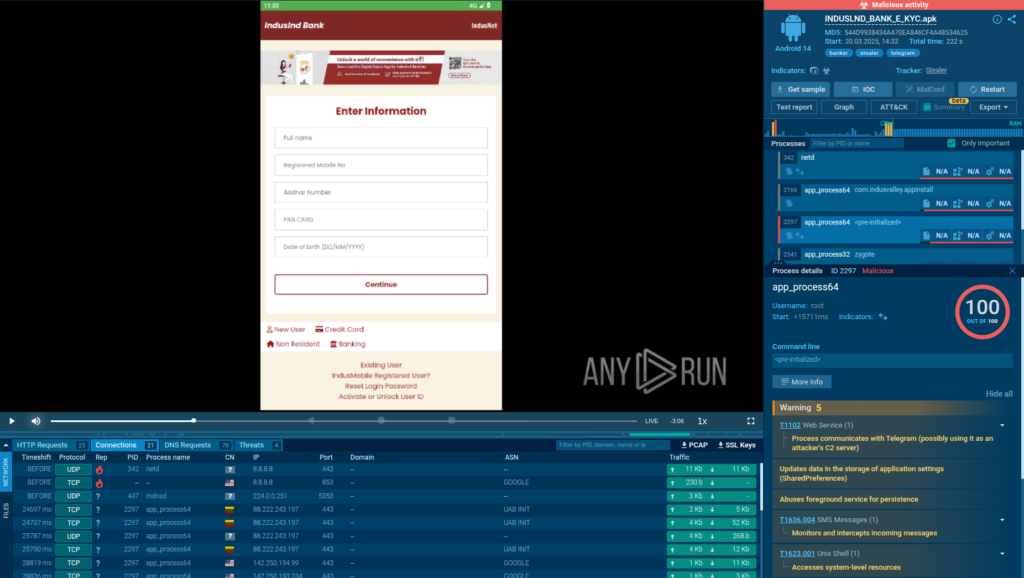
This guide outlines a strategic security approach for Software-as-a-Service (SaaS) applications, focusing on five key pillars: Identity and Access Management (IAM), Data Protection, Secure Development, Network Security Controls, and Incident Response & Monitoring. It emphasizes the need for adopting Zero Trust principles and aligns each security pillar with established industry standards.…
Read More