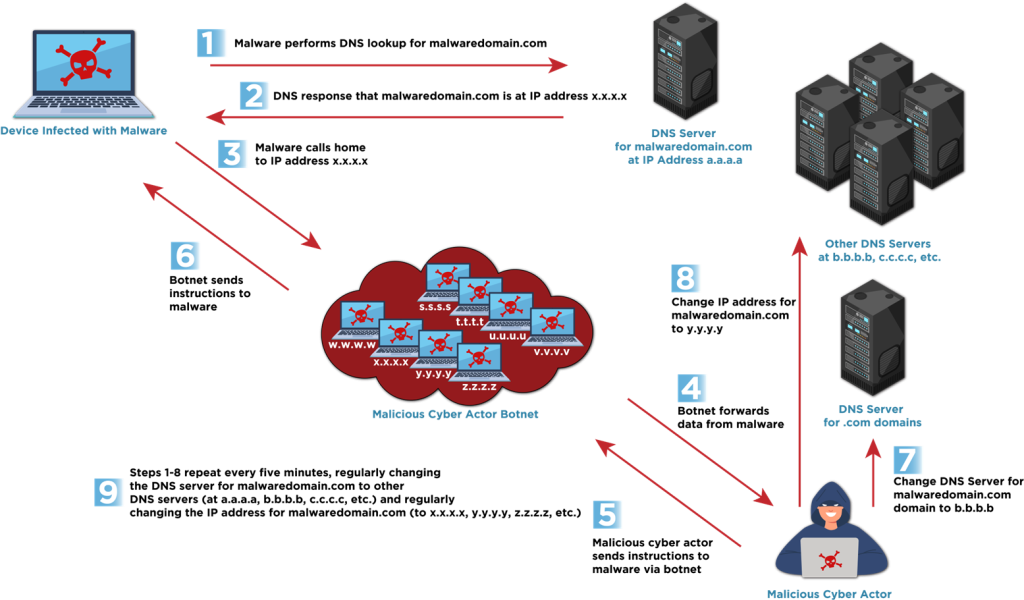
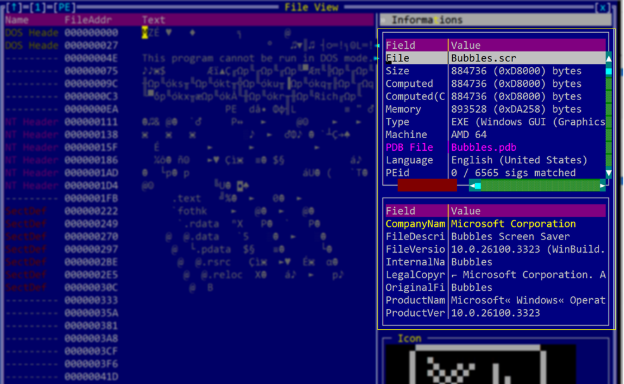
This article outlines a sophisticated multi-stage cyber attack characterized by the use of vishing, remote access tools, and legitimate software exploitation to gain unauthorized access and maintain persistence. The attack involved delivering malicious payloads through Microsoft Teams, using Quick Assist for remote access, and deploying malware including TeamViewer and a JavaScript-based command and control backdoor.…
Read More