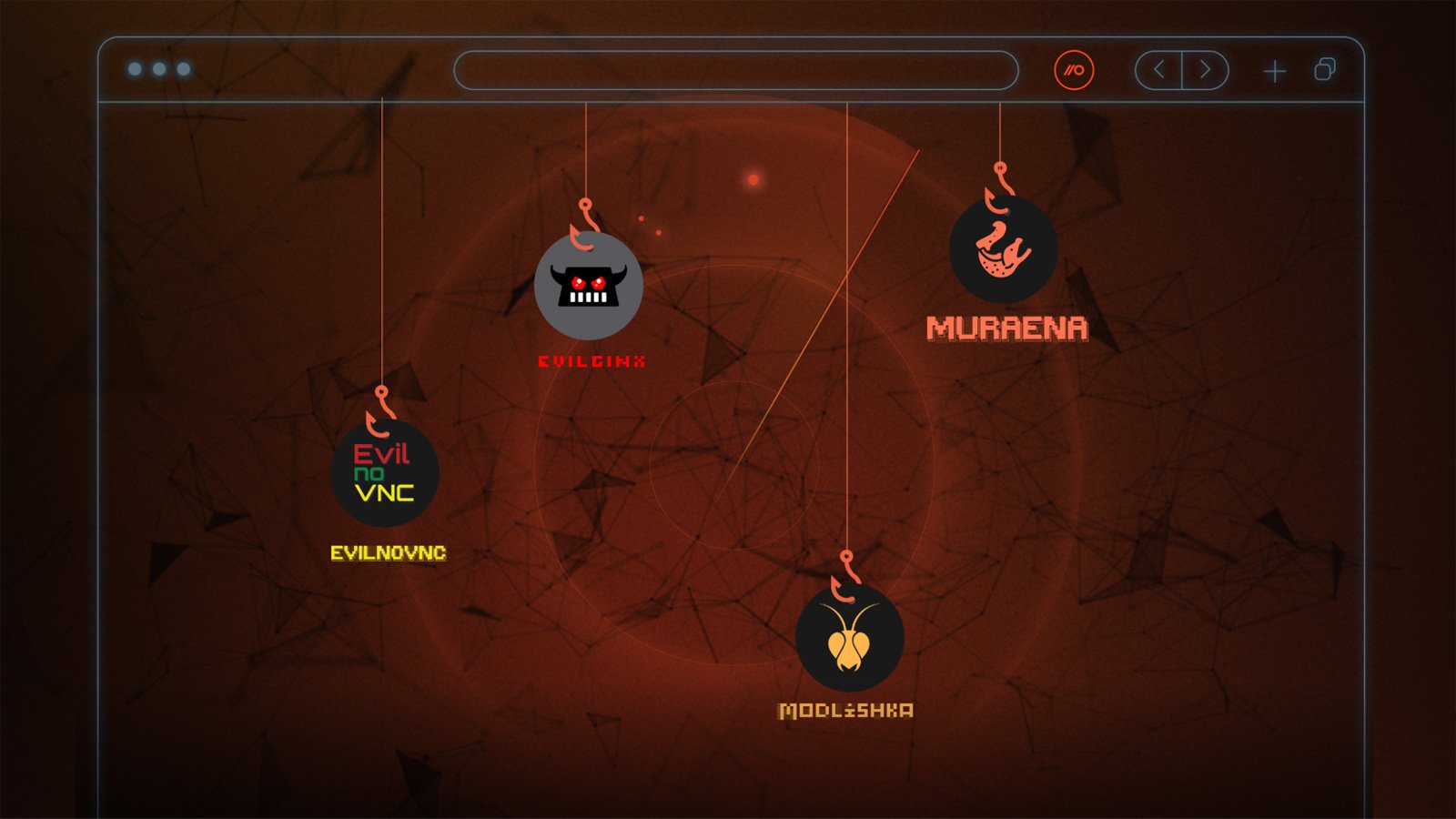
Summary: Despite significant investments in email security solutions, phishing attacks continue to pose a severe threat to organizations, largely due to the emergence of sophisticated Attack-in-the-Middle (AitM) phishing techniques. Traditional detection methods, including known-bad blocklists and malicious webpage detection, are increasingly ineffective against these evolving tactics.…
Read More