The Lotus Blossom, also known as Lotus Panda, is a sophisticated Chinese APT group involved in cyber espionage for over a decade. They have recently enhanced their tactics by deploying new Sagerunex backdoor variants that utilize third-party cloud services and social media for command-and-control activities. This article examines their tactics, techniques, and procedures, detailing their operational framework along with the challenges we face against such persistent threats.…
Read More Tag: SOCIAL ENGINEERING

Summary: A new campaign utilizing the PJobRAT Android malware has been detected, targeting users in Taiwan under the guise of chat applications. This malware, previously aimed at Indian military personnel, has evolved to harvest sensitive information while masquerading as messaging apps. Security researchers indicate its operation spanned nearly two years before pausing in October 2024.…
Read More 
Recent social engineering tactics have evolved to include a variant of the SectopRAT malware, which is disguised as a Cloudflare verification challenge. This Remote Access Trojan employs extensive techniques for data exfiltration and uses various evasion methods to avoid detection. Affected: Users, Browsers, Cryptocurrency Holders
Read More Keypoints :
ClickFix-style social engineering techniques are becoming more prevalent among threat groups.…Summary: The video discusses the increasing significance of AI in cybersecurity, particularly how it is blurring the lines between real and fake, making it challenging to distinguish genuine profiles from AI-generated ones. The hosts interview Andre, co-founder and CEO of Brightside AI, who shares insights on combating the misuse of AI for malicious purposes and discusses the company’s innovative approach to cybersecurity, targeting social engineering attacks while promoting employee privacy and safety.…
Read More 
Summary: The Russian-speaking hacking group RedCurl has been identified for the first time as launching a ransomware campaign using a new strain named QWCrypt. Historically known for corporate espionage attacks, RedCurl’s latest activities include sophisticated social engineering tactics to deploy malware and encrypt virtual machines, severely disrupting their targets.…
Read More 
This report reveals a sophisticated malware campaign targeting YouTube creators through spearphishing, utilizing the Clickflix technique to deceive victims into executing malicious scripts. Attackers leverage brand impersonation and exploit interest in professional collaborations to spread malware via meticulously crafted phishing emails. Once activated, the malware steals sensitive data or allows remote access.…
Read More 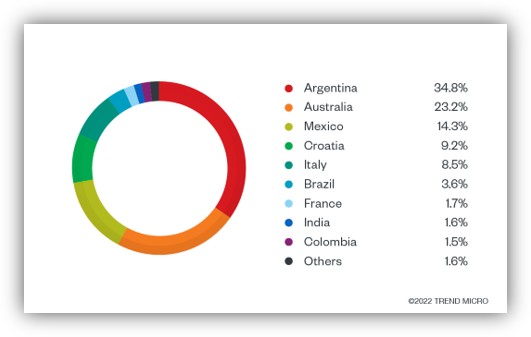
The article discusses the ongoing threat posed by Raspberry Robin, a sophisticated initial access broker (IAB) linked to various cybercriminal organizations, particularly those connected to Russia. It highlights recent findings such as the discovery of nearly 200 unique command and control domains, the involvement of Russian GRU’s Unit 29155, and the threat actor’s evolution in attack methodologies.…
Read More 
Summary: A threat actor named EncryptHub has exploited a Microsoft Management Console vulnerability (CVE-2025-26633) to conduct Windows zero-day attacks, allowing them to bypass security features and execute malicious code. Researchers from Trend Micro reported multiple delivery methods and certifications used in these attacks, with indications of ongoing development of these techniques.…
Read More 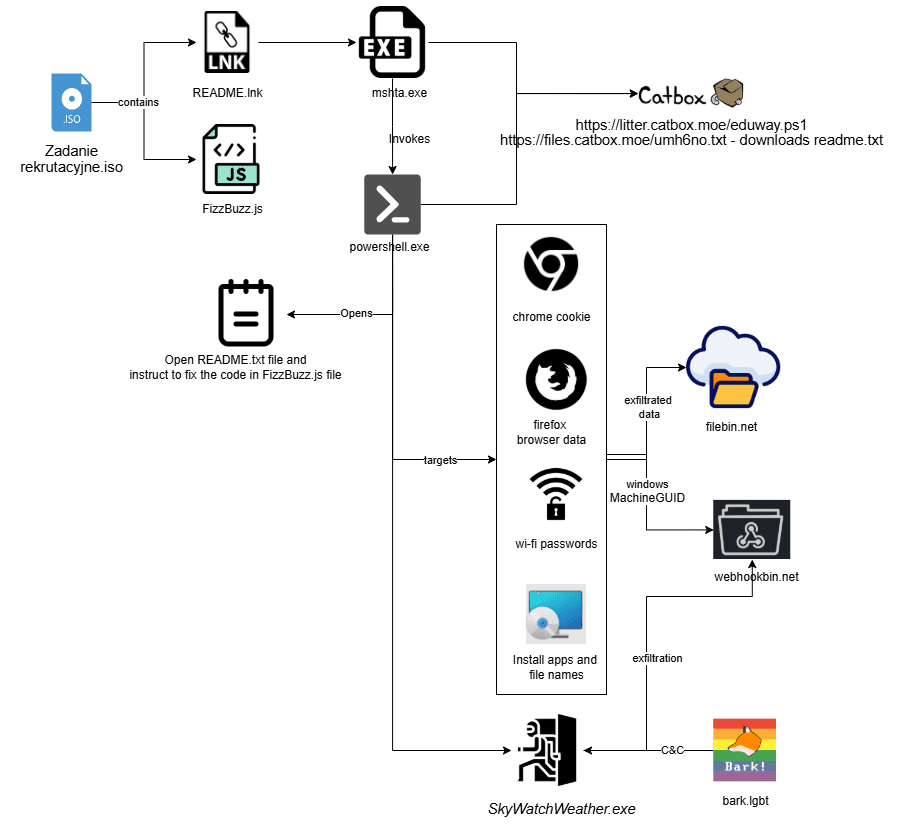
A targeted social engineering campaign has emerged, with a GitHub repository posing as a coding challenge aimed specifically at Polish-speaking developers. The campaign utilizes a malicious ISO file that, when executed, installs a backdoor called “FogDoor,” which collects sensitive information and communicates with a social media platform to execute commands.…
Read More 
The article discusses a financially motivated cybercriminal campaign utilizing a malicious driver known as ABYSSWORKER, which disables endpoint detection and response systems to deploy MEDUSA ransomware. This driver exploits revoked certificates and incorporates various evasion techniques against EDR systems while showcasing its capabilities to manipulate processes and files.…
Read More Summary: The video discusses the importance of securing company data on unmanaged apps and devices, highlighting that traditional access management (AM) and mobile device management (MDM) solutions fall short. One password introduces Extended Access Management as a solution. Additionally, the video previews the Identiverse 2025 event and delves into current enterprise security news, covering various funding rounds, cyber incidents, and the challenges of integrating AI in security operations.…
Read More
Summary: Cybersecurity researcher Vitaly Simonovich demonstrated that it is alarmingly easy to bypass safety features in ChatGPT and similar LLM chatbots to produce malware. By engaging in role-play scenarios, he managed to get the AI to create malware capable of breaching Google Chrome’s Password Manager. This raises concerns about the growing threat landscape as generative AI tools become more accessible to potential cybercriminals.…
Read More 
Summary: INTERPOL’s ‘Operation Red Card’ has led to the arrest of 306 suspects across seven African countries targeting cybercriminal networks. The operation resulted in the seizure of 1,842 devices involved in various scams affecting over 5,000 victims. This initiative highlights the importance of international cooperation in combating cybercrime and protecting communities.…
Read More 
Summary: HP’s latest Threat Insights Report highlights a rise in malicious CAPTCHA campaigns that deceive users into executing PowerShell commands, leading to the installation of the Lumma Stealer remote access trojan (RAT). The report emphasizes the dangers of increased click tolerance among users and outlines various tactics used by attackers, including the distribution of other RATs through social engineering.…
Read More 
Summary: The EU-SOCTA 2025 report from Europol reveals that organized crime in Europe is evolving dramatically due to hybrid threats and the integration of artificial intelligence (AI) into criminal tactics. This shift necessitates a reevaluation of traditional crime-fighting methods and highlights the urgency for proactive measures against diverse and complex threats.…
Read More 
Summary: Europol has dismantled a criminal network that executed a €6.7 million healthcare subsidy fraud against France’s public health insurance system, utilizing fake diplomas and stolen patient data. The operation, which began in July 2024, involved fictitious businesses billing for non-existent hearing aids and laundering funds through shell companies across Europe.…
Read More 
Summary: The Cloak ransomware group has executed a cyberattack on the Virginia Attorney General’s Office, leading to significant disruptions in their computer systems and services. Following the attack, Cloak claimed responsibility and released purportedly stolen data on their leak site. This incident marks Cloak’s first confirmed attack in 2023, amid an increasing number of victims since the group’s emergence.…
Read More 
Summary: CERT-UA warned about targeted cyberattacks against Ukraine’s defense-industry employees and Armed Forces, linked to the UAC-0200 identifier. These attacks utilize the DarkCrystal RAT malware, employing social engineering tactics primarily through the Signal messaging app to distribute malicious files. The campaign has evolved to target specific military technologies, necessitating heightened vigilance within the defense sector.…
Read More 
Summary: Browser security is becoming increasingly critical due to a 140% rise in phishing attacks, primarily fueled by zero-day vulnerabilities and advancements in generative AI used by cybercriminals. As attackers adopt sophisticated techniques akin to professional engineering, the risk of browser-based phishing is expected to escalate dramatically moving into 2025.…
Read More Summary: The video discusses a wide range of security topics including the age verification dilemma, a bogus employee scheme tied to North Korea, a potential Bluetooth backdoor vulnerability discovered in popular chips, and the implications of these findings within the context of cybersecurity. Steve Gibson, the host, highlights the nature of undocumented commands found in Bluetooth chips and explains the misinterpretation of these findings as a true “backdoor.”…
Read More