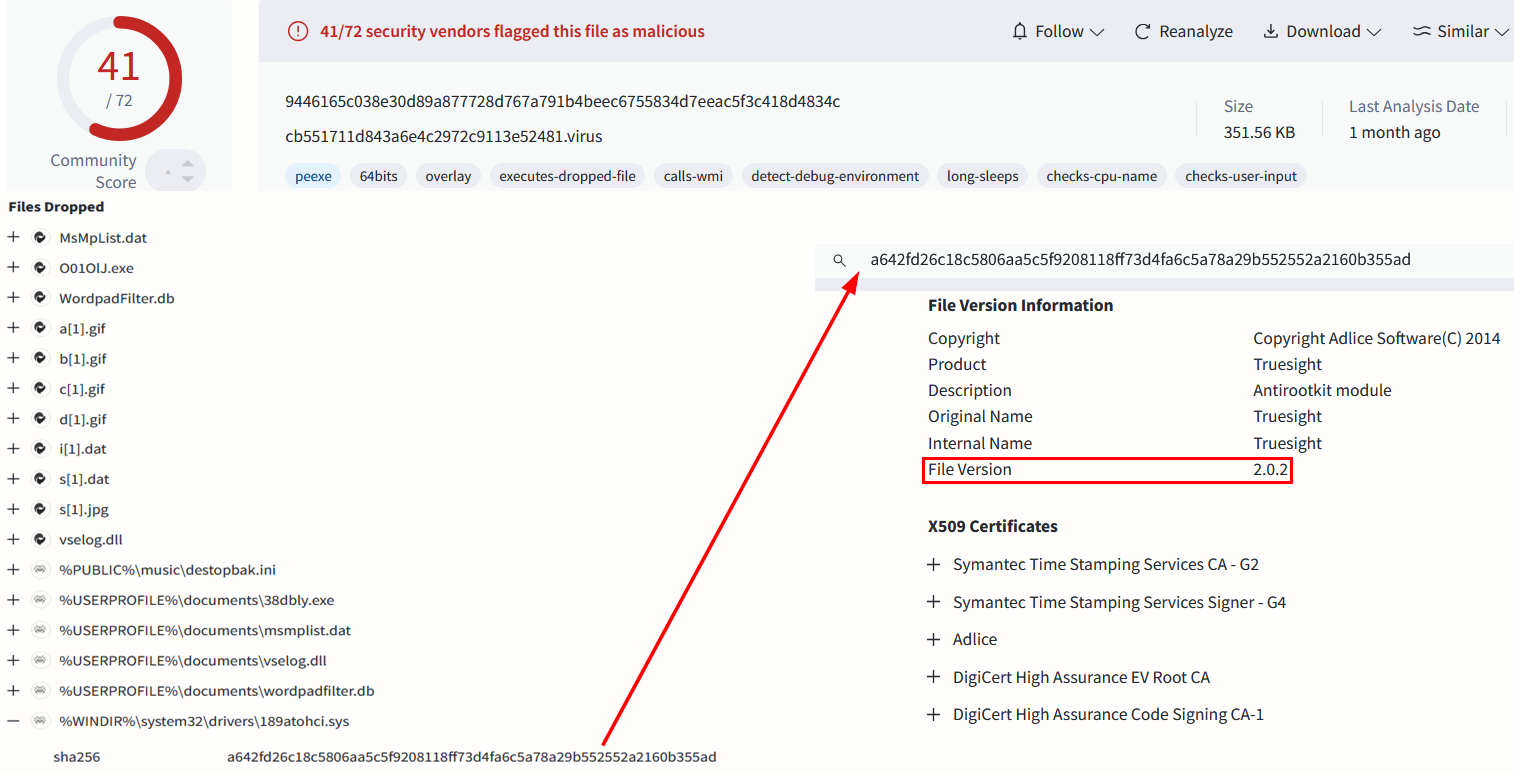
Summary: The article draws parallels between Groucho Marx’s humor and the importance of consistent security policies in the face of growing enterprise complexity. It highlights how recent technological advancements have made security policy implementation more challenging and emphasizes the need for reliable methods to enforce these policies.…
Read More