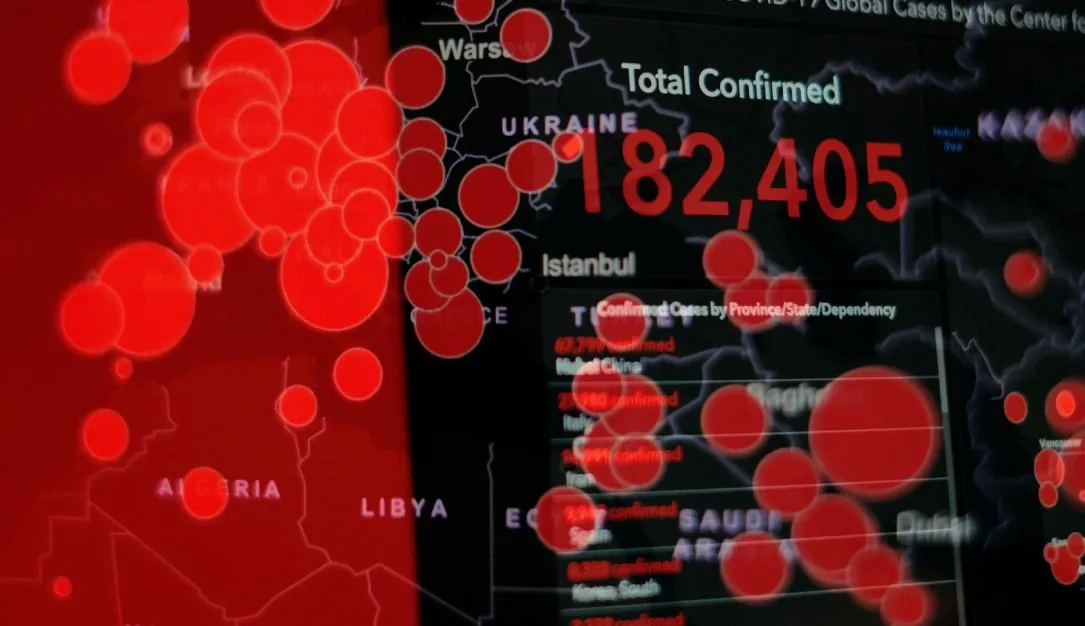
Summary: Research indicates that operators of DragonForce and Anubis ransomware-as-a-service are evolving their business models to attract more affiliates, akin to strategies used in legitimate businesses. By adopting new collaborative frameworks and monetization methods, they aim to increase their market share, but these developments come with shared risks among affiliates.…
Read More 



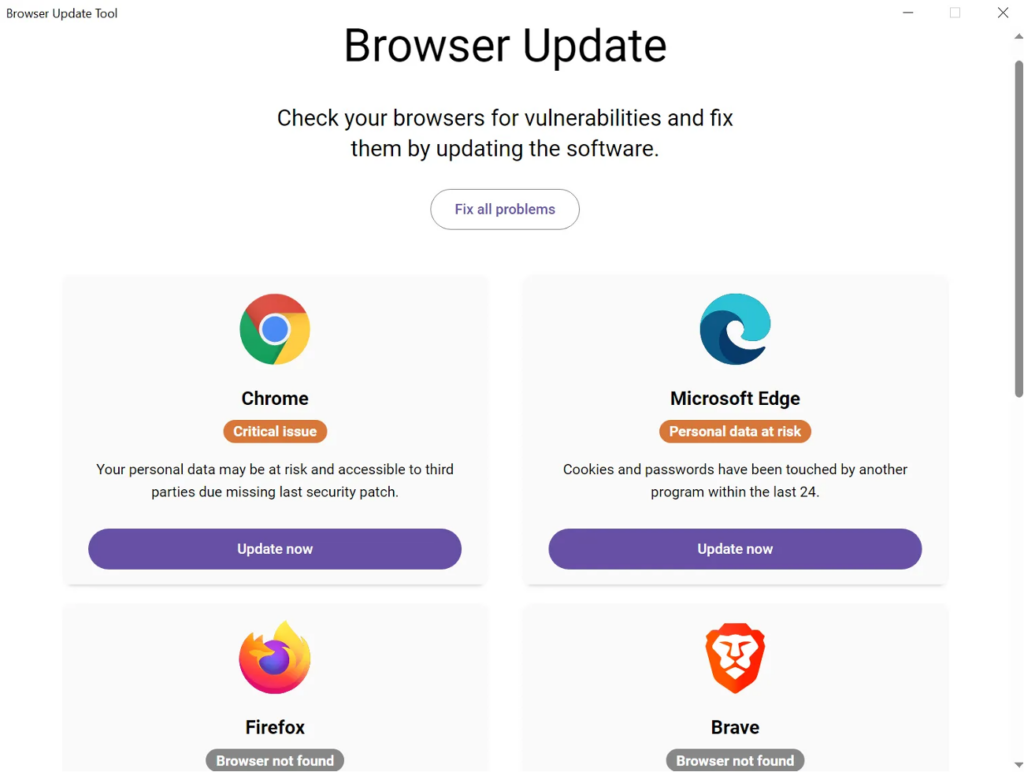




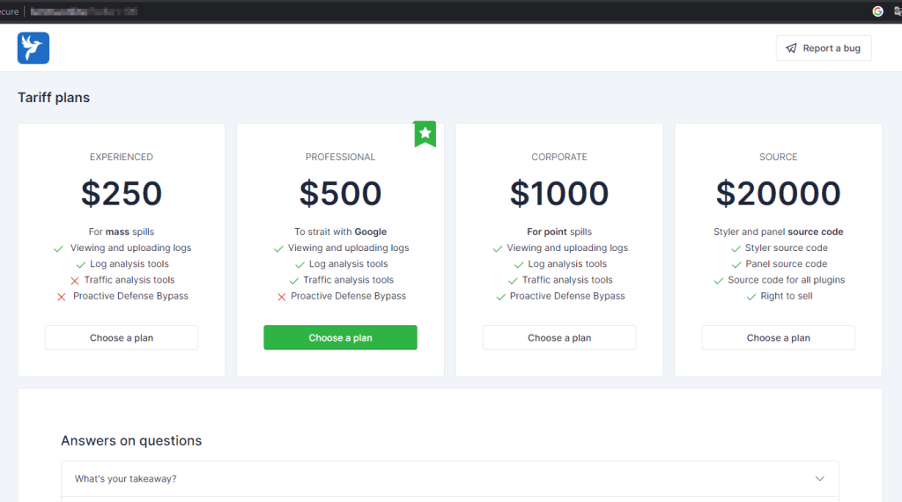


 THN Weekly Recap: iOS Zero-Days, 4Chan Breach, NTLM Exploits, WhatsApp Spyware & More
THN Weekly Recap: iOS Zero-Days, 4Chan Breach, NTLM Exploits, WhatsApp Spyware & More