
Tag: SIEM


Threat Actor: Shadow AI Users | shadow AI users Victim: Organizations | organizations
Key Point :
Shadow AI refers to unauthorized use of AI tools within organizations, increasing data security risks.…
Keypoints :
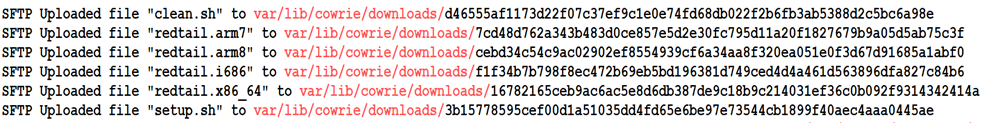
redtail is a cryptocurrency mining malware that stealthily installs itself on compromised systems.…

Threat Actor: CryptBot Operators | CryptBot Operators Victim: Users of Cracked Software | users of cracked software
Key Point :
CryptBot is primarily distributed through fake cracked software and Pay-Per-Install solutions like PrivateLoader.…Keypoints :
Info stealers are subtle but dangerous threats in the cybersecurity landscape.…Summary: Cross-domain attacks are increasingly being utilized by adversaries to exploit vulnerabilities across interconnected environments, emphasizing the critical need for a unified approach to identity security. Organizations must move beyond fragmented solutions to effectively defend against these sophisticated threats.
Threat Actor: SCATTERED SPIDER, FAMOUS CHOLLIMA | SCATTERED SPIDER, FAMOUS CHOLLIMA Victim: Various Organizations | Various Organizations
Key Point :
Adversaries leverage compromised credentials to infiltrate organizations, moving laterally and evading detection.…Cyber Security Career Skills Summary
Short SummaryThe video discusses essential skills for starting a career in cyber security, highlighting a shift towards skill-based hiring and highlighting the importance of specific competencies necessary for aspiring professionals in the field.
Key Points **Skill-based hiring**: The White House’s national cyber director is promoting skill-based hiring to create pathways for new talent in cyber security.…Summary :
This article discusses an intrusion involving Amazon Simple Email Service (SES) where an attacker exploited an external AWS account to persist in the victim’s environment, utilizing various techniques for evasion and privilege escalation. #AWS #CyberSecurity #EmailPhishing
Keypoints :
The attacker used a controlled AWS account to persist in the victim’s environment.…Summary :
YARA is a powerful tool for malware detection and classification, extensively used by Sekoia.io’s Threat Detection and Research team. The integration of YARA into their workflows enhances threat hunting and malware analysis, and the release of their YARA rules on GitHub fosters community collaboration.…
Interview Summary
Cybersecurity Career Insights: Interview SummaryThe video discusses an interview with Josh Mador, focusing on his journey into cybersecurity and the dynamic nature of the field. He reflects on his previous experiences in IT, the importance of practical skills, and the evolving landscape of cybersecurity, especially with the advent of AI technologies.…
Summary: Silent Push, a cybersecurity intelligence firm, has successfully raised $10M in Series A funding to enhance its global presence and market strategies. The company specializes in real-time threat detection through its innovative Indicators of Future Attacks (IOFA) data.
Threat Actor: Silent Push | Silent Push Victim: Enterprises and Government Agencies | enterprises and government agencies
Key Point :
Raised $10M in Series A funding led by Ten Eleven Ventures and Stepstone Group.…### #AIinSecurity #StartupFunding #DetectionEngineering
Summary: System Two Security, a Palo Alto-based cybersecurity startup, has secured $7M in funding to enhance its AI-driven detection engineering capabilities. The investment will support team expansion and accelerate product development to improve detection speed and accuracy.
Threat Actor: System Two Security | System Two Security Victim: N/A | System Two Security
Key Point :
System Two Security raised $7M in funding led by Costanoa Ventures, with participation from notable investors.…Keypoints :
Cozy Bear is linked to the Russian SVR and targets government and private sectors for intelligence gathering.…Keypoints :
The healthcare sector is a primary target for data breaches, with average costs reaching $9.77 million in 2024.…### #BulletproofHosting #Proton66 #MaliciousInfrastructure
Summary: This report investigates the connections between the Russian autonomous systems PROSPERO and Proton66, highlighting their involvement in various cybercriminal activities, including malware distribution and phishing campaigns. The findings suggest a sophisticated network of bulletproof hosting services facilitating these malicious operations.
Threat Actor: Proton66 | Proton66 Victim: Various individuals and organizations | phishing victims
Key Point :
PROSPERO and Proton66 share similar network configurations and peering agreements, indicating a strong operational link.…Summary: Team AXON has identified an ongoing threat campaign named “VEILDrive,” which exploits Microsoft SaaS services for malicious activities, including a unique OneDrive-based Command & Control (C&C) method. The campaign is believed to originate from Russia and has prompted Team AXON to alert Microsoft and affected organizations to mitigate further risks.…