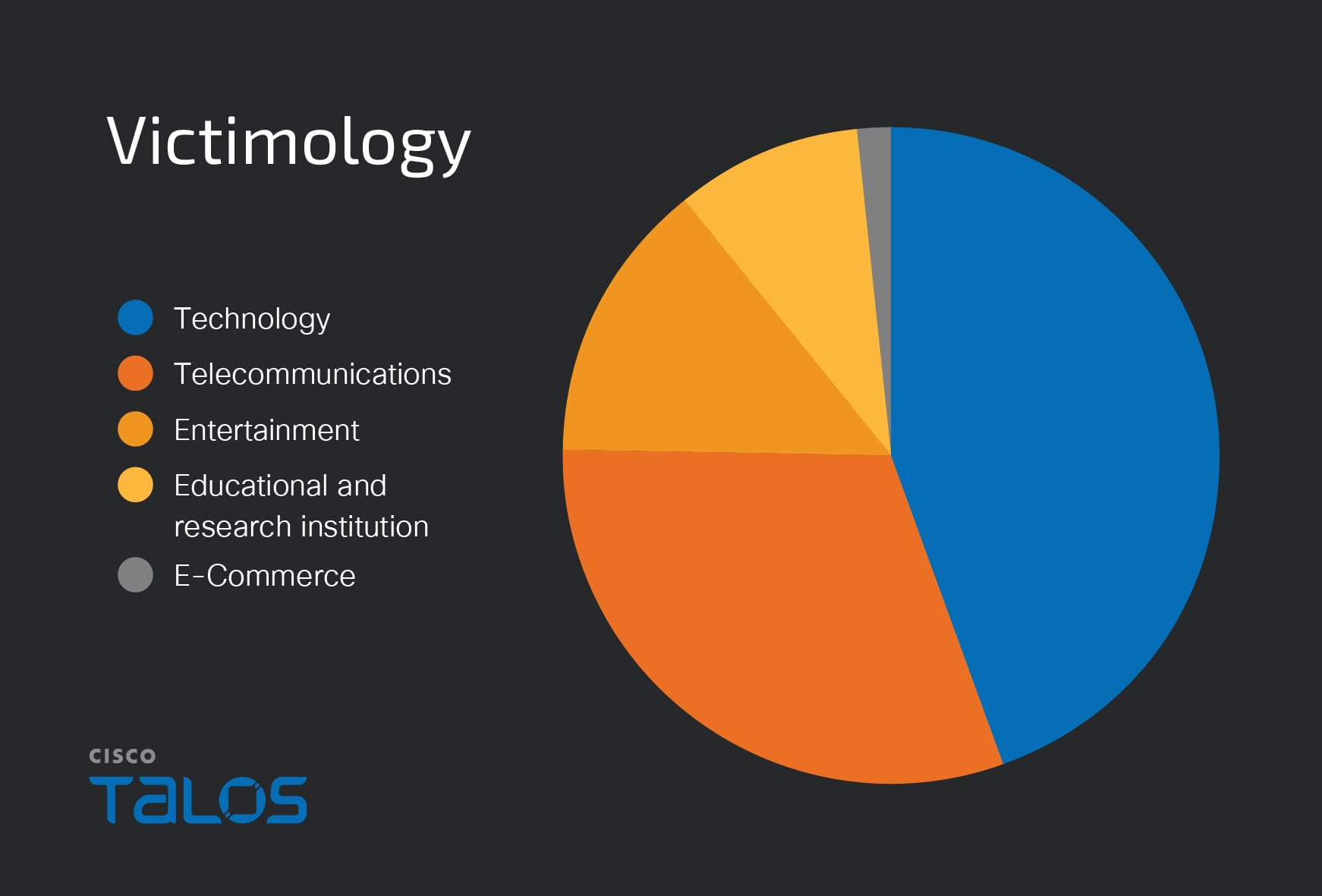
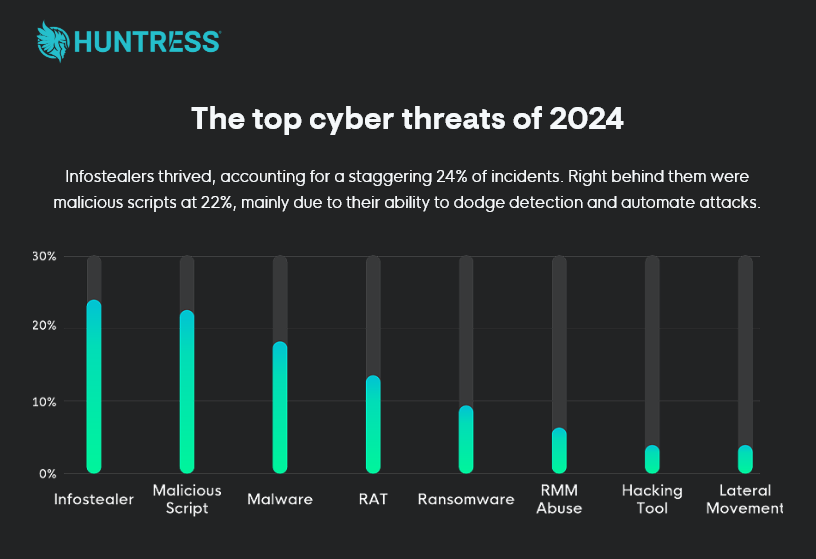
Summary: Safe{Wallet} disclosed details about a sophisticated cyberattack on Bybit, attributed to state-sponsored North Korean hackers. The attackers employed advanced social engineering techniques to compromise a developer’s machine and hijack AWS session tokens, enabling them to conduct covert operations. The incident highlights serious security vulnerabilities in the cryptocurrency industry, which faces record losses from hacks in 2025.…
Read More