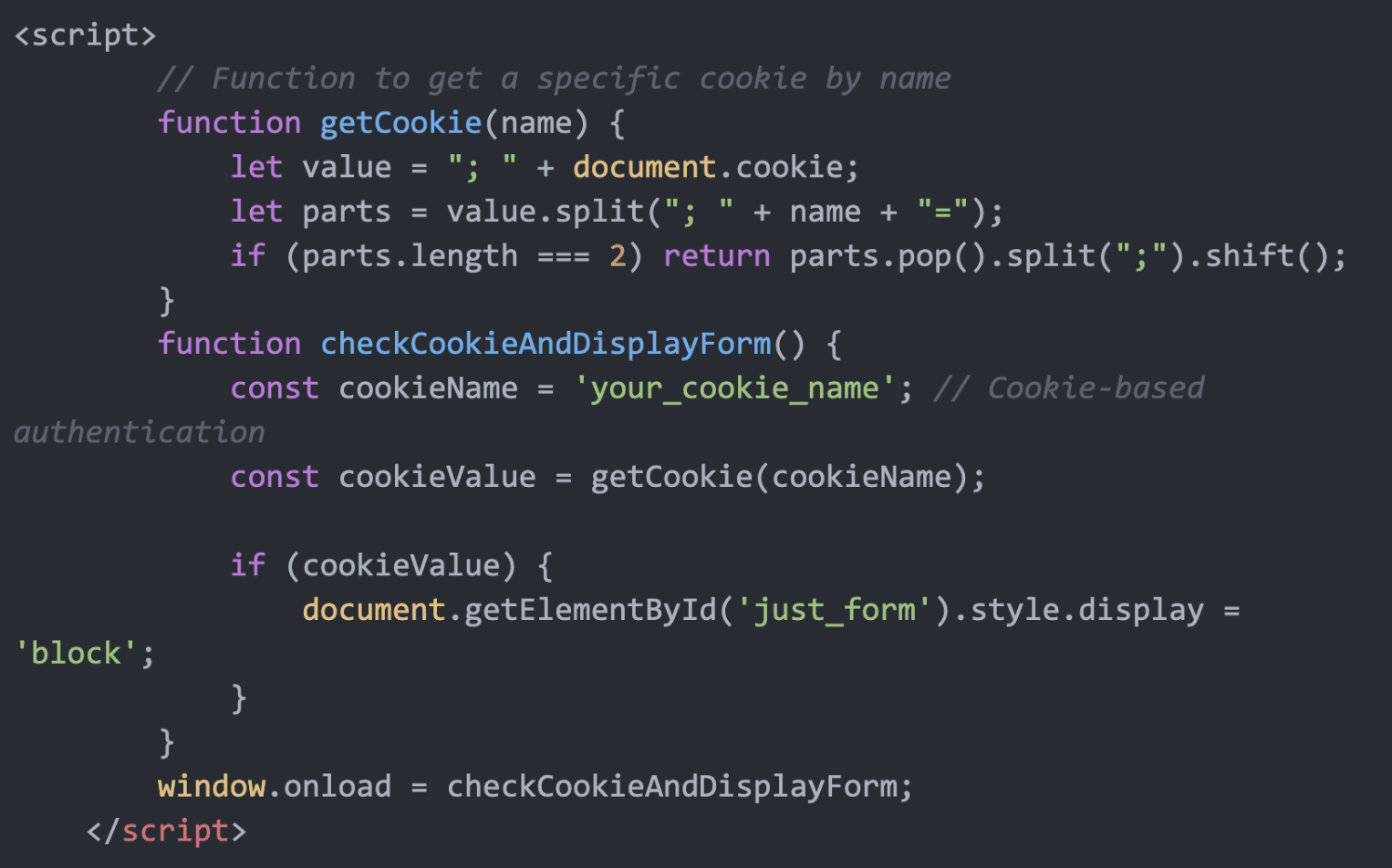
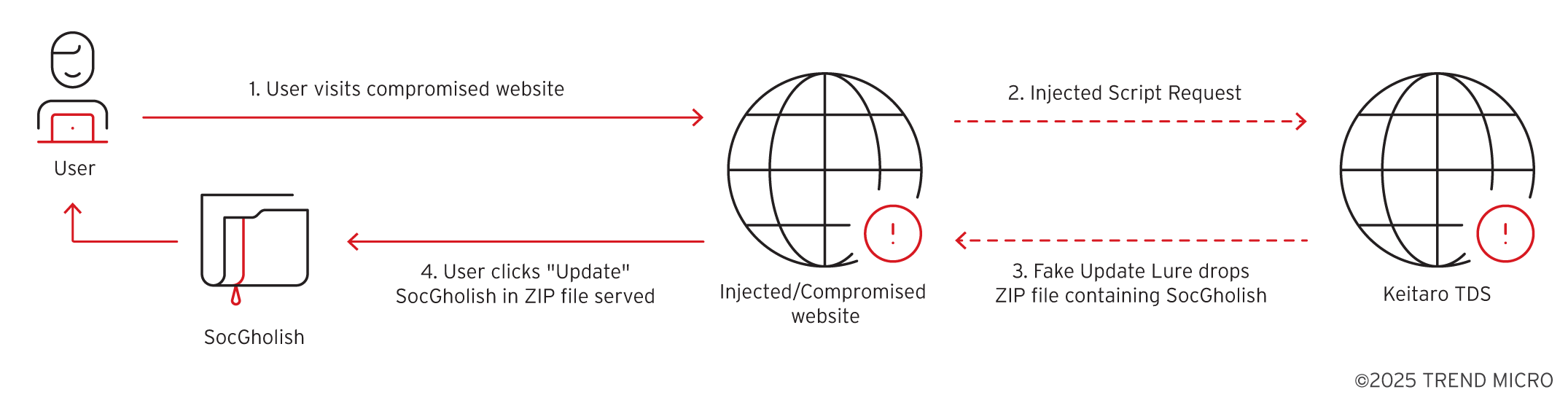
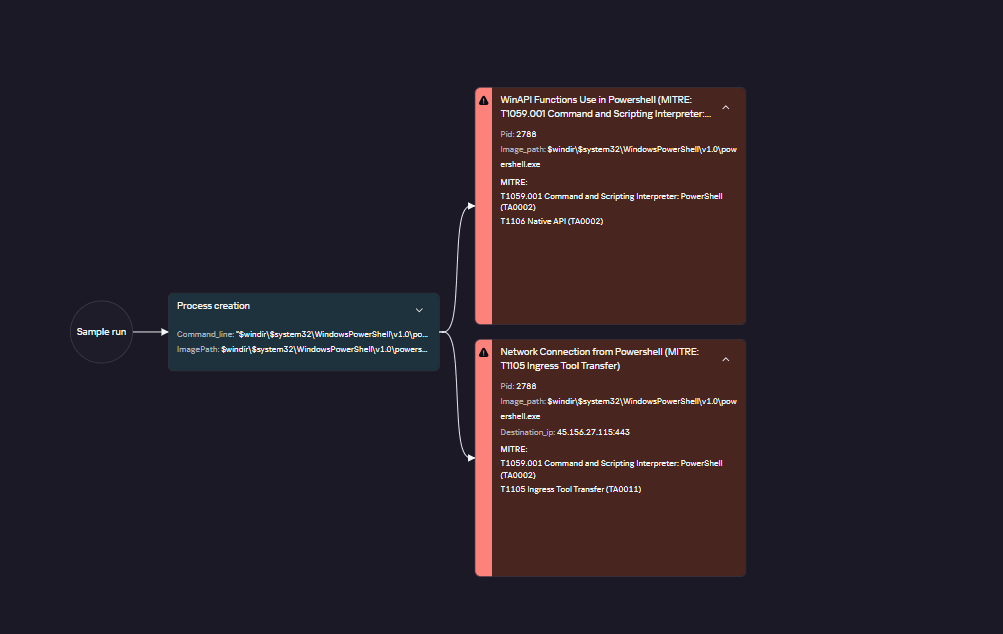
In November 2024, Microsoft Incident Response uncovered StilachiRAT, a remote access trojan that employs sophisticated evasion techniques and data exfiltration capabilities, targeting sensitive information such as credentials, digital wallet data, and clipboard contents. StilachiRAT establishes command-and-control connectivity with remote servers, and Microsoft has issued guidance to bolster defenses against this growing threat.…
Read More