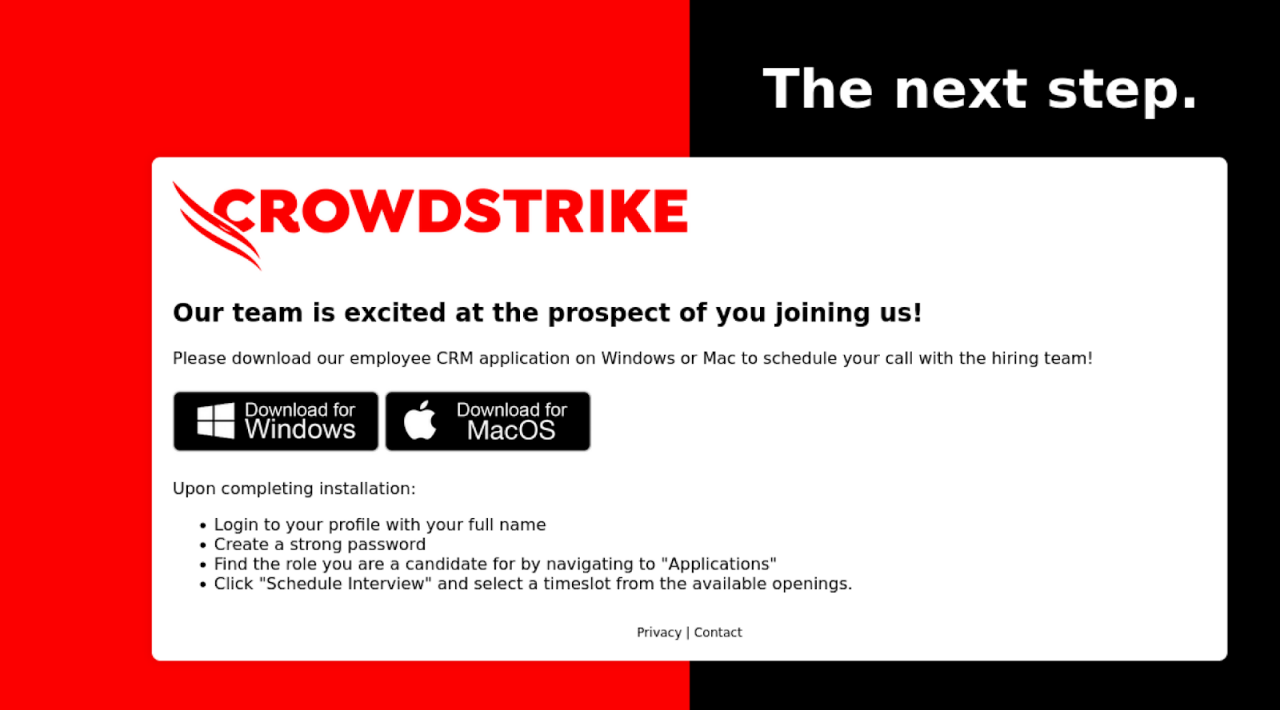
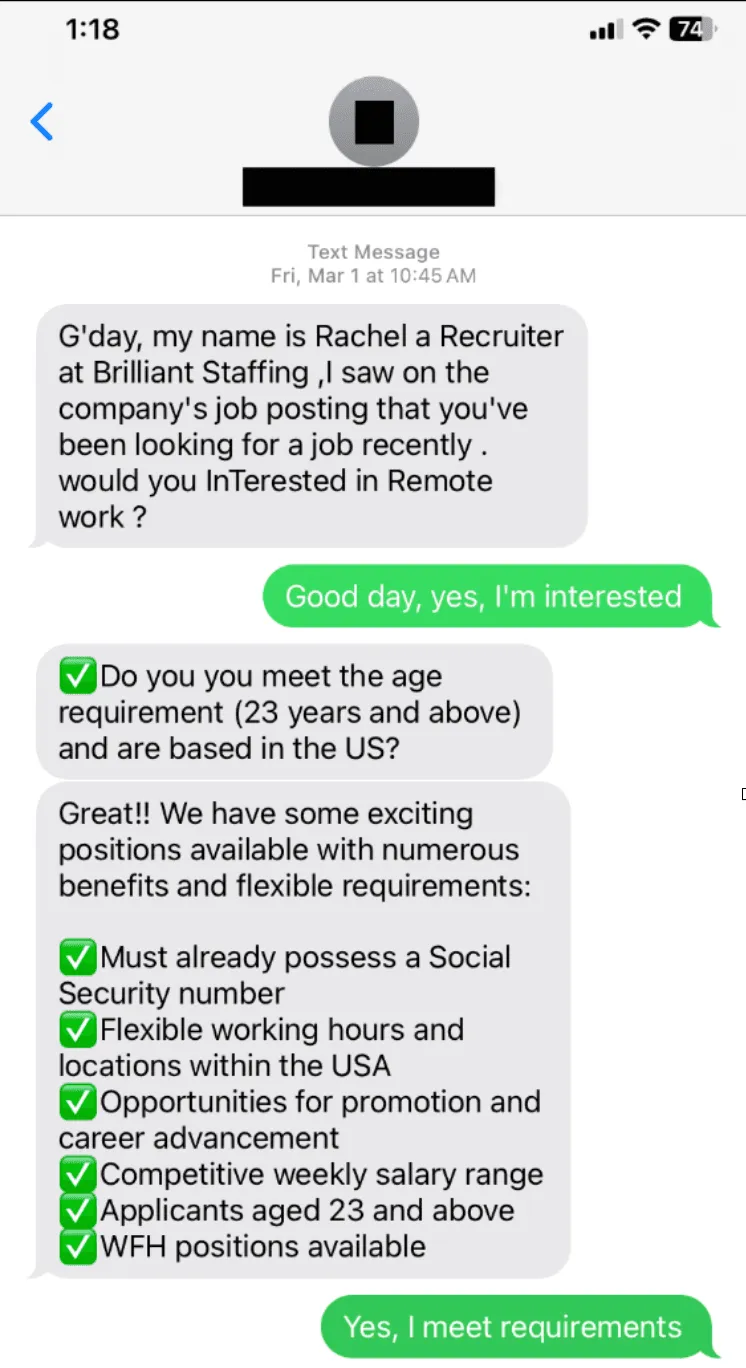
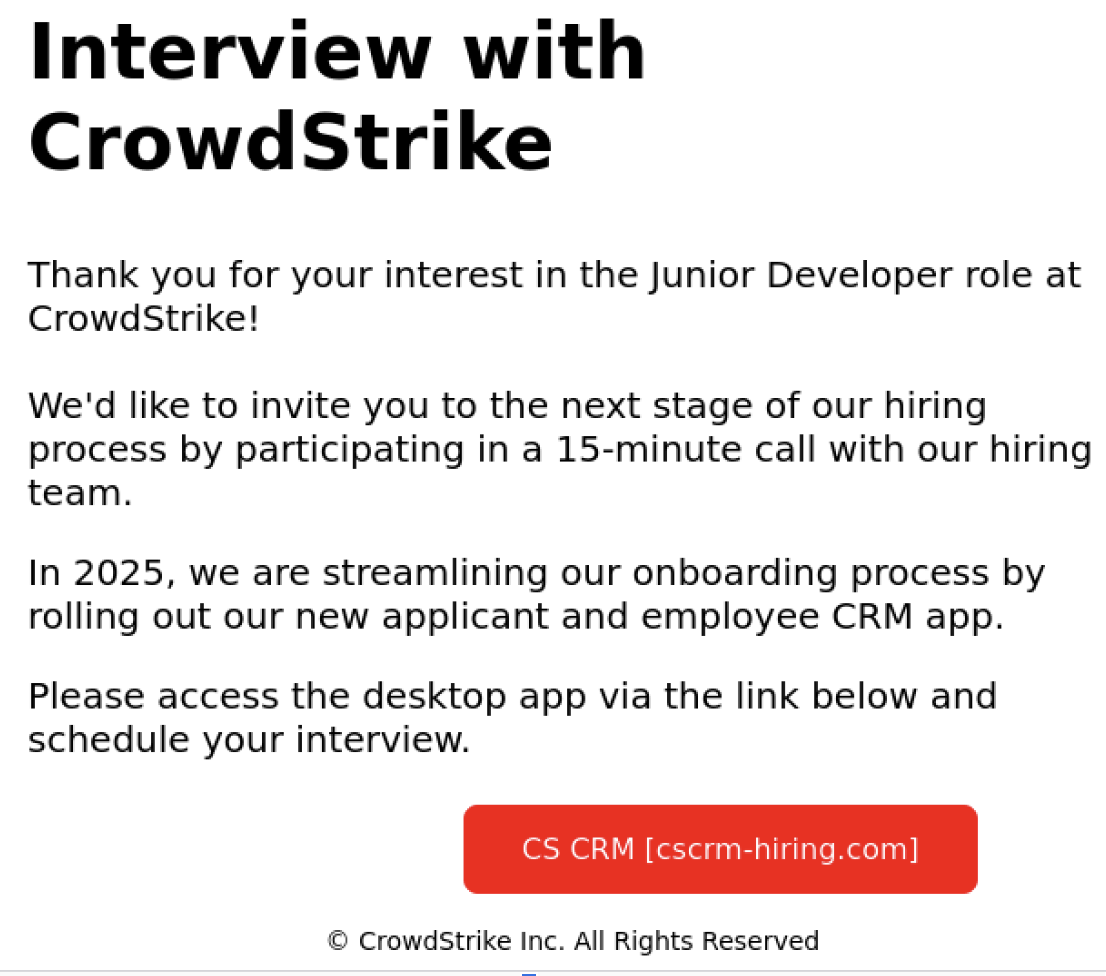
Summary: Cybercriminals are exploiting Google search advertisements to promote phishing sites that impersonate Google Ads, tricking users into revealing their credentials. These fake ads lead victims to counterfeit login pages hosted on Google Sites, which closely mimic the official Google Ads interface. The attackers, operating from various regions, aim to steal accounts for resale and further malicious activities.…
Read More




![THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [13 January] THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [13 January]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh-GVBzJbXbnB628INcZeeGpxnFqxVpcaOaQnUH-g2FpiUGHCsUnPnPNYeuEKDvxOqHzeiB2fZWoNTOO81_P4b77zyyyuaSpWTBjahKirJJMtMXCEIvVUiqsIojlnyGL9pPkB8Dv5-wviS5poLJ_CIYdbkSxjPE4Psyh6mppkjg0M4rWF22fNSR9IgRUqwh/s728-rw-e365/recap.png)