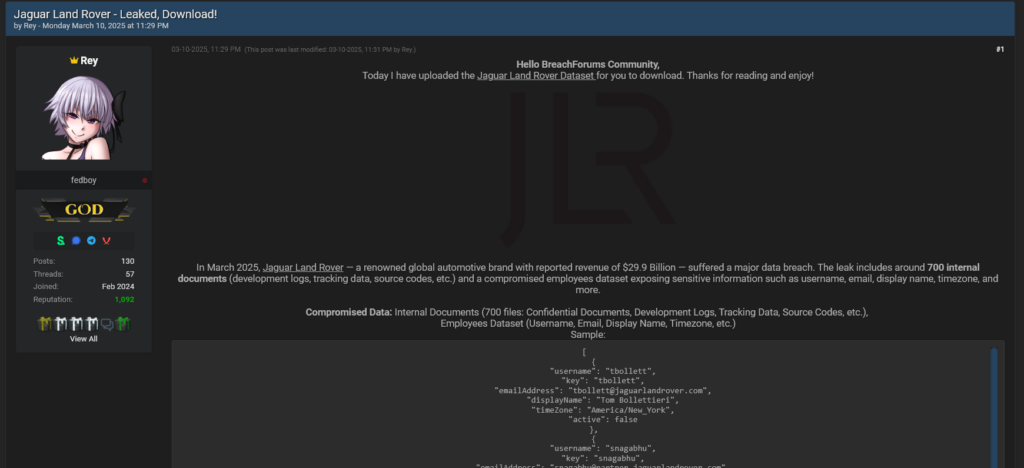
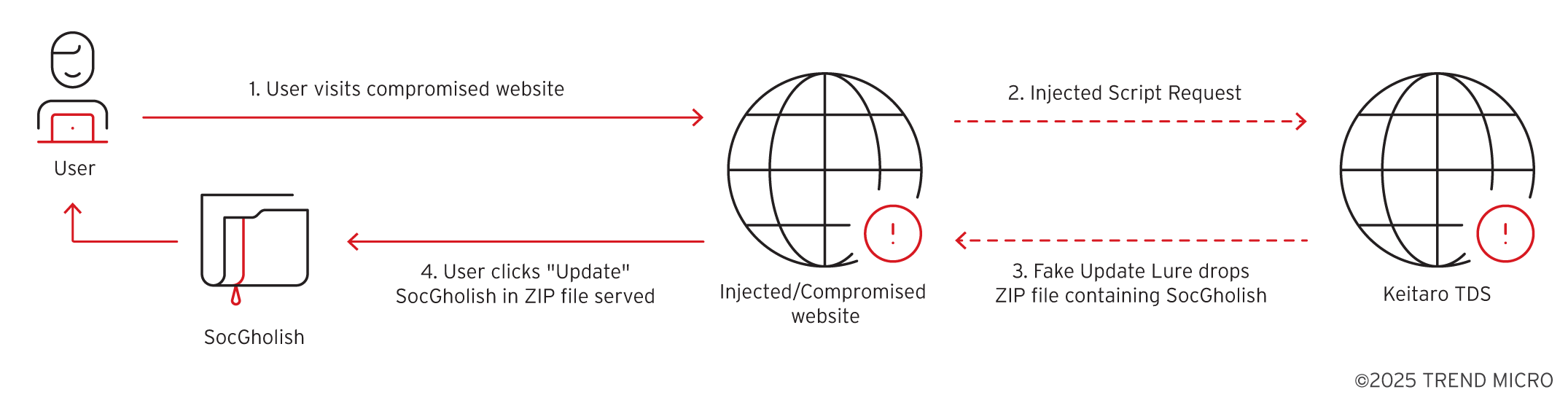
Summary: Browser security is becoming increasingly critical due to a 140% rise in phishing attacks, primarily fueled by zero-day vulnerabilities and advancements in generative AI used by cybercriminals. As attackers adopt sophisticated techniques akin to professional engineering, the risk of browser-based phishing is expected to escalate dramatically moving into 2025.…
Read More 




 THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More