Victim: La Uni,ón
Country :
Actor: lynx
Source: http://lynxch2k5xi35j7hlbmwl7d6u2oz4vp2wqp6qkwol624cod3d6iqiyqd.onion/leaks/67c5a77d44fac8dca191bfd4
Discovered: 2025-03-03 13:27:56.197850
Published: 2025-03-03 12:58:37.705000
Description :La Unión is a Spanish company.
Specializes in production and sale of fruits and vegetables.
Collaborates with 3,500 family farms.
Provides employment for 15,000 people.
Controls the entire process from field to consumer’s table.…
Read More Tag: RUSSIA

Summary: In 2024, global ransomware attacks surged to 5,414 incidents, marking an 11% increase from the previous year, with a notable spike in attacks during Q2 and Q4. The emergence of 46 new ransomware groups, especially RansomHub, has significantly transformed the ransomware landscape, with these groups adopting aggressive strategies and collaborations.…
Read More 
This study offers a comprehensive examination of Advanced Persistent Threats (APTs), focusing on their dynamics, techniques employed, and preventive measures. The article discusses the identification of APTs, the reasons behind attacks on Turkey, and their geopolitical and economic impacts. Furthermore, it explains the concept of Tactics, Techniques, and Procedures (TTP), their subdivision into sub-techniques, and details effective strategies to mitigate APT attacks.…
Read More 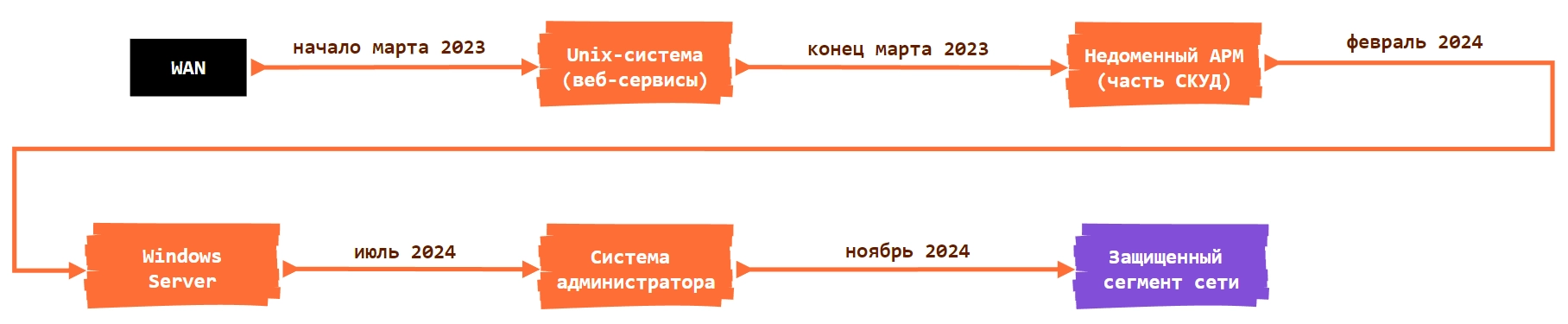
In November 2024, Solar 4RAYS reported on a malicious campaign targeting Russian IT organizations providing services for the public sector. The group, dubbed Erudite Mogwai by Solar 4RAYS and Space Pirates by Positive Technologies, is utilizing a modified version of the public proxy tool Stowaway. This custom tool, used alongside other malware like ShadowPad Light, demonstrated enhancements and adaptions for unauthorized access against sensitive networks.…
Read More 
The December 2024 phishing attack against Ukraine’s military, attributed to the cyber group UAC-0185 (UNC4221), exemplifies ongoing cyber warfare amid the Russia-Ukraine conflict. By masquerading as legitimate conference invitations, attackers aimed to acquire sensitive credentials using common remote access tools. The incident underscores the importance of vigilance against phishing threats.…
Read More 
In 2024, Insikt Group expanded its monitoring of malicious infrastructure, particularly focusing on malware families and infrastructure types. Key trends included the rise of malware-as-a-service infostealers, with significant activity from LummaC2, and persistent targeting of Android for mobile malware. State-sponsored groups from China and Russia adapted their tactics, leveraging legitimate internet services to enhance cybercrime efforts.…
Read More 
Summary: A US Army soldier, Cameron John Wagenius, arrested for unlawfully transferring confidential records, indicated plans to plead guilty in court. He infiltrated telecommunications firms to publish sensitive information about high-ranking officials on the Dark Web and has been accused of extortion and other cybercrimes. The prosecution considers him a flight risk due to his alleged attempts to defect and sell hacked information to foreign entities.…
Read More 
Summary: Defense Secretary Pete Hegseth has ordered U.S. Cyber Command to halt all planning and offensive actions against Russia, indicating a shift in U.S. policy to normalize relations with Moscow amidst ongoing global tensions. This directive does not affect the National Security Agency’s work targeting Russia, and its full implications for personnel and operations are still being evaluated.…
Read More 
Summary: In a recent interview on the Click Here podcast, Anne Neuberger discusses the implications of artificial intelligence in cybersecurity and military strategy, highlighting the evolving role of AI in both offensive and defensive operations. She emphasizes the importance of data and innovation in the U.S.-China…
Read More 
Summary: The German government has refuted claims by a member of the Bundestag intelligence committee that foreign actors successfully manipulated the recent federal election. Despite acknowledging attempts at influence, officials emphasized the integrity of the electoral process and cited minimal reach of such interventions. The debate continues regarding the measurement of influence operations’ effectiveness in democratic processes.…
Read More 
Summary: Director of National Intelligence Tulsi Gabbard expressed grave concerns over the British government’s demand for Apple to provide backdoor access to encrypted data. Gabbard emphasized that this would violate Americans’ privacy and civil liberties and has called for further examination of the issue by U.S.…
Read More 
Summary: Microsoft has unveiled four individuals involved in a cybercrime network, known as Storm-2139, that exploited unauthorized access to Azure’s generative AI services for harmful activities, including creating illicit content. The campaign, referred to as LLMjacking, encompasses a broader network of individuals engaged in modifying and reselling access to these malicious AI tools.…
Read More 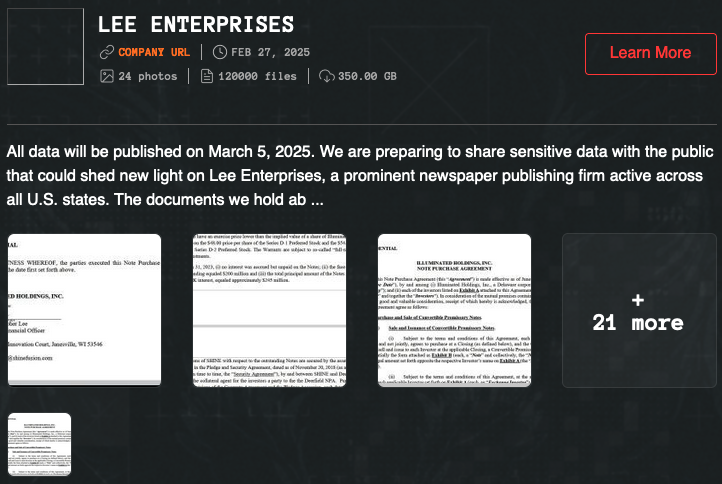
Summary: A ransomware attack by the Qilin group has disrupted operations at Lee Enterprises, affecting at least 75 local newspapers in the U.S. The attackers have exfiltrated sensitive data and are demanding a ransom, threatening to leak the stolen information if their demands are not met by March 5.…
Read More 
Summary: The threat actor group Sticky Werewolf is conducting targeted attacks in Russia and Belarus aimed at delivering Lumma Stealer malware through a new implant. Known as Angry Likho by Kaspersky, these attacks utilize phishing tactics and sophisticated evasion techniques to compromise organizations, particularly targeting government employees and contractors.…
Read More 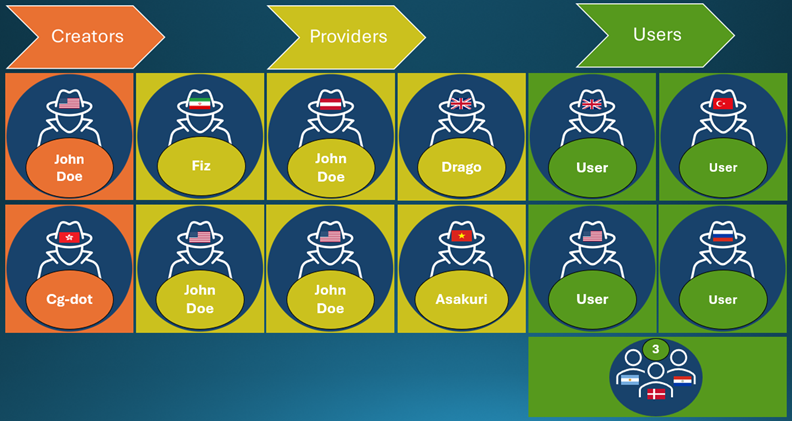
Summary: Microsoft has revealed the identities of four individuals allegedly linked to a network named Storm-2139, involved in exploiting AI services for malicious purposes. The lawsuit targets those who develop and distribute tools that manipulate generative AI, primarily to create harmful content like deepfakes. Microsoft is also working with international law enforcement to combat this cybercrime operation.…
Read More Victim: FFL-GROUP.COM
Country : RU
Actor: clop
Source:
Discovered: 2025-02-27 17:58:11.158464
Published: 2025-02-27 17:58:05.319989
Description :Global investment company with a focus on trading, e-commerce, and venture capitalism.
Diversified operations across various markets to achieve strategic goals.
Houses multiple businesses in sectors such as healthcare, technology, retail, and manufacturing.…
Read More 
The research examines the evolution of hacktivism, particularly the emergence of state-sponsored groups masquerading as independent hacktivists. By leveraging machine learning and linguistic analysis, the study aims to enhance attribution methods for hacktivist operations, uncovering their motivations and connections over time. The findings highlight a shift in hacktivist tactics, employing increasingly sophisticated methods for political and social influence.…
Read More Victim: FASHION.PRI
Country : RU
Actor: clop
Source:
Discovered: 2025-02-27 18:01:44.621237
Published: 2025-02-27 18:01:37.801855
Description :Digital platform specializing in fashion apparel and accessories.
Offers a wide range of trendy products including clothes, shoes, handbags, and jewelry.
Caters to both men and women.
Mission focused on providing high-quality fashion at competitive prices.…
Read More 
Summary: Privacy-focused email provider Tuta and the VPN Trust Initiative are voicing concerns over proposed French laws that would impose backdoors in encrypted communication systems and restrict VPN access to pirate sites. The amendments, supported by law enforcement, threaten user privacy and security, with potential legal conflicts against European GDPR and Germany’s IT security regulations.…
Read More 
Summary: The Philippine Army has confirmed a cyberattack by a local hacking group known as Exodus Security, which claims to have accessed confidential military documents. Although the army swiftly contained the incident with no reported data theft, the breach raises serious concerns about cybersecurity and potential threats from foreign state-sponsored actors.…
Read More