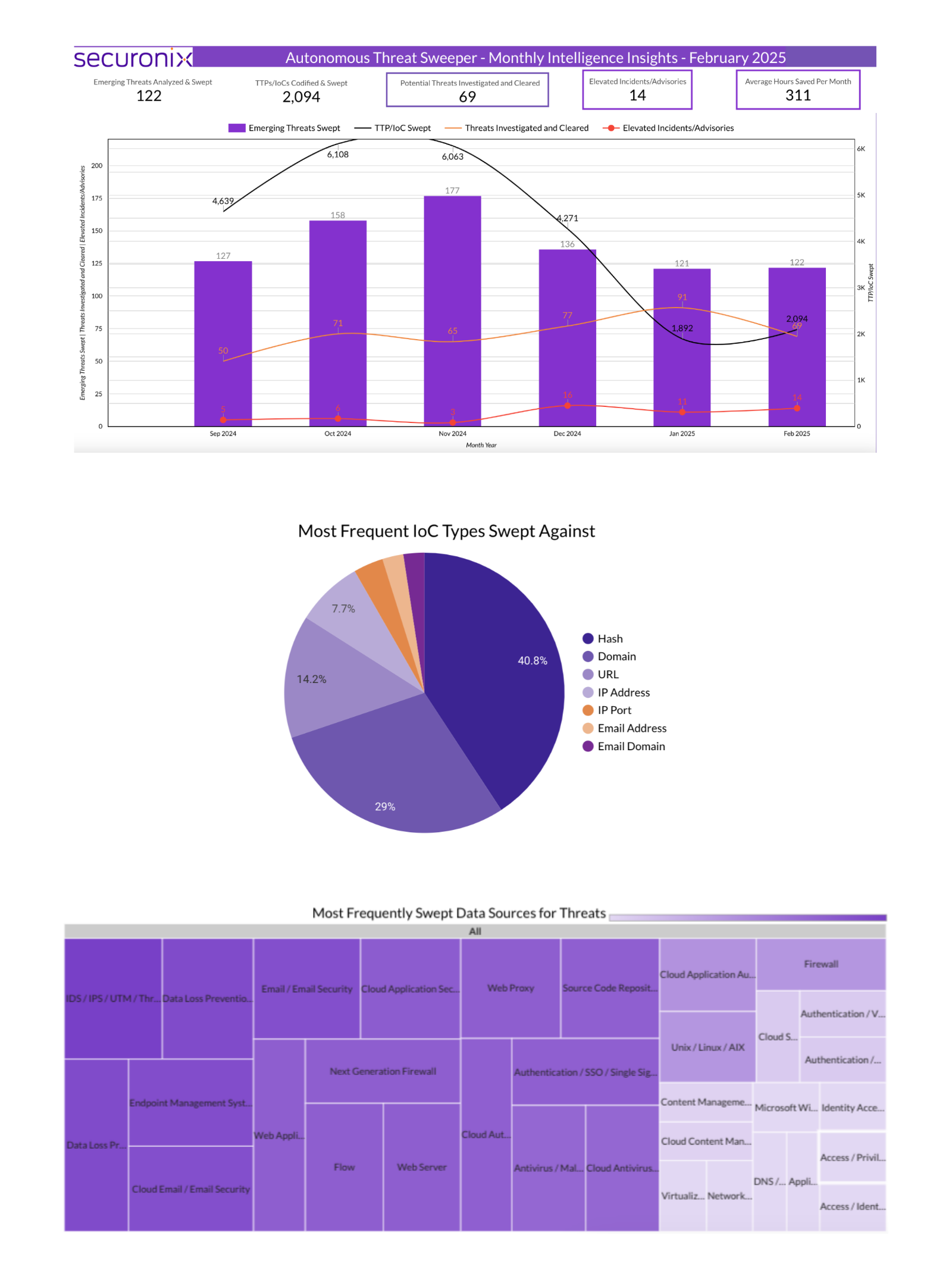
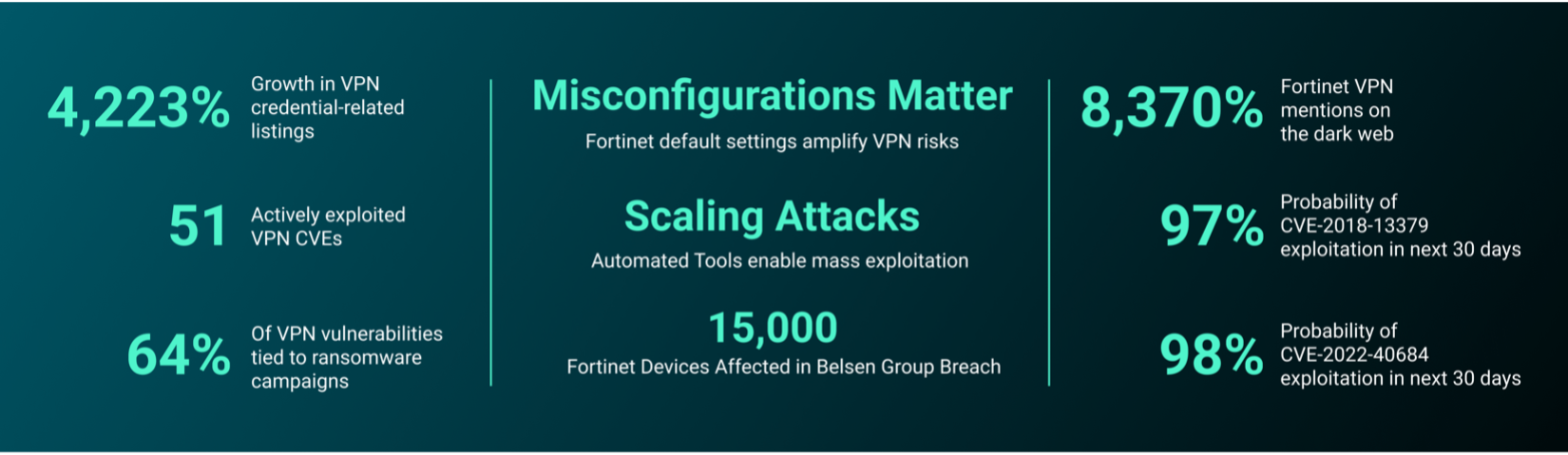
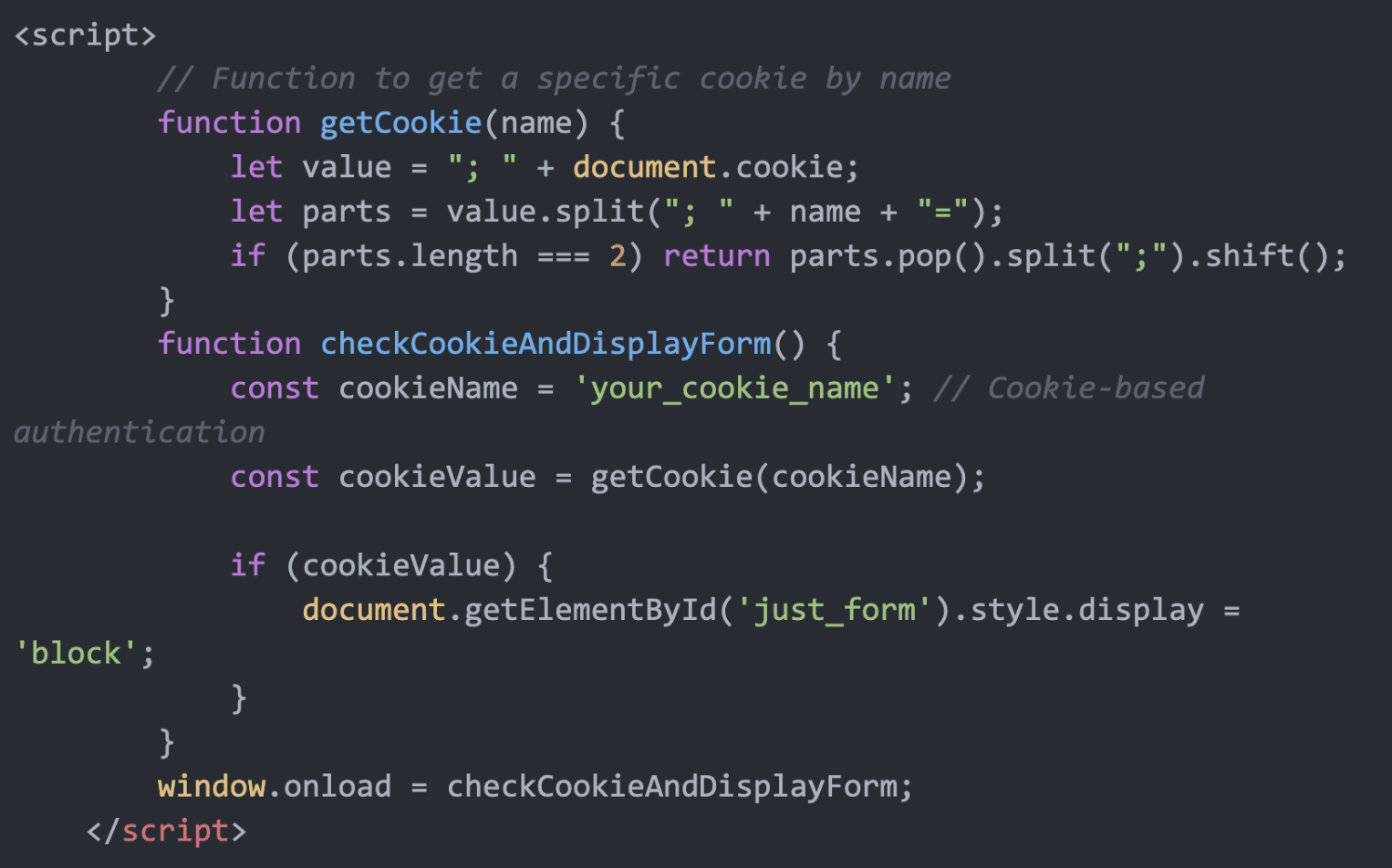
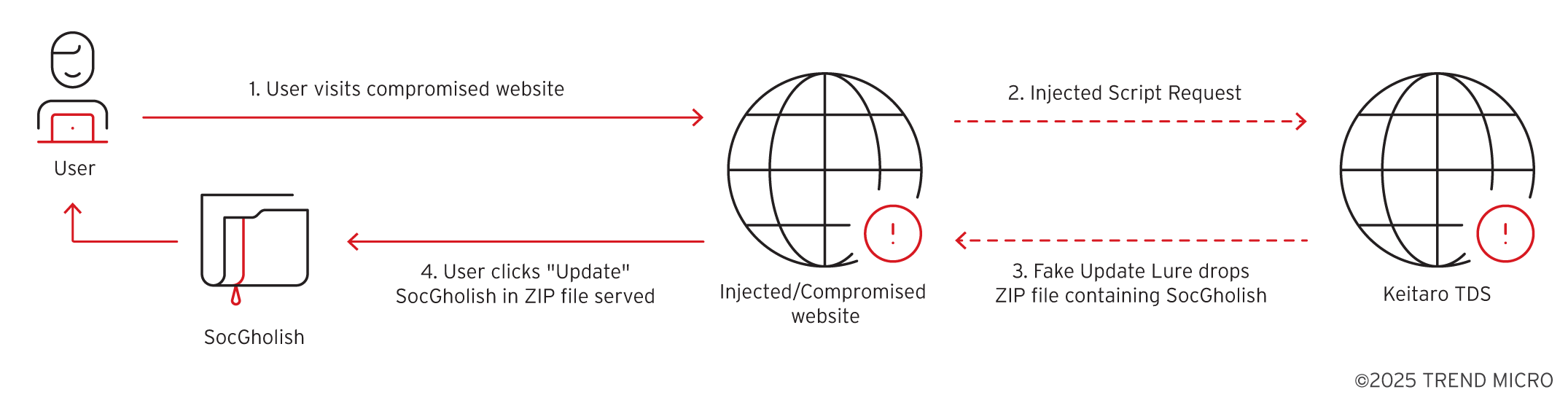
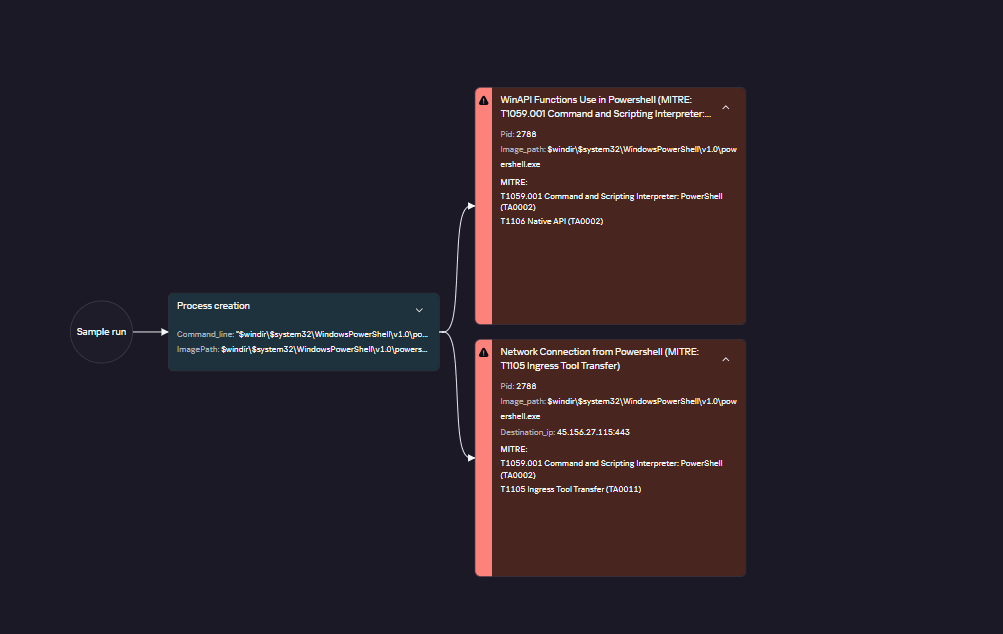
Summary: The Computer Emergency Response Team of Ukraine (CERT-UA) has identified a cyber espionage campaign targeting the defense sector with the Dark Crystal RAT. This campaign involves the distribution of malicious archived files via Signal, designed to look like legitimate communications. The report highlights the persistent threat posed by the DCRat malware, which has evolved since its first appearance in 2018, with modular capabilities for various malicious actions.…
Read More