Threat Actor: Unknown | unknown Victim: CrowdStrike | CrowdStrike
Key Point :
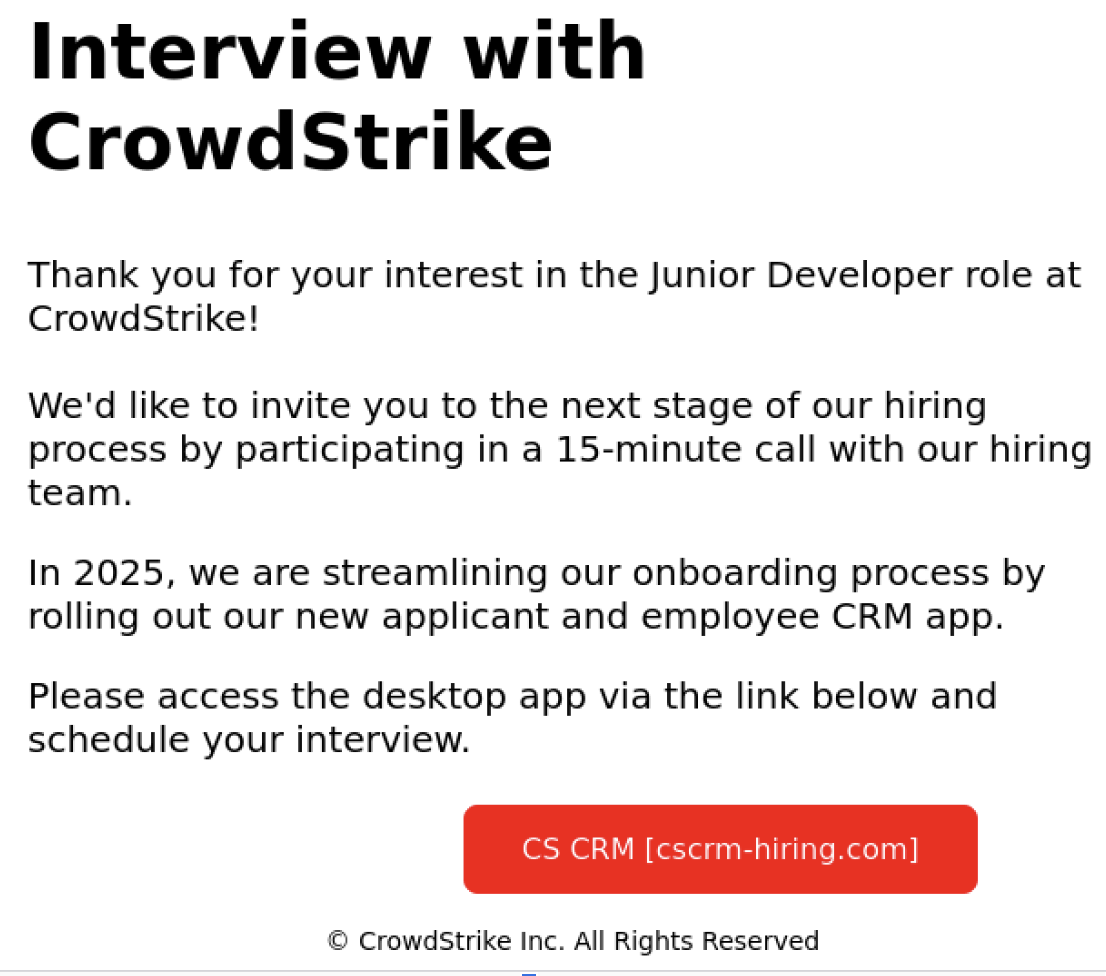
The phishing email claims recipients have been shortlisted for a junior developer role, prompting them to download a malicious CRM tool.…
Threat Actor: Unknown | unknown Victim: CrowdStrike | CrowdStrike
Key Point :
The phishing email claims recipients have been shortlisted for a junior developer role, prompting them to download a malicious CRM tool.…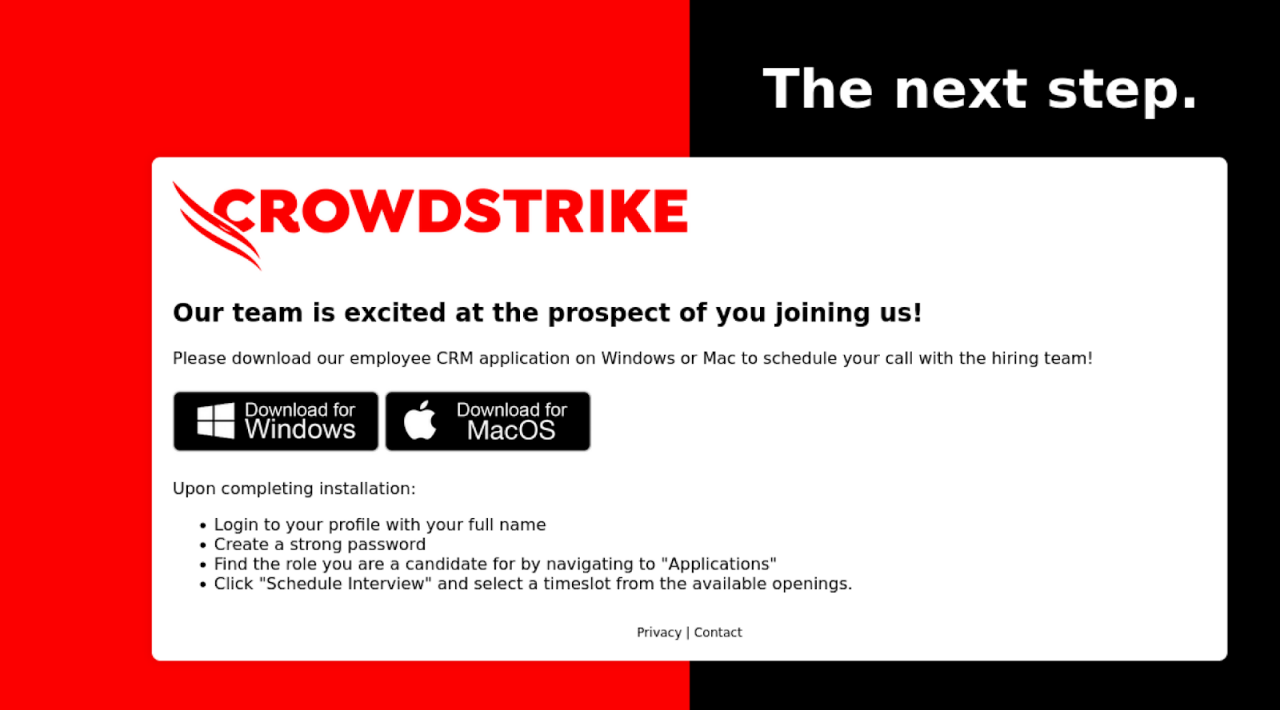
Threat Actor: Unknown | unknown Victim: Job seekers | job seekers
Key Point :
The phishing email mimics CrowdStrike’s recruitment process to lure victims.…
Keypoints :
Ivanti disclosed two high-severity vulnerabilities (CVE-2025–0282, CVE-2025–0283) affecting its products.…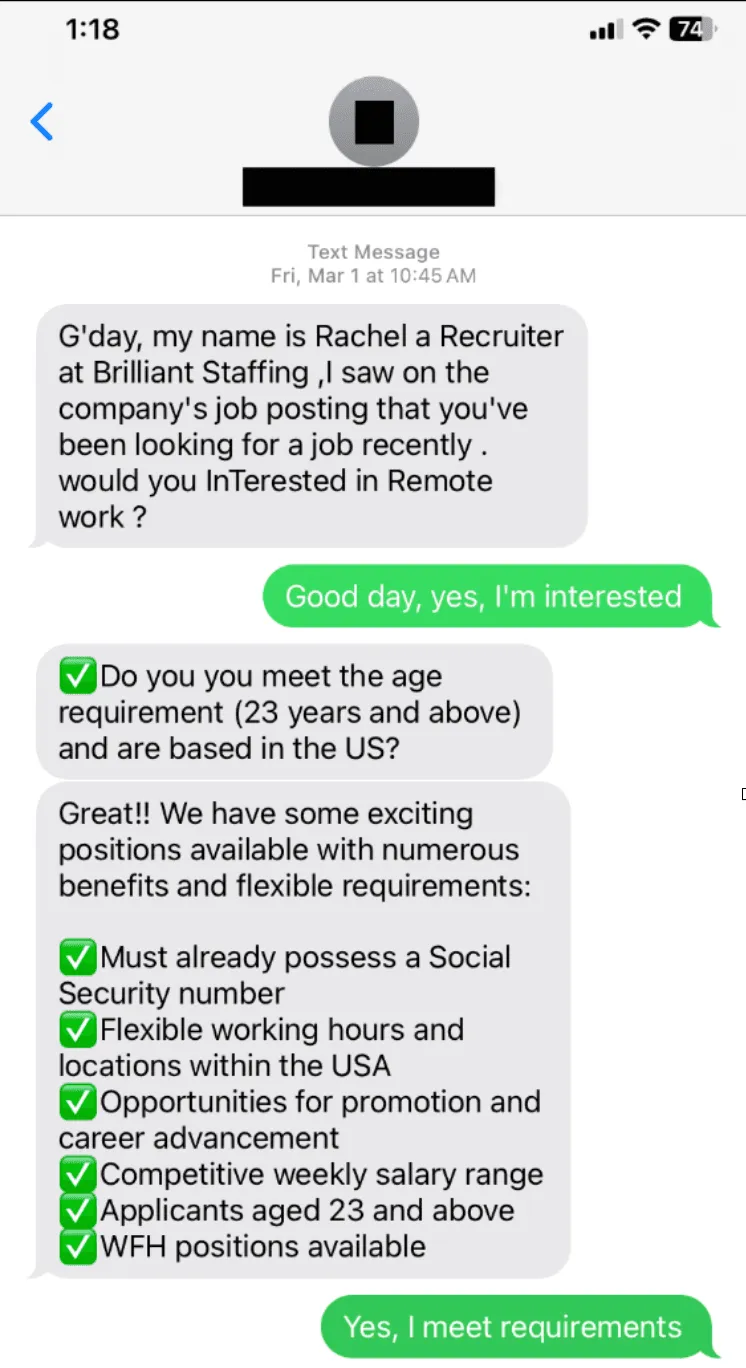

“`html
Check Point Research has identified a new version of the Banshee macOS stealer malware, which has been evading detection since September 2024. The malware targets macOS users, stealing sensitive information and utilizing an encryption algorithm similar to Apple’s XProtect. Despite the shutdown of its original operations after a code leak, Banshee continues to be distributed through phishing websites and malicious GitHub repositories.…

Threat Actor: Unknown | unknown Victim: Individuals using PayPal | PayPal
Key Point :
The phishing email appears legitimate, with a valid sender address and genuine-looking URL.…


Threat Actor: Muddling Meerkat | Muddling Meerkat Victim: Various sectors including legal, government, and construction | Various sectors
Key Point :
Threat actors are using old, neglected domains to spoof sender addresses and evade security checks.…

Keypoints :
BARWM is a new backdoor attack method targeting deep learning models on mobile devices.…
Threat Actor: Wallet Drainers | wallet drainers Victim: Crypto Users | crypto users
Key Point :
Victims lost approximately $494 million from wallet drainers in 2024, a 67% increase from the previous year.…Threat Actor: ShinyHunters | ShinyHunters Victim: Snowflake | Snowflake
Key Point :
ShinyHunters exploited a misconfiguration to breach over 165 organizations, emphasizing the importance of proper security measures.…Threat Actor: Flax Typhoon (Chinese state-sponsored) | Flax Typhoon Victim: Cyberhaven | Cyberhaven
Key Point :
Dozens of Google Chrome extensions were found stealing sensitive data from 2.6 million devices.…Threat Actor: Scammers | scammers Victim: Cryptocurrency Users | cryptocurrency users
Key Point :
Scammers stole $494 million from over 300,000 wallet addresses, marking a 67% increase from 2023.…