In recent months, state-sponsored actors from North Korea, Iran, and Russia have begun utilizing the ClickFix social engineering technique, which has primarily been associated with cybercriminals. This shift indicates a potential evolution in espionage tactics, as traditional campaigns are being augmented with innovative methods. The use of ClickFix represents a growing trend where cybercriminal techniques are adopted by state actors for espionage activities.…
Read More Tag: RUSSIA

This article discusses a malicious campaign by a threat actor named “Desert Dexter,” which targets victims in the Middle East and North Africa through fake news posts on social media to distribute a modified version of AsyncRAT malware. Approximately 900 victims have been identified, with a focus on countries like Egypt, Libya, and Saudi Arabia.…
Read More 
This article discusses the malicious use of a subscription service called Crypters And Tools, enabling cybercriminals to generate malware loaders. Various hacker groups, including PhaseShifters, TA558, and Blind Eagle, utilize this service to conduct cyber attacks on organizations worldwide, primarily through phishing emails and malicious scripts.…
Read More 
Summary: A complex multi-stage attack has been seen delivering malware such as Agent Tesla variants and Remcos RAT using a deceptive email tactic. The attack employs various methods for payload delivery and execution, including PowerShell scripts and encoded files, further complicating detection efforts. Concurrently, a new version of MysterySnail RAT is being utilized by a Chinese-speaking threat actor named IronHusky to target government organizations in Mongolia and Russia.…
Read More 
Summary: Chinese-speaking IronHusky hackers are employing an upgraded version of the MysterySnail remote access trojan (RAT) to target Russian and Mongolian government organizations. This new variant, named MysteryMonoSnail, facilitates advanced control over compromised devices via a malicious script disguised as a Word document, allowing attackers to manage files and processes effectively.…
Read More 
Summary: A deep-dive analysis by HarfangLab reveals new insights into Gamaredon, a Russian cyberespionage group, focusing on their use of PteroLNK, a stealthy VBScript malware. The report outlines how Gamaredon utilizes obfuscation, deceptive shortcut files, and intricate persistence mechanisms to evade detection and maintain access to Ukrainian systems.…
Read More 
Summary: Kaspersky’s Global Research and Analysis Team has reported the resurgence of the IronHusky APT group, which is targeting Russia and Mongolia with a new version of the MysterySnail RAT. This new implant takes advantage of previously known vulnerabilities and uses sophisticated evasion techniques. Despite being relatively quiet since 2021, the group has been observed using a modular architecture for their attacks, indicating ongoing operations.…
Read More 
Summary: A Windows vulnerability, CVE-2025-24054, is being actively exploited in phishing campaigns to capture NTLM hashes from users in government and private sectors. The exploit uses .library-ms files to trigger SMB connections that allow attackers to capture NTLM hashes with minimal user interaction. Organizations are urged to apply the March 2025 updates and consider disabling NTLM authentication due to the severe implications of this flaw.…
Read More 
Iran is prioritizing the development of artificial intelligence (AI) to enhance its economic viability, security, and regional influence, despite facing challenges due to economic isolation and government oversight. The government’s top-down strategy includes leveraging AI for national security purposes, cyber operations, and social control, while initiatives aim to create a robust AI ecosystem.…
Read More 
The MysterySnail RAT, linked to the IronHusky APT threat actor, has resurfaced after years of inactivity. Initially discovered in 2021, recent reports show its deployment in government organizations in Mongolia and Russia, alongside a new variant called MysteryMonoSnail that has a more simplified architecture. The article emphasizes the importance of monitoring and detecting historical malware threats, as they may still be active despite the lack of public reports.…
Read More 
Summary: Two U.S. senators have proposed the Cybersecurity Information Sharing Extension Act to extend the provisions of the Cybersecurity Information Sharing Act of 2015 for another decade, promoting private sector and government collaboration against cyber threats. The bill provides legal protections for businesses that share cybersecurity threat information with the Department of Homeland Security.…
Read More 
Summary: Various state-sponsored hacking groups from Iran, North Korea, and Russia have adopted the ClickFix social engineering tactic to deploy malware in a series of phishing campaigns from late 2024 into early 2025. This approach has evolved from cybercrime applications to being utilized by nation-state actors, who manipulate targets into executing malicious commands under the guise of technical fixes.…
Read More 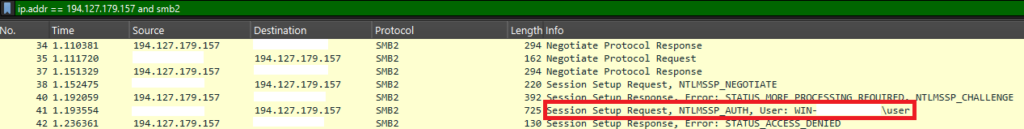
CVE-2025-24054 is a vulnerability that allows NTLM hash disclosure through spoofing methods, primarily via a malicious .library-ms file. Active exploits have targeted institutions in Poland and Romania, posing significant risk for password leakage and system compromise. Microsoft issued a patch on March 11, 2025, but attackers exploited the flaw just days later.…
Read More 
Summary: The hacktivist group Anonymous has released 10 terabytes of classified data in a cyberattack against Russia, claiming it is in defense of Ukraine. The leak includes sensitive information on Russian government officials, pro-Kremlin assets, and notable figures like Donald Trump, suggesting potential foreign influence ties.…
Read More 
Summary: APT29, also known as Midnight Blizzard or Cozy Bear, is executing a new wave of targeted phishing attacks against European governments and diplomats by impersonating legitimate entities. This campaign employs sophisticated malware including GRAPELOADER, which enhances evasion tactics and delivers payloads while updating previously known tools like WINELOADER.…
Read More 
Summary: A recent report by Resecurity reveals a significant rise in cyberattacks against the energy sector, driven by geopolitical conflicts and criminal activities. These attacks, which target various energy operators, include ransomware, espionage, hacktivism, and exploitation of IT vulnerabilities that threaten operational technology. The escalating threat landscape necessitates a heightened awareness and reinforced cybersecurity measures across the industry.…
Read More
Summary: A recent report by Cyble highlights the shift in hacktivist tactics towards advanced attacks targeting critical infrastructure and the integration of ransomware into politically motivated operations. This evolution demonstrates hacktivist groups adopting methods similar to those of nation-state actors, posing significant threats to national resilience.…
Read More
Summary: Check Point Research has raised an alarm over the exploitation of CVE-2025-24054, a vulnerability in Windows that leaks NTLMv2-SSP hashes through interaction with malicious .library-ms files. Despite Microsoft’s patch released on March 11, 2025, attackers rapidly weaponized the flaw, which allows hash disclosure with minimal user interaction.…
Read More 
Summary: A Chinese state-owned company, SDIC Intelligence Xiamen Information Co Ltd, is training police officers in Tibet on hacking and digital forensics, following a controversial contract. This initiative enhances local police’s surveillance capabilities against Tibetan dissidents and reflects larger trends in digital oppression. Human rights groups express concern over the implications for targeted surveillance and global digital threats.…
Read More 
This report discusses the ongoing threat posed by the Russian-nexus Gamaredon group, specifically their use of the Pterodo malware family, particularly through PteroLNK VBScript files. The report highlights the malware’s techniques, victimology, and the infrastructure used by Gamaredon, including Dead Drop Resolvers (DDRs). The findings indicate active operations targeting Ukrainian entities, predominantly government and military sectors, providing insights into their malware deployment strategies.…
Read More