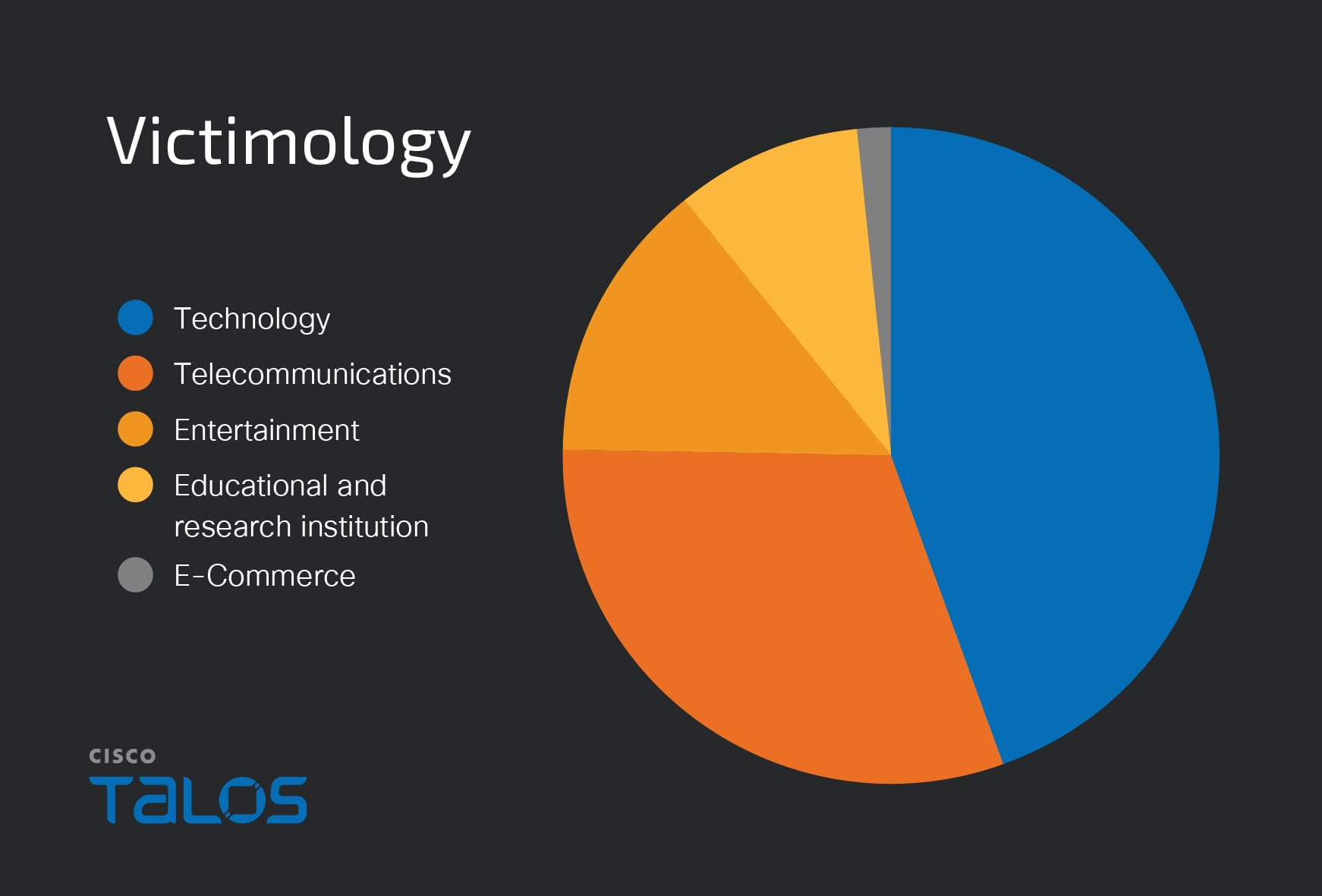
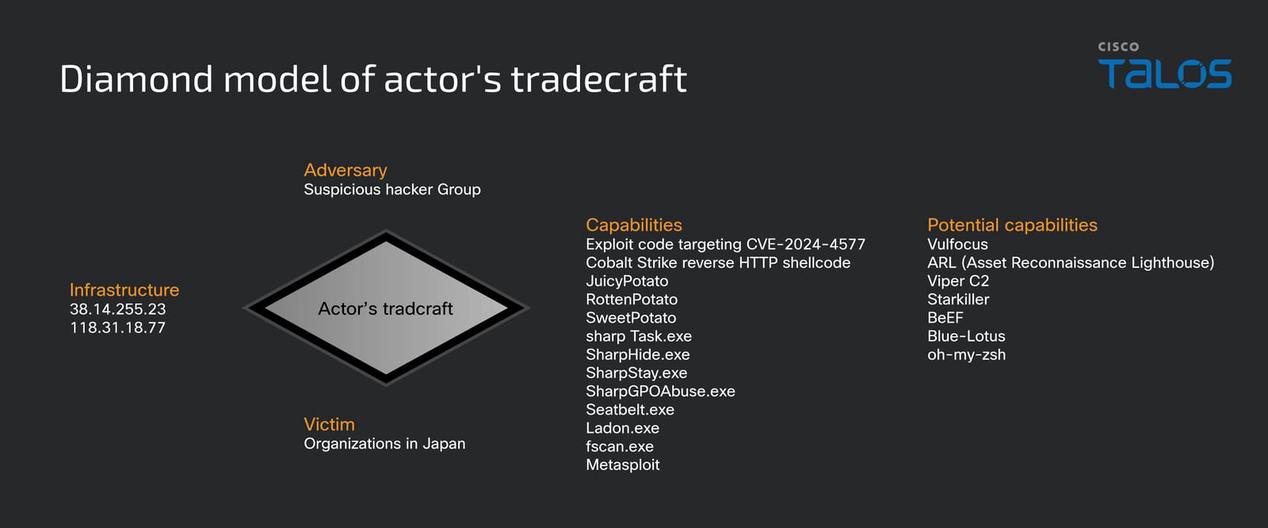
Summary: North Korean hackers known as APT37 or ScarCruft are utilizing advanced phishing techniques to deploy the RokRat remote access Trojan (RAT) by delivering malicious ZIP files containing disguised LNK files. These attacks exploit real information to enhance credibility and execute a multi-stage infection process that gathers system details and exfiltrates data using legitimate cloud services.…
Read More 


 Cyber Attack Chronicles
Cyber Attack Chronicles